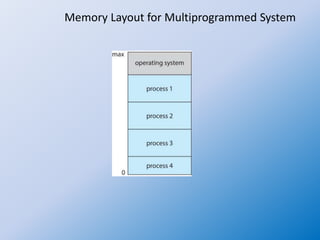
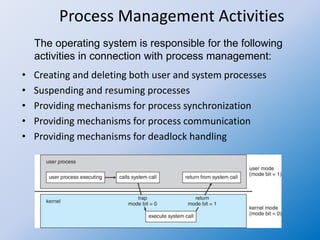
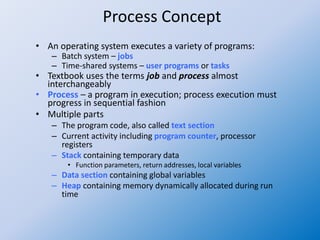
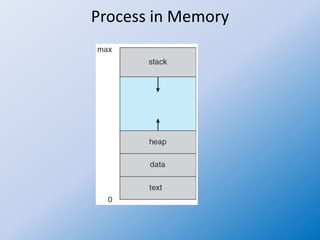
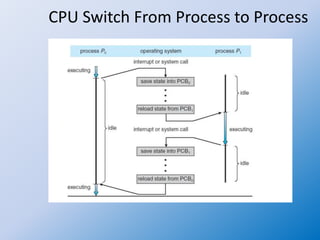
The document discusses the concepts of process management in operating systems, highlighting the importance of multiprogramming and multitasking to efficiently utilize CPU and I/O devices. It defines processes as active entities compared to passive programs and describes various process states such as new, running, waiting, ready, and terminated, along with the role of the process control block (PCB). Additionally, it outlines key activities involved in process management, including creation, synchronization, communication, and handling deadlocks.