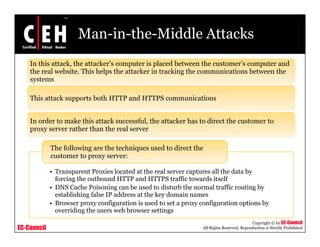
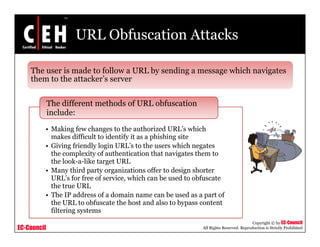
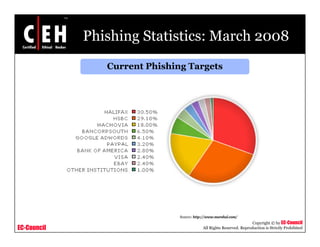
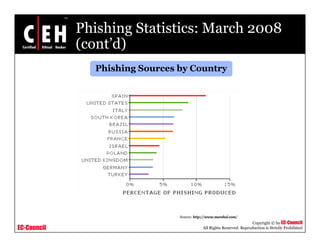
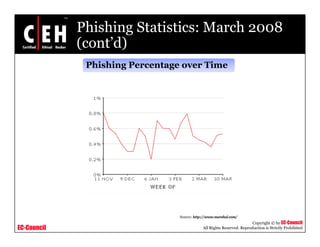
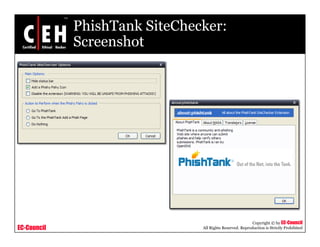
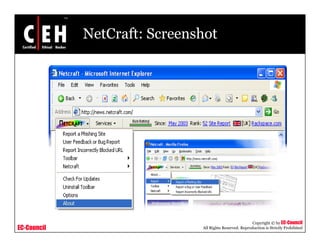
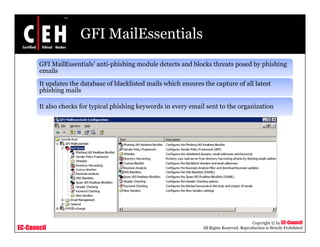
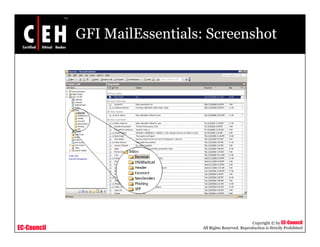
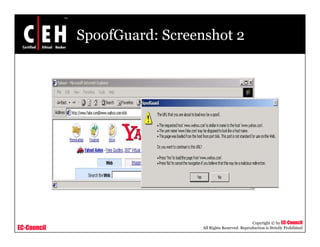
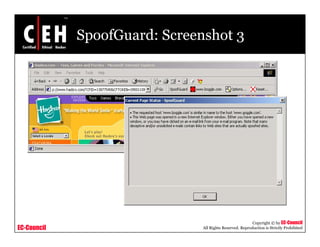
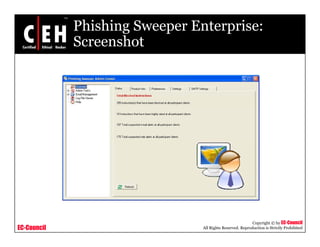
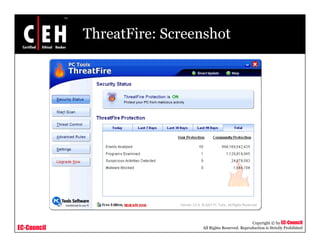
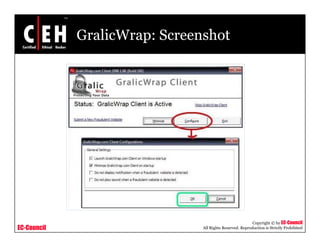
This document discusses phishing attacks and methods to prevent them. It begins with an introduction to phishing and reasons it is successful. It then outlines various phishing methods like email spam, web-based delivery, and Trojan horses. It also describes the typical process of phishing and different attack types such as man-in-the-middle, URL obfuscation, and client-side vulnerabilities. The document concludes by discussing anti-phishing tools like PhishTank SiteChecker that block phishing pages.