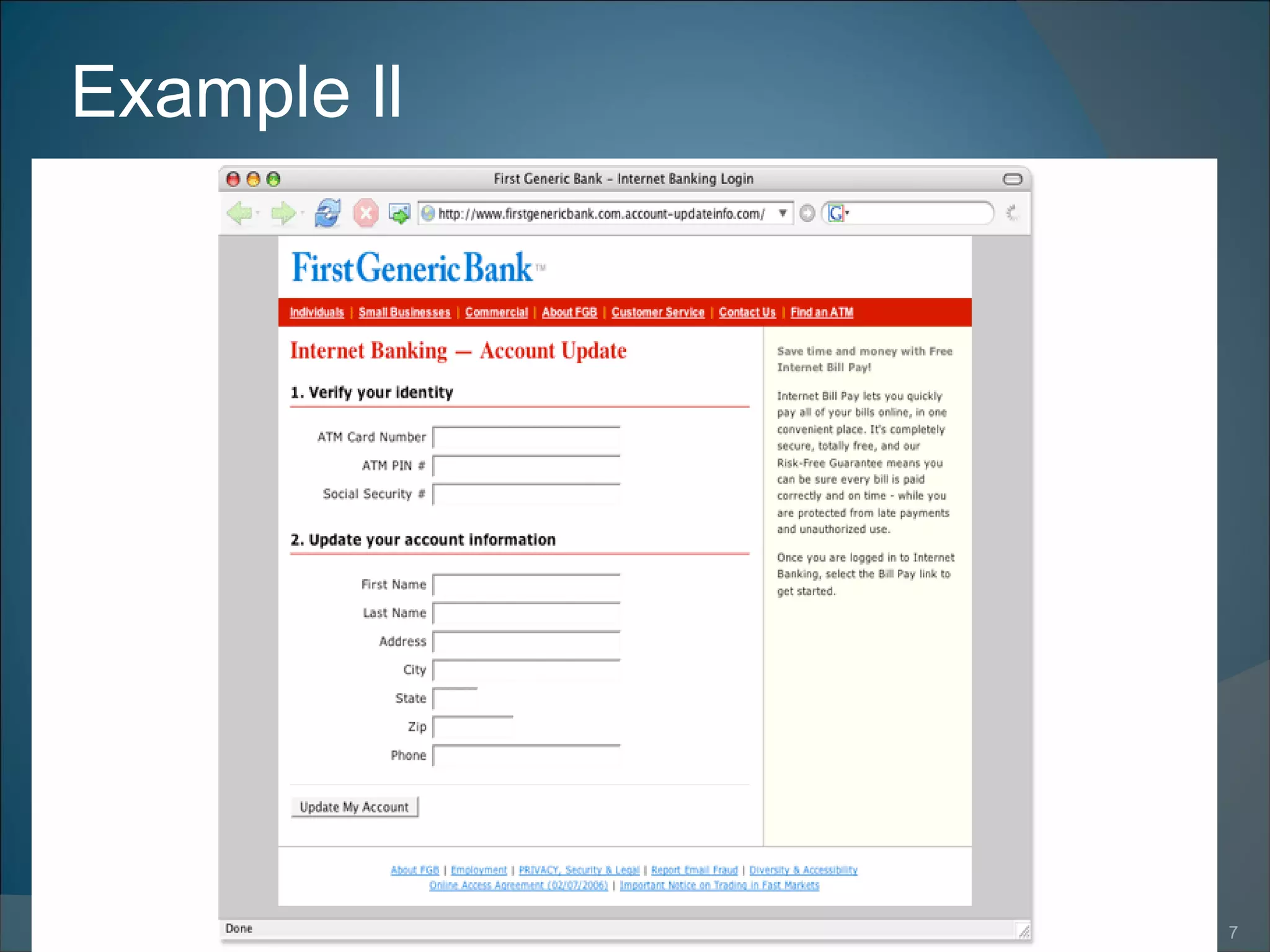
Phishing involves tricking individuals into providing personal information through fraudulent emails or websites. Attackers make links or websites look like they belong to legitimate organizations to deceive victims. This can be done with misspelled URLs or subdomains. Some signs of phishing are misspelled domains, URLs containing @ symbols, or scripts on legitimate websites. Phishing can result in identity theft, financial loss, or unauthorized access to accounts. Once attackers obtain personal details, they may create fake accounts or access existing accounts without consent. Phishing is a growing problem but can be detected by looking for signs of deception or irregularities.