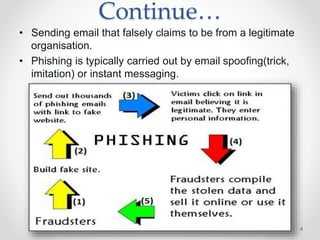
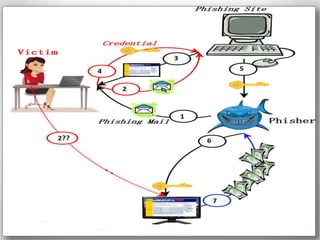
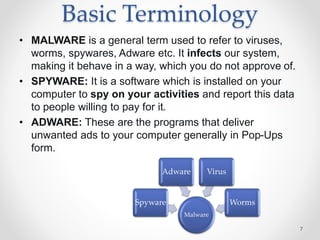
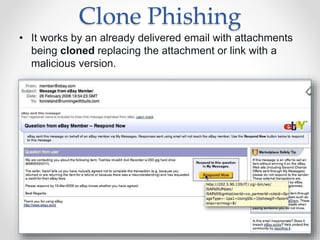
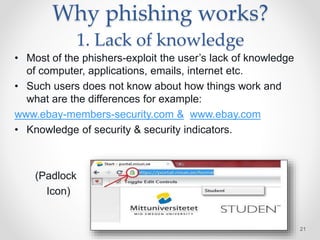
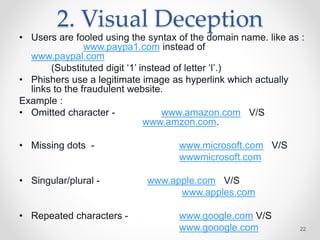
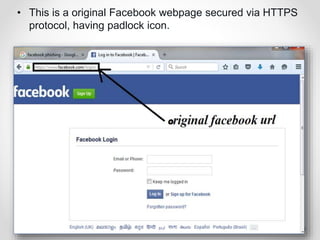
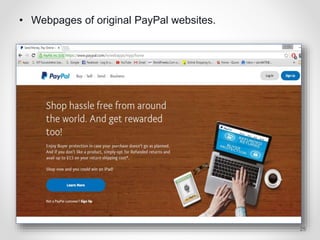
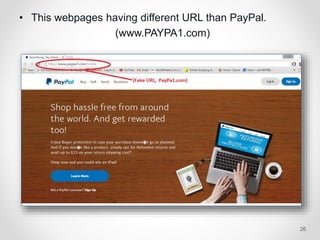
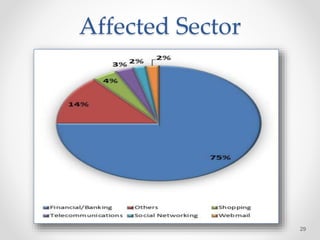
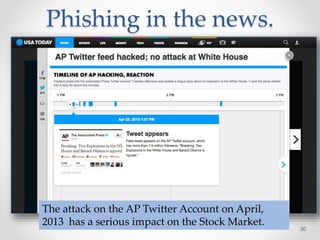
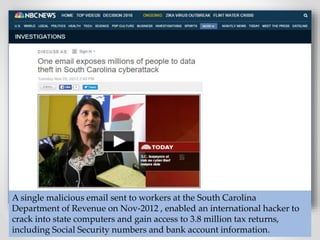
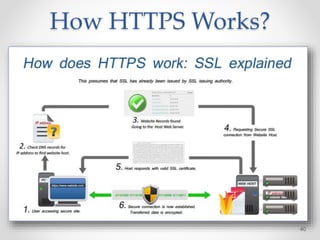
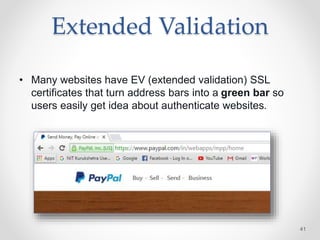
The document provides an overview of phishing attacks, explaining their motives, techniques, and impacts on individuals and organizations. It highlights various types of phishing, including spear phishing and whaling, as well as methods for protection, such as two-factor authentication and the use of SSL encryption. The document concludes with recommendations for avoiding phishing attacks and stresses the importance of education in combating this growing threat.