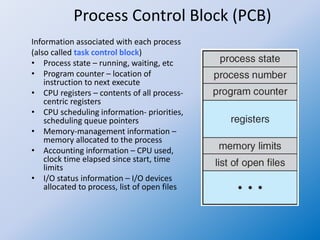
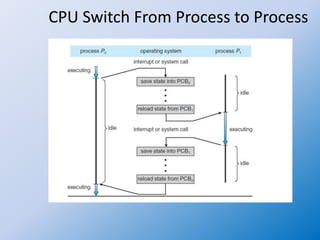
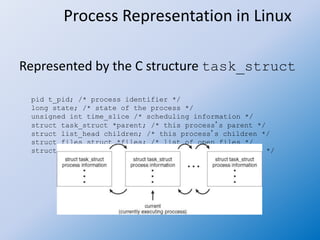
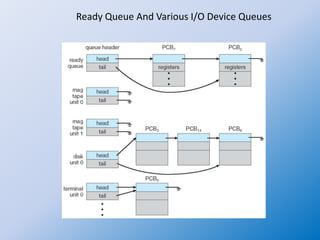
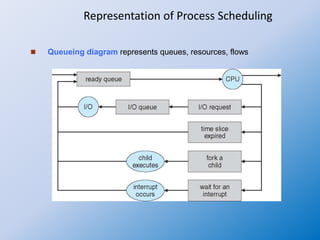
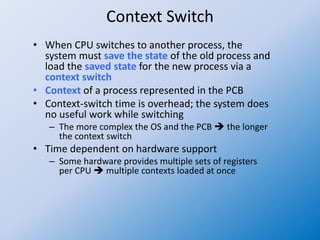
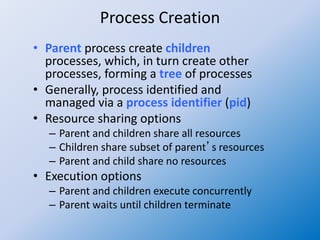
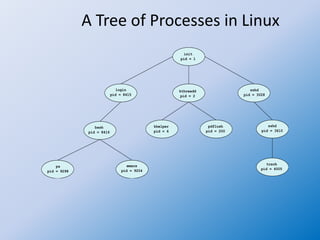
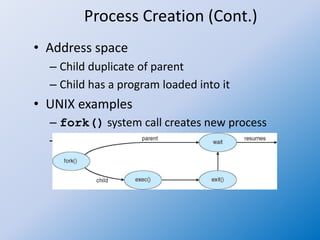
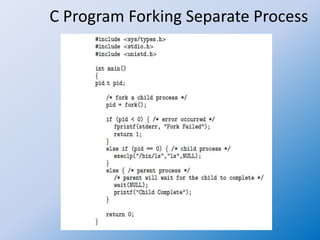
The document discusses process creation and termination in operating systems, detailing various states of processes, the role of the process control block (PCB), and types of schedulers. It explains CPU scheduling, context switching, and how processes are created, executed, and terminated, including Unix system calls involved in these operations. Additionally, it touches on multitasking in mobile systems and the implications of process termination, including cascading termination and handling orphan processes.