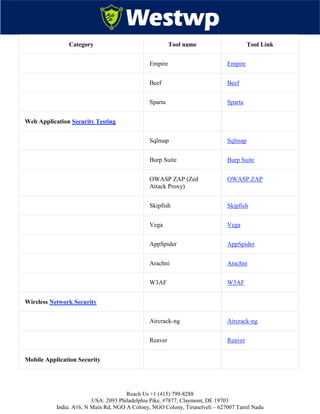
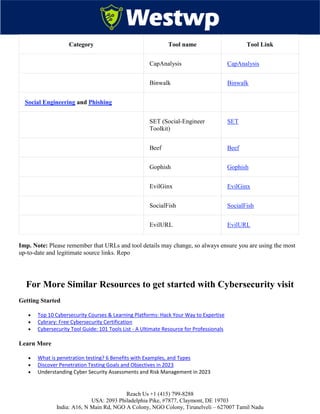
The document is a comprehensive guide outlining over 101 cybersecurity tools essential for protecting businesses from cyber threats, detailing their functions, advantages, and disadvantages. It is divided into segments focusing on various aspects of cybersecurity, including network security, endpoint security, application security, data security, and risk management tools. Additionally, it emphasizes the importance of thorough research, expert consultation, and effective utilization of these tools in enhancing cyber defenses.