Next Generation Security
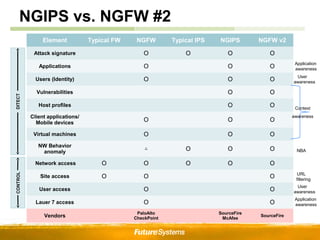
- Evolution of network security technologies from basic firewalls to next generation firewalls (NGFW) and next generation intrusion prevention systems (NGIPS) that provide advanced capabilities like application awareness, user awareness, and context awareness.
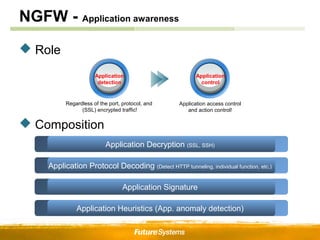
- NGFWs provide integrated firewall, IPS, and other features to control access at the application and user level rather than just the network/port level. NGIPS builds on IPS with application/context awareness to more accurately assess and respond to threats.
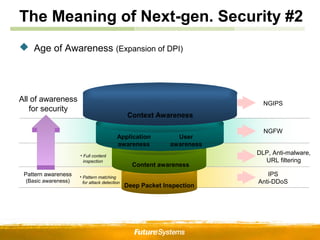
- Context awareness in particular enhances security by providing additional network intelligence and situational awareness to make better response decisions with fewer false alarms. The future of security emphasizes continued convergence through features like expanded awareness capabilities and centralized management


![Evolution of Network Security
[Acronym]
• SPI : Stateful Packet Inspection
• DPI : Deep Packet Inspection
• OC : Outbound Control
• FCI : Full Content Inspection
1984 1988 1991 1993 2001 2002 2004 2009 2011
Boom of Network
Security
Signature Packet Application SPI Application/User Context
Technology DPI OC FCI
detection filtering proxy awareness awareness
IDS IPS NGIPS
Next
Anti-DDoS Generation
Security!!
Product Firewall Firewall UTM NGFW
URL filtering DLP
Web-FW SWG](https://image.slidesharecdn.com/nextgenerationsecurity-130206191451-phpapp02/85/Next-Generation-Security-3-320.jpg)






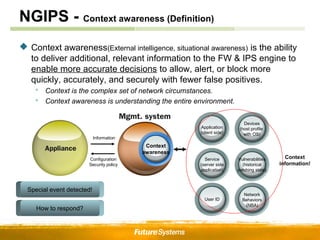
![NGIPS - Context awareness (Example)
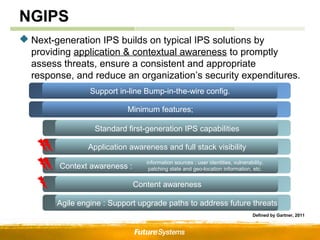
Context awareness provides “Actionable Intelligent”!!!
[Automated Tuning] [Incident Prioritization]
Unknown devise detection Linux-based Alerting
exploit detection (if Detection mode)
Needless action!
Abnormal traffic detection
Target server No
Dismissing/Logging
Provided?
Unexpected App./User
detection Impact level low!
Yes
…
Target server No
New vulnerability Blocking
patched?
reported
Impact level high!
Yes
Dismissing/Logging
Recommend related policy Impact level middle!](https://image.slidesharecdn.com/nextgenerationsecurity-130206191451-phpapp02/85/Next-Generation-Security-13-320.jpg)