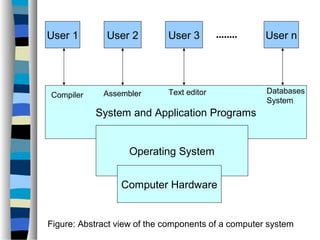
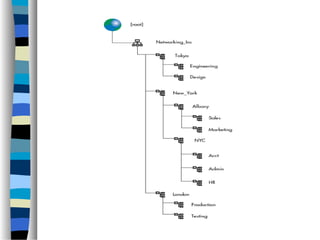
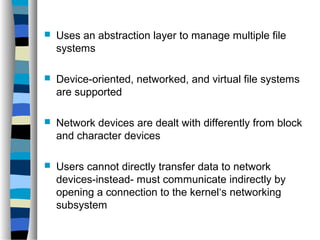
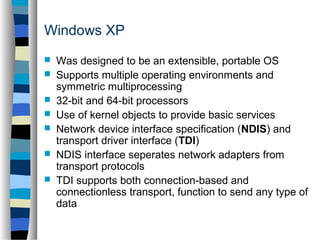
This document discusses network operating systems. It begins by defining key concepts like systems, networks, and operating systems. It then introduces network operating systems, which allow users to access remote resources by logging into other machines or transferring files between computers. Example features of network operating systems are described like security, directory services, and file/print sharing. Specific network operating systems are also outlined, such as Novell NetWare, Linux, and Windows XP. The document concludes by summarizing the differences between a regular operating system and a network operating system.