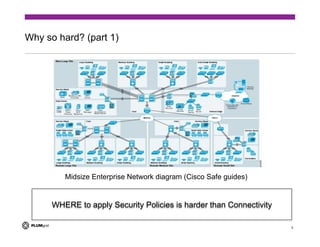
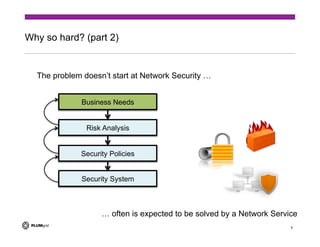
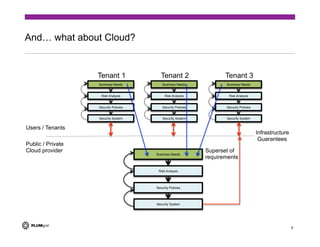
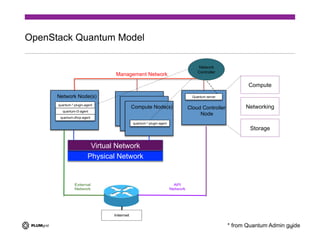
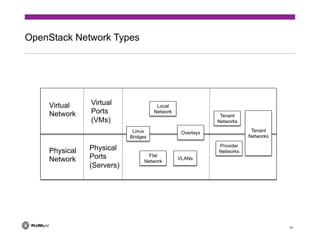
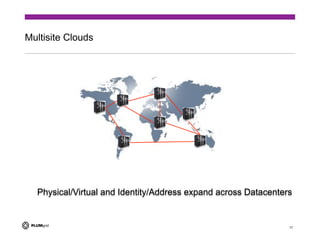
The document discusses the challenges of providing secure networking in public and private cloud environments. It notes that security is difficult because connectivity needs to be provided by default while preventing unwanted connections, and that security policies are harder to apply than just enabling connectivity. The document also examines issues like tenant isolation, application isolation, multitenant challenges, identity and location-based security approaches, and how to better integrate security capabilities into cloud platforms like OpenStack. It argues that security must be designed into networks from the beginning as an integrated system rather than added as an afterthought.