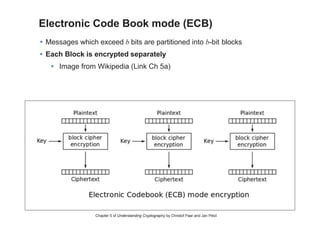
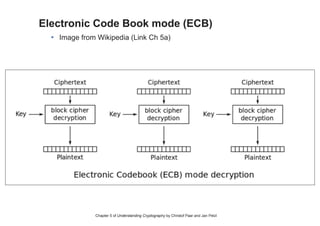
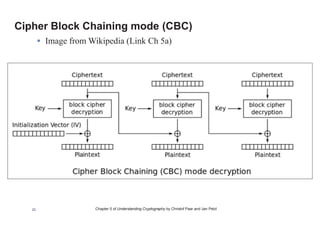
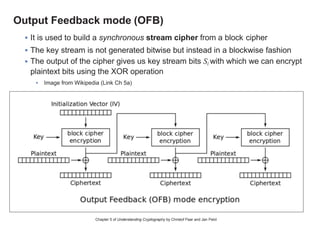
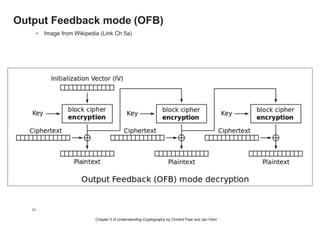
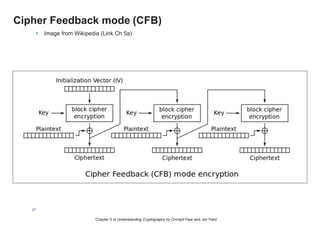
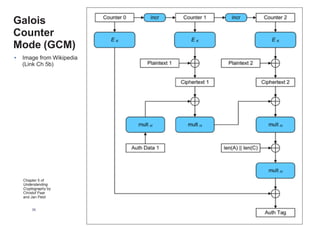
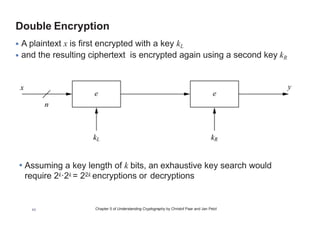
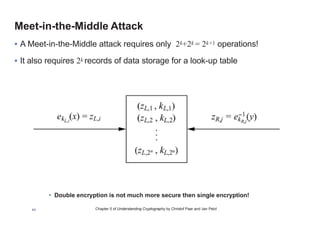
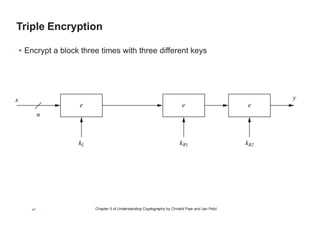
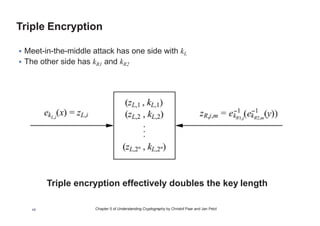
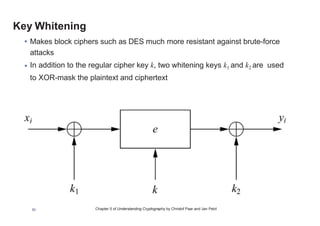
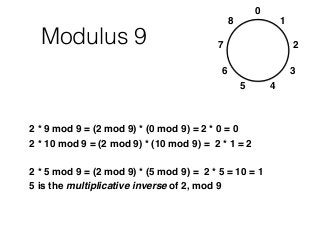
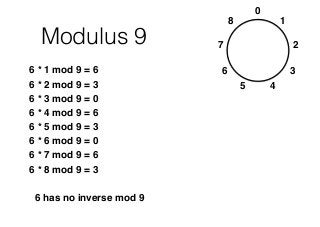
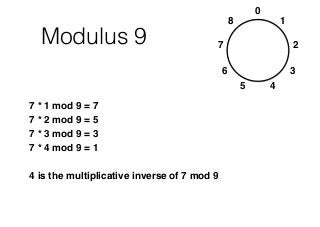
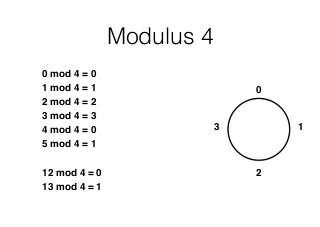
This chapter summary covers modes of operation for block ciphers and techniques for increasing the security of block ciphers. It discusses the following modes: Electronic Codebook (ECB), Cipher Block Chaining (CBC), Output Feedback (OFB), Cipher Feedback (CFB), Counter (CTR), and Galois Counter (GCM) modes. It also covers techniques like double encryption, triple encryption, and key whitening that can strengthen block ciphers against brute force attacks. Quantum computers may break algorithms like RSA and AES-128, but AES-192 and AES-256 should remain secure even with quantum computers.