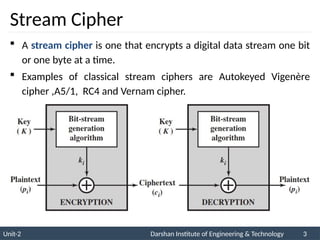
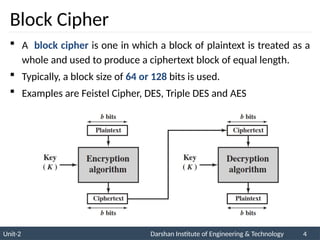
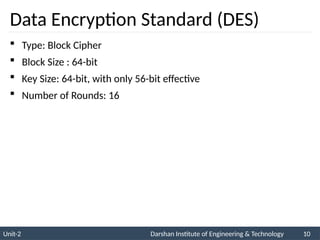
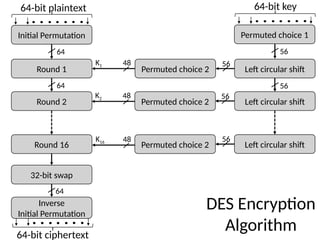
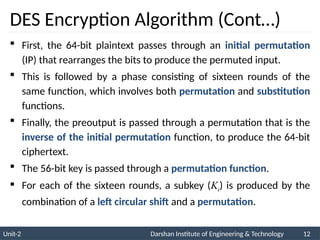
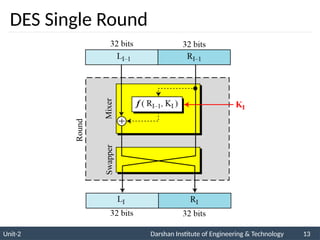
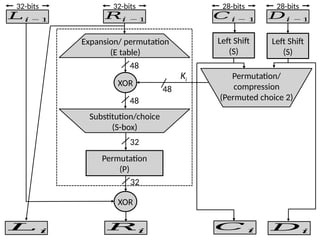
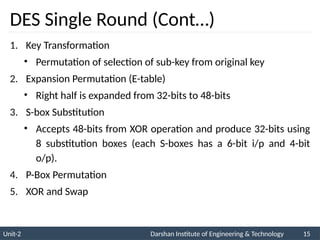
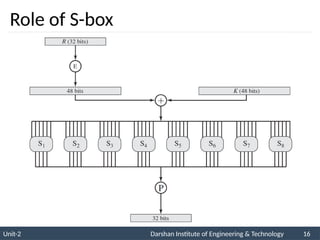
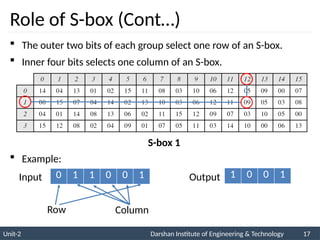
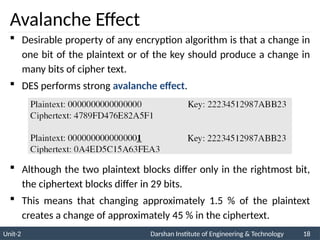
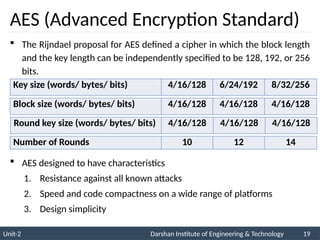
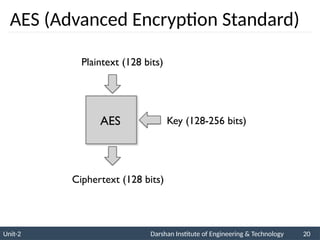
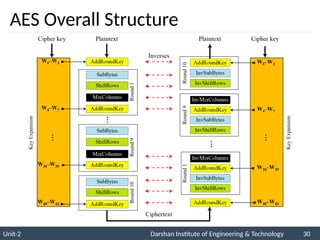
The document provides an overview of stream ciphers and block ciphers, detailing their structures and examples, such as DES and AES. It explains key concepts including diffusion and confusion, the Feistel cipher structure, and the operations involved in encryption and decryption processes. Additionally, the document outlines the AES structure, transformation functions, and the key expansion algorithm.

![Feistel Encryption & Decryption
Prove that o/p of first round
of Decryption is equal to 32-
bit swap of i/p of 16th
round of
Encryption
LD1=RE15 & RD1=LE15
𝐿𝐸16=𝑅 𝐸15
𝑅𝐸16=𝐿𝐸15 ⊕ 𝐹(𝑅𝐸15 ,𝐾16)
On Encryption Side:
𝐿𝐷1=𝑅𝐷0=𝐿𝐸16=𝑅𝐸15
𝑅𝐷1=𝐿 𝐷0⊕ 𝐹 (𝑅 𝐷0 ,𝐾16)
On Decryption Side:
¿ 𝑅𝐸16 ⊕ 𝐹 (𝑅𝐸15 , 𝐾 16 )
¿[𝐿𝐸¿¿15⊕𝐹 (𝑅𝐸15 , 𝐾16)] ⊕𝐹 (𝑅𝐸15 , 𝐾16)¿
XOR Associativity
Property](https://image.slidesharecdn.com/2170709insgtustudymaterialpresentationsunit-206082020060231am-241209063112-8a5b1b4e/85/Stream-Ciphers-and-Block-Ciphers-in-Security-pptx-9-320.jpg)
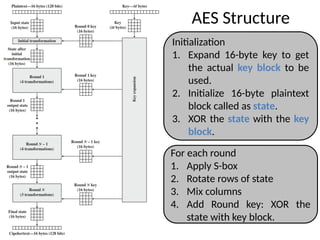
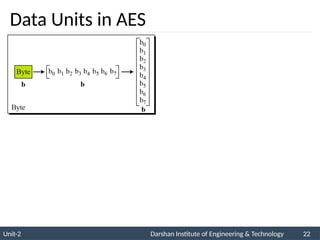
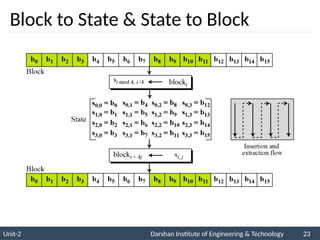
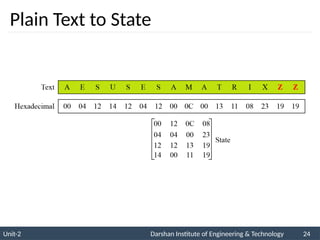
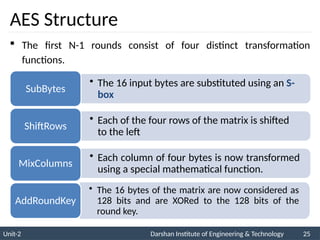
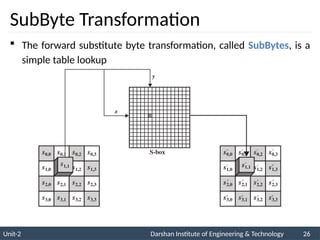
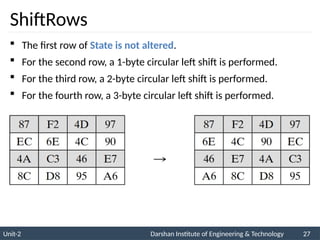
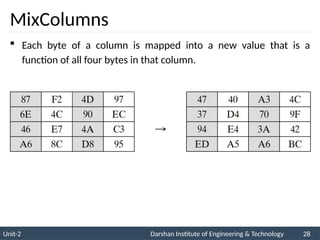
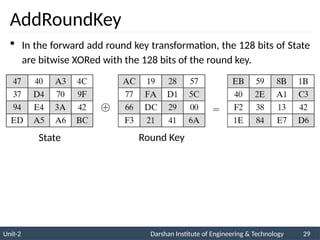
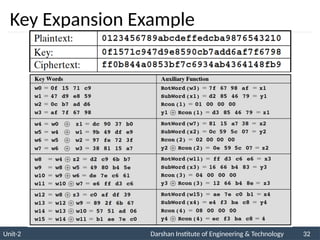
![ The AES key expansion algorithm takes as
input a four-word (16-byte) key and produces
a linear array of 44 words (176 bytes).
Each added word w[i] depends on the
immediately preceding word, w[i - 1].
In three out of four cases, a simple XOR is
used.
AES Key Expansion](https://image.slidesharecdn.com/2170709insgtustudymaterialpresentationsunit-206082020060231am-241209063112-8a5b1b4e/85/Stream-Ciphers-and-Block-Ciphers-in-Security-pptx-31-320.jpg)