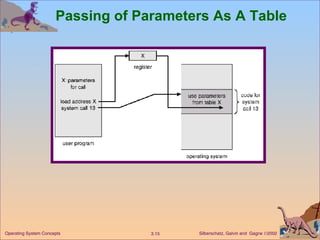
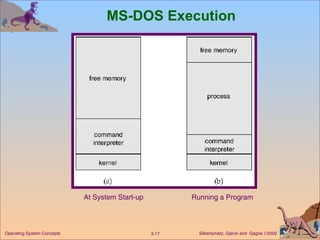
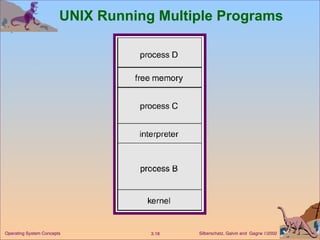
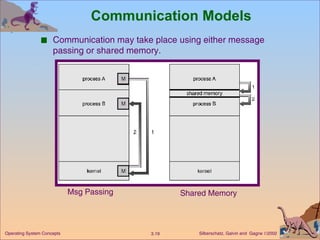
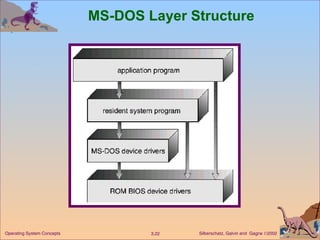
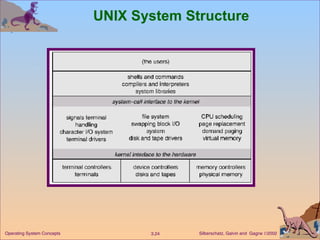
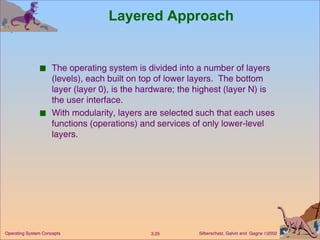
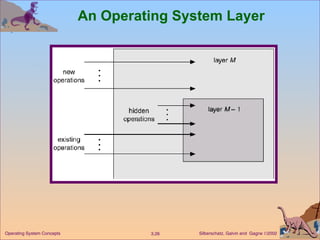
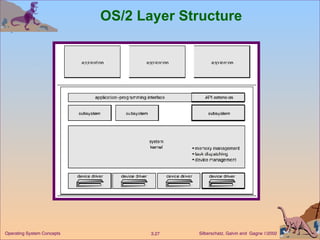
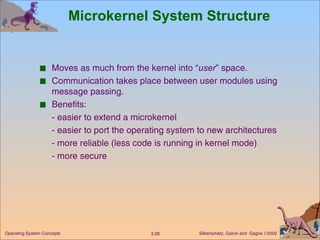
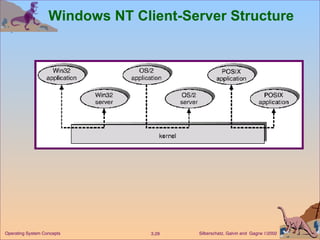
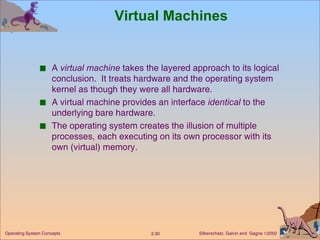
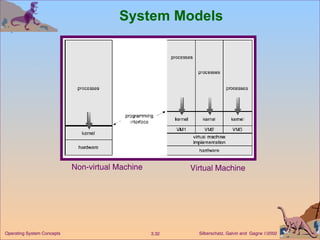
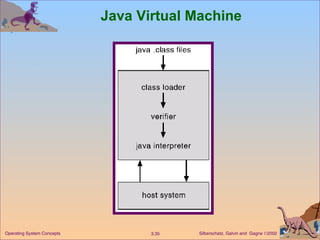
The document provides an overview of operating system structures and components. It discusses process management, memory management, file management, I/O system management, secondary storage management, networking, protection systems, and command interpreters. It also describes system calls, system programs, virtual machines, and different system models including non-virtual and virtual machine models.