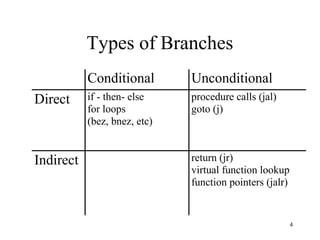
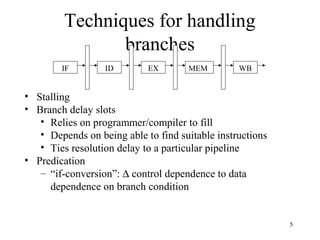
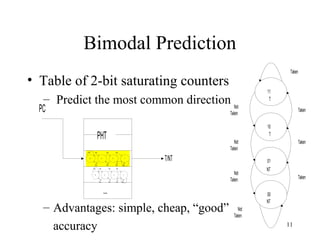
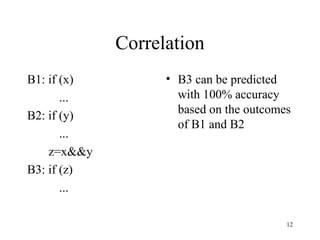
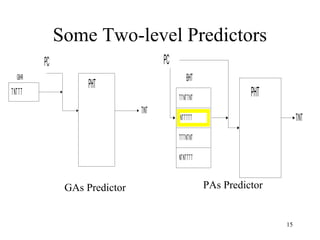
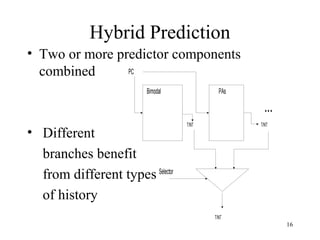
Branch prediction is necessary to reduce penalties from branches in modern deep pipelines. It predicts the direction (taken or not taken) and target of branches. Common techniques include bimodal prediction using saturating counters and two-level prediction using branch history tables and pattern history tables. Real processors use hybrid predictors combining different techniques. Mispredictions require flushing the pipeline and incur a performance penalty.