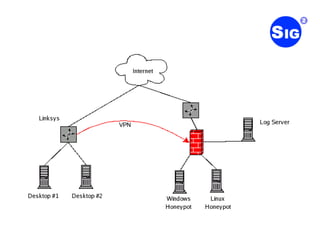
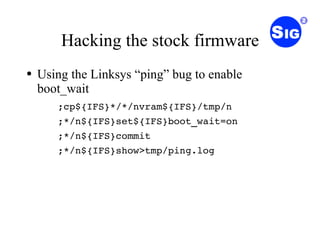
This document summarizes the SOHO Honeynet Project which aims to use inexpensive consumer routers to expand honeynet networks. The project uses Linksys WRT54G or WRT54GS routers running customized OpenWRT firmware to establish a VPN to a central honeynet and redirect traffic that would normally be dropped by the firewall. The document provides an overview of the project goals, hardware choices, hacking the stock firmware, installing custom firmware, and software required as well as calling for developers, testers, and documentation authors to participate in the project.