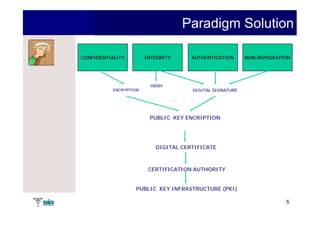
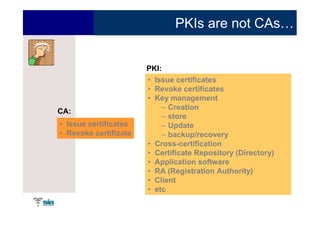
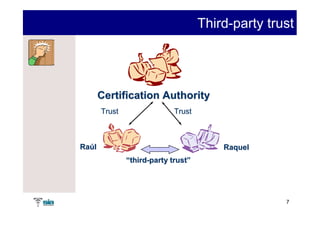
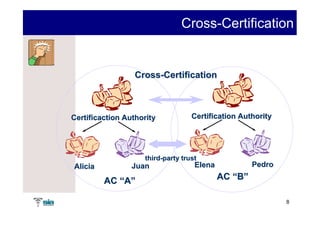
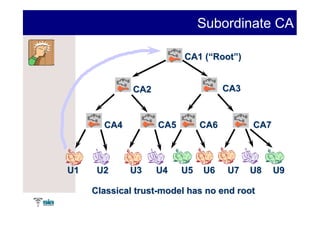
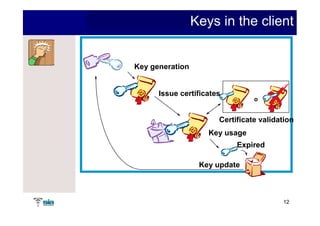
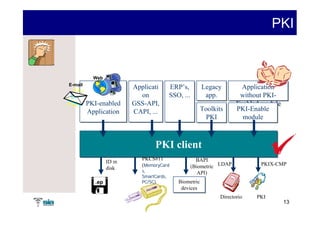
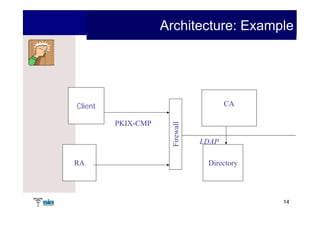
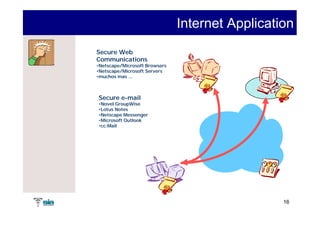
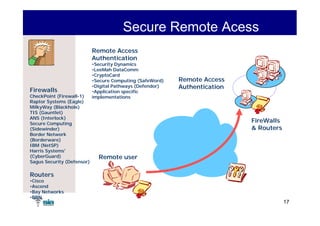
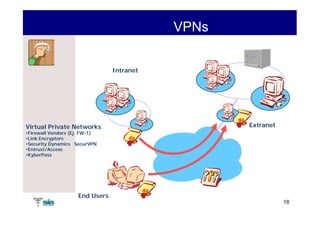
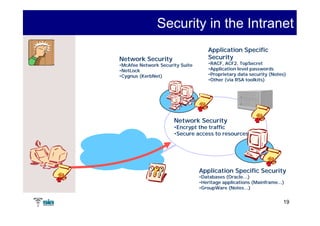
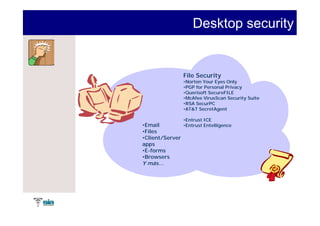
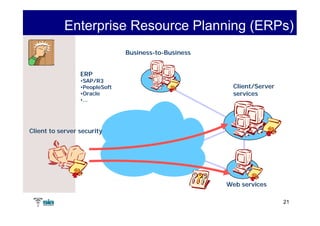
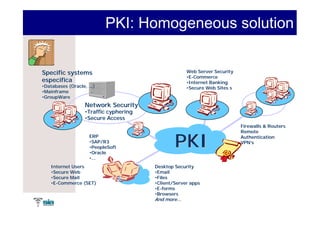
The document summarizes Raúl Guerra Jiménez's presentation on PKI interoperability at the FIST Conference in September 2005 in Madrid. It discusses the basics of public key infrastructure (PKI) including concepts like digital certificates, certification authorities, cross-certification, and certificate revocation. It also provides examples of PKI applications in areas like internet security, remote access, virtual private networks, and securing intranets and applications.