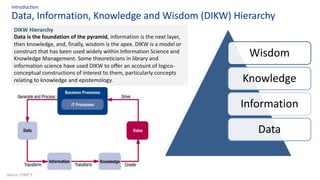
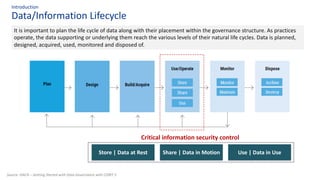
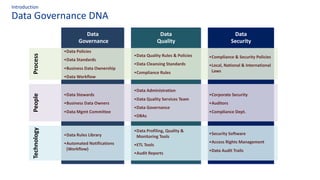
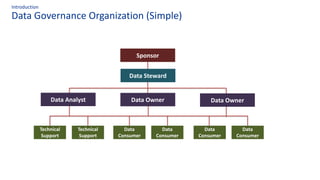
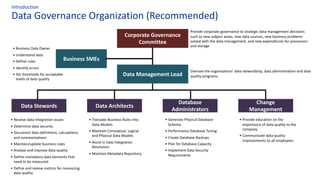
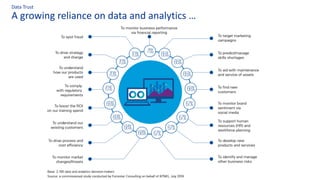
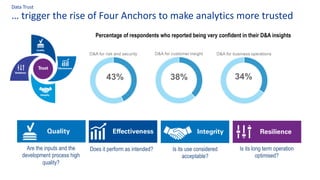
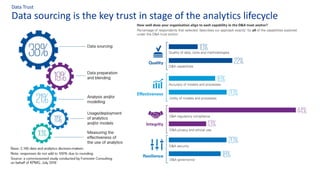
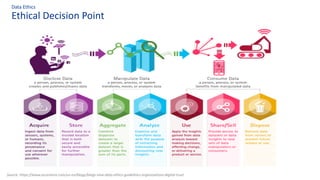
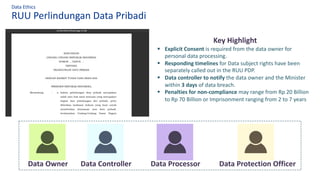
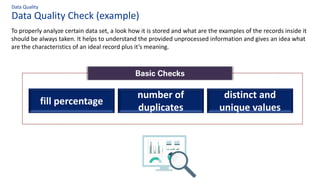
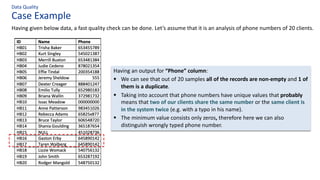
The document discusses the importance of data governance, trust, ethics, and quality within organizations, highlighting frameworks and strategies for managing data responsibly. It emphasizes the significance of ethical data usage and the potential impact of poor data quality on decision-making. Additionally, it outlines necessary infrastructure and governance structures to ensure effective data management and compliance with regulations.