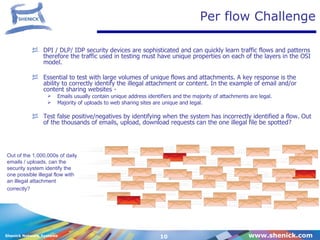
The document discusses various strategies for testing cyber-terrorism defenses, highlighting the dangers of ignorance and lack of basic computer skills among individuals. It outlines the distinctions between visible and invisible threats, countermeasures against cyber crimes, and emphasizes the importance of performance testing with unique traffic flows. Additionally, it introduces 'DiversifEye,' a tool for emulating real-world client interactions and analyzing network performance in various environments.