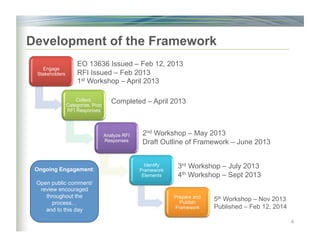
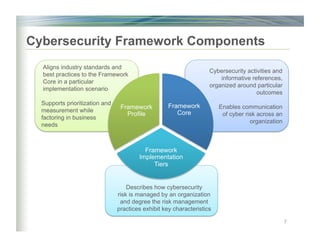
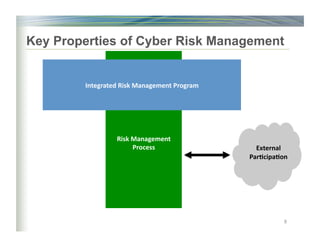
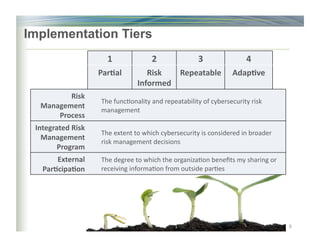
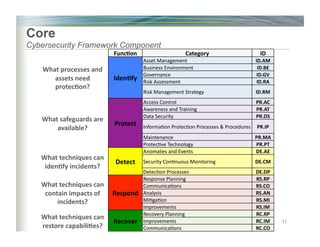
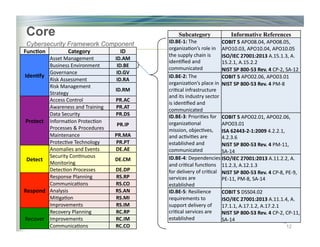
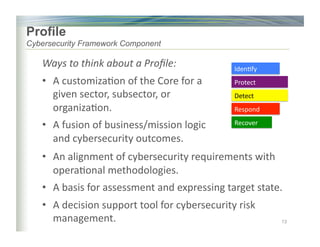
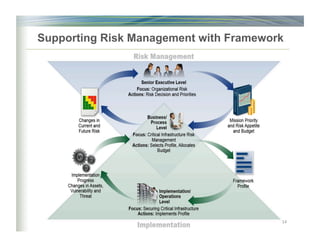
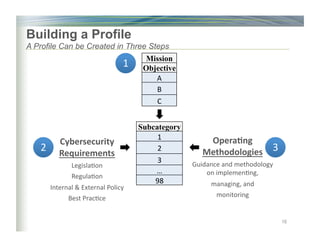
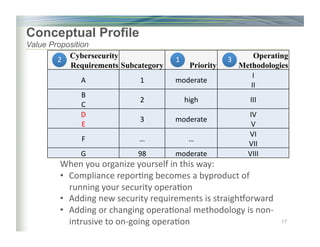
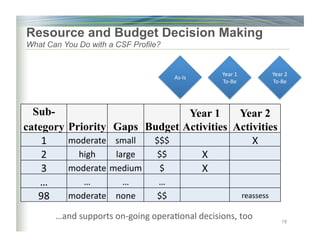
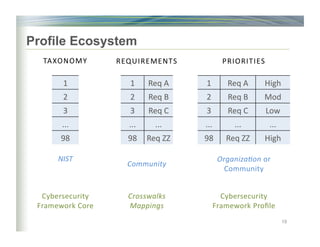
The document outlines the framework for enhancing cybersecurity within the nation's critical infrastructure, emphasizing a flexible and cost-effective approach to identify and manage cyber risks. It includes standards and methodologies that align business and technological strategies, applicable to organizations of all sizes and sectors. The framework is continuously improved and encourages ongoing stakeholder engagement while being consistent with international standards and legal requirements.