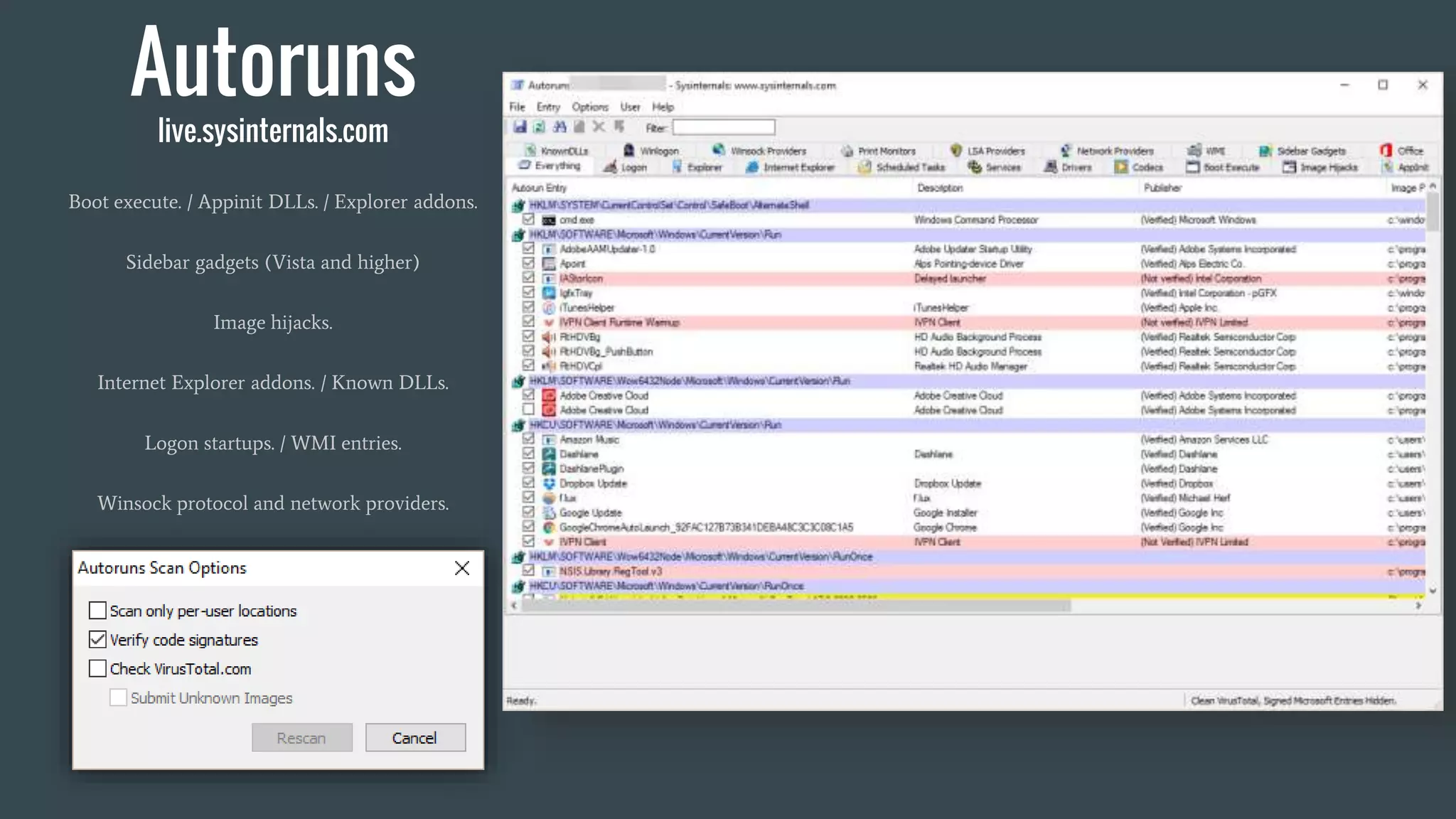
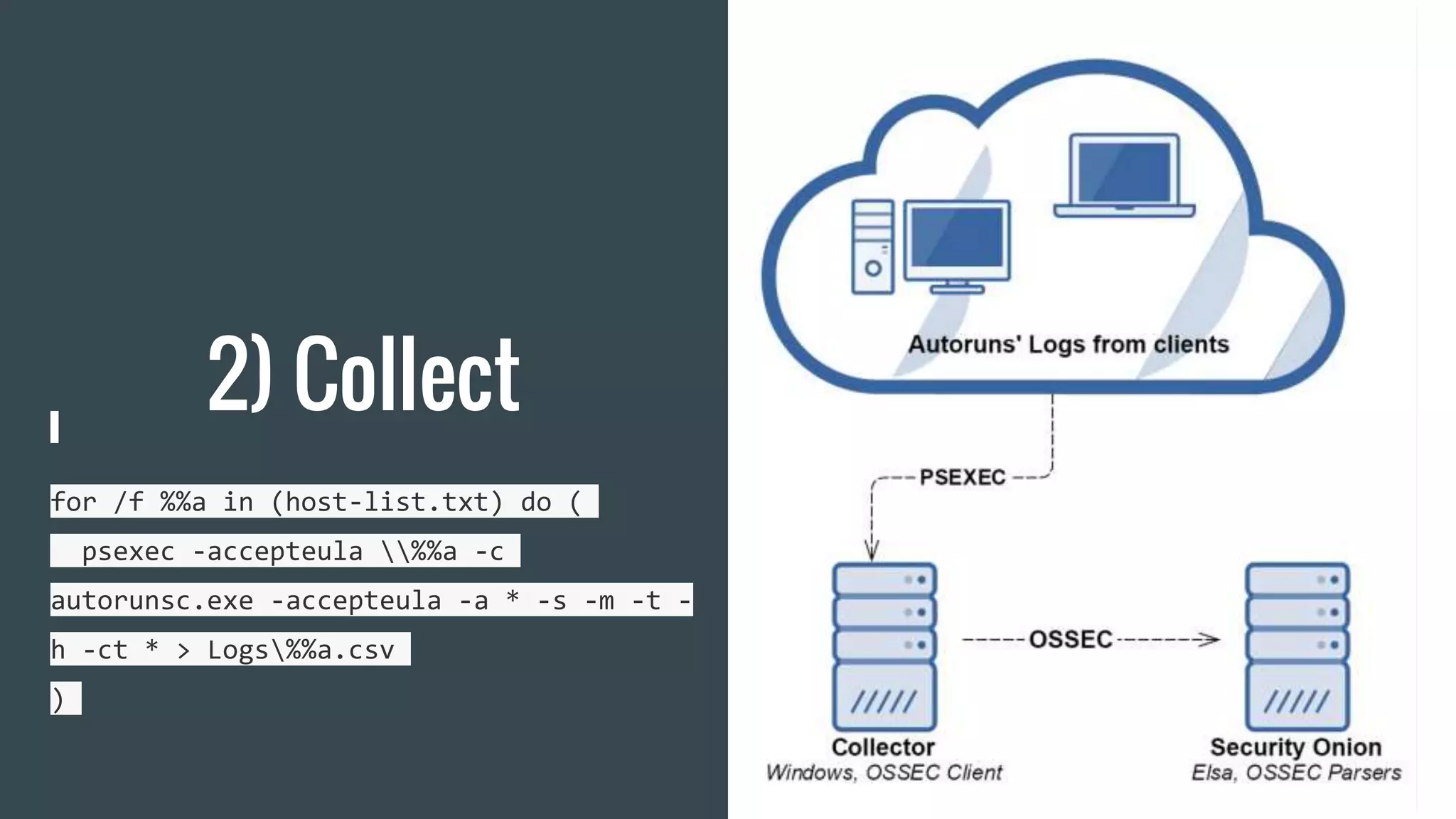
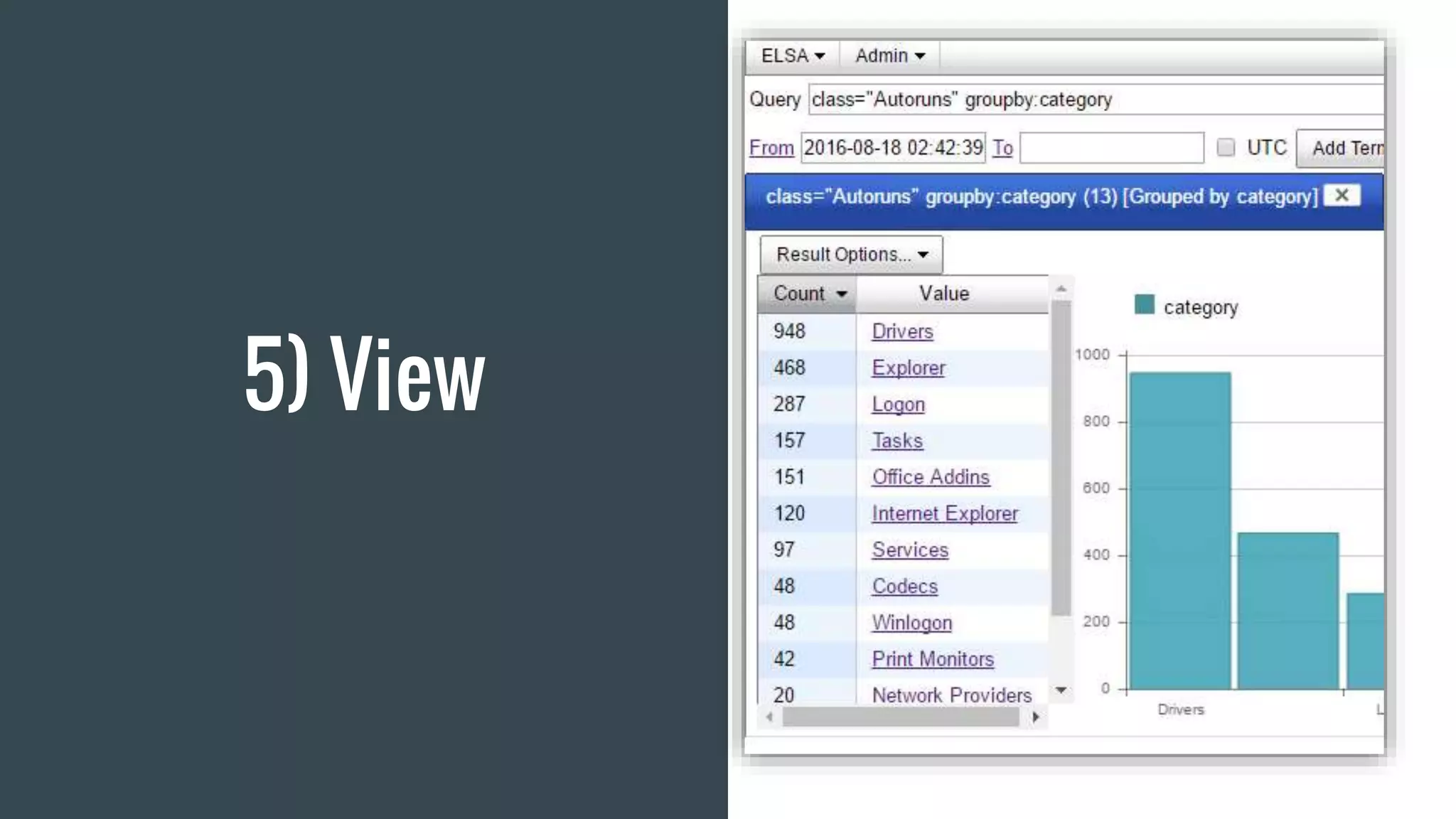
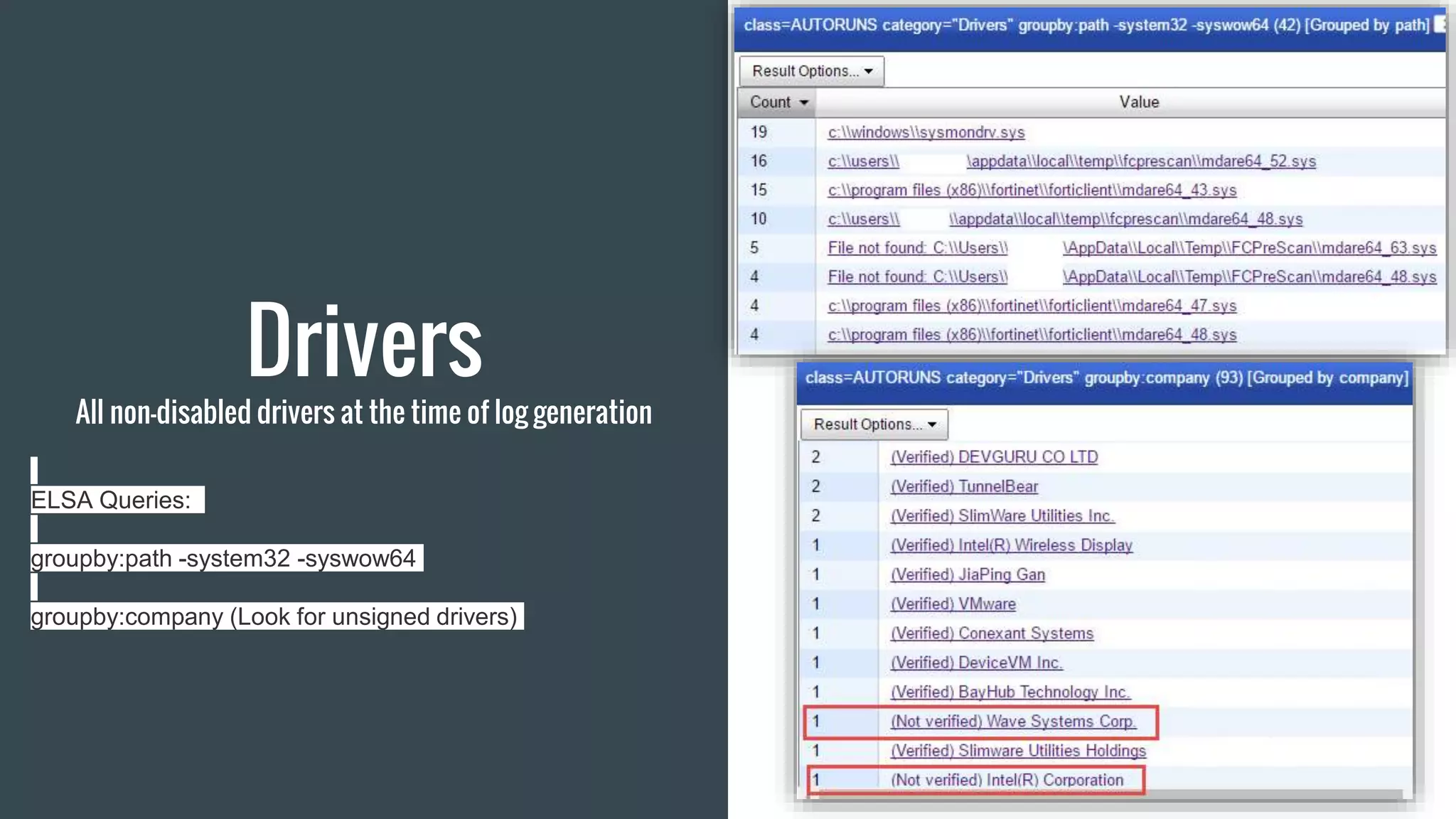
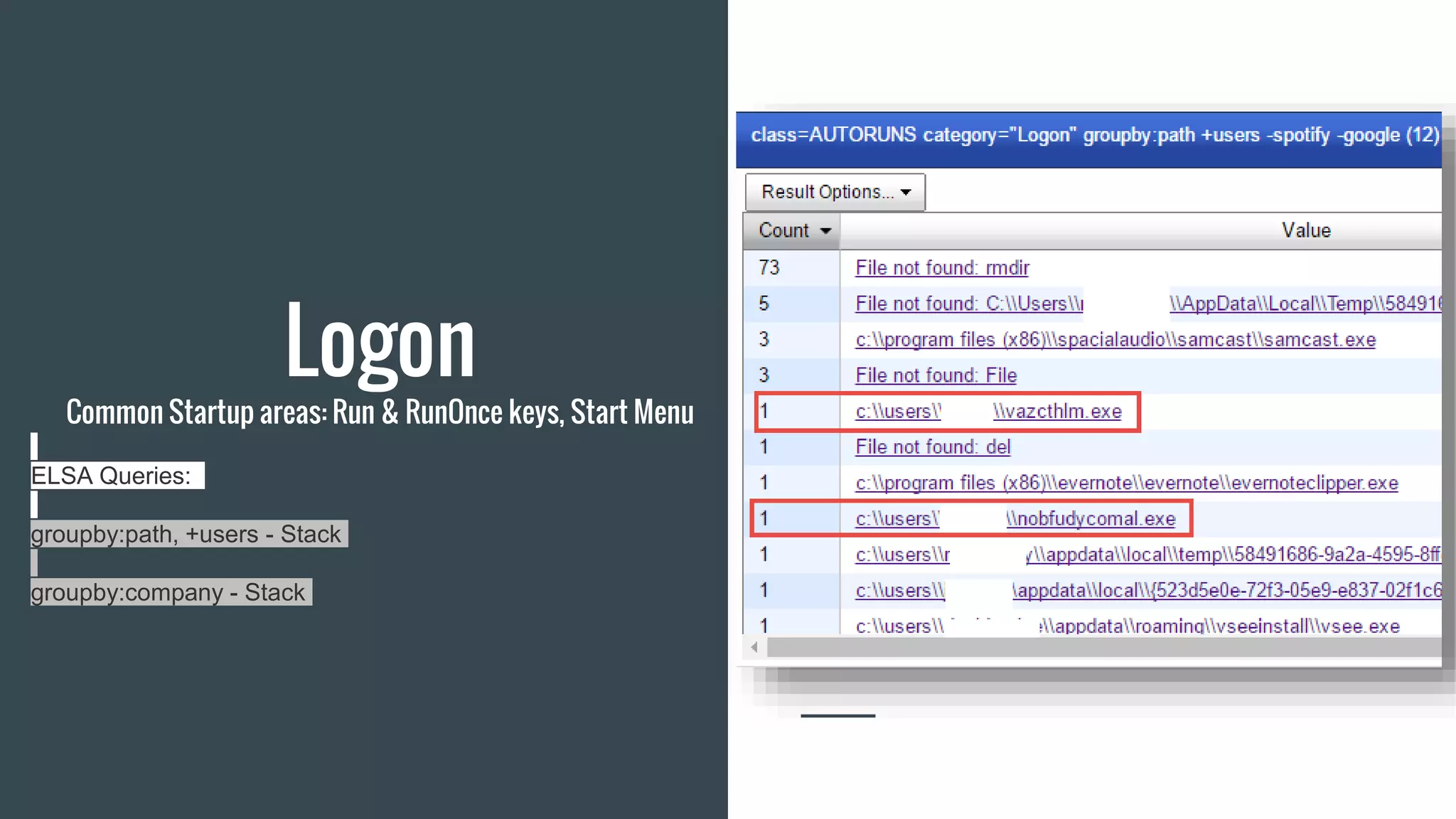
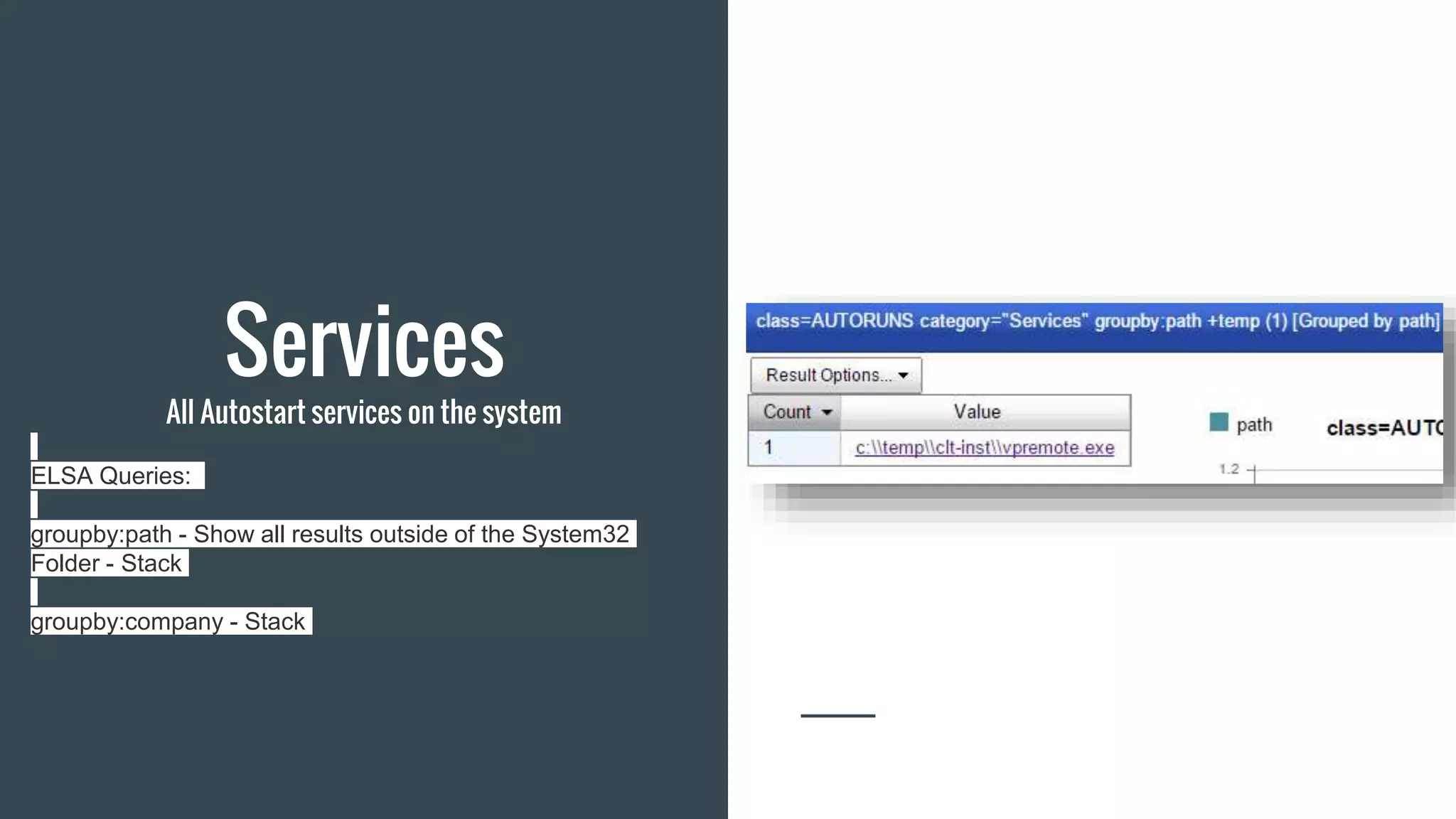
The document discusses using Autoruns and Security Onion to uncover persistence on systems. It describes how Autoruns can detect various types of persistence mechanisms including boot execute items, DLLs, Explorer addons, image hijacks, and more. It then outlines how Security Onion can be used to generate Autoruns logs from multiple systems, normalize the data, import it, and perform queries to detect anomalous or malicious items that may indicate persistence. Real-world use cases are discussed where this approach reduces the number of items to manually review from thousands to a few hundred.