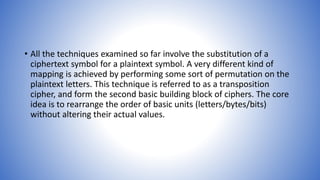
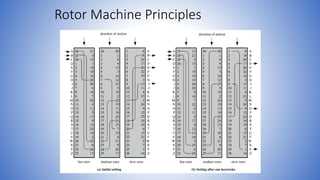
The document discusses transposition ciphers, which hide messages by rearranging the order of plaintext letters without changing their actual values. It explores various transposition techniques, including the rail fence cipher and columnar transposition, explaining how these methods maintain the original letter frequencies, making them identifiable. Furthermore, it contrasts classical ciphers with modern ciphers, highlighting the introduction of rotor machines during WW2, which employed complex substitution through rotating mechanisms to enhance security.