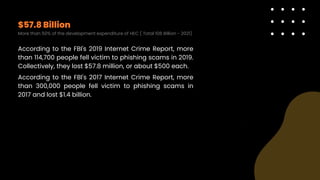
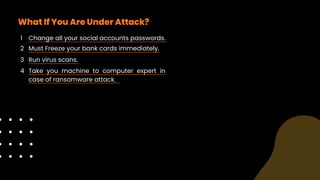
Phishing is a type of cyber attack aimed at stealing sensitive user data by tricking victims into interacting with fraudulent communications that appear legitimate. Common methods include spear phishing, MITM attacks, vishing, smishing, angler phishing, whaling, and pharming, with significant financial losses reported by victims. Protection involves security awareness training, vigilance against suspicious communications, and immediate action if compromised.