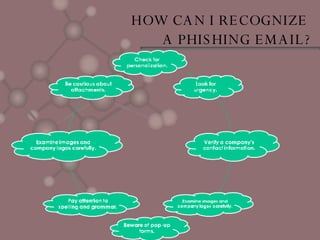
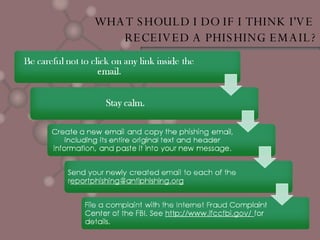
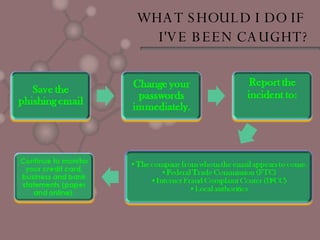
Phishing is a form of cybercrime where scammers acquire personal information like credit card numbers and passwords by sending fraudulent emails pretending to be from legitimate businesses. These emails will ask users to provide or verify personal details. Phishing is growing rapidly and targets users of online banking and auction sites. To protect yourself, be wary of unsolicited requests for information via email and ensure your devices have updated antivirus software. If you receive a phishing email or become a victim, report it and monitor your accounts for fraudulent activity.