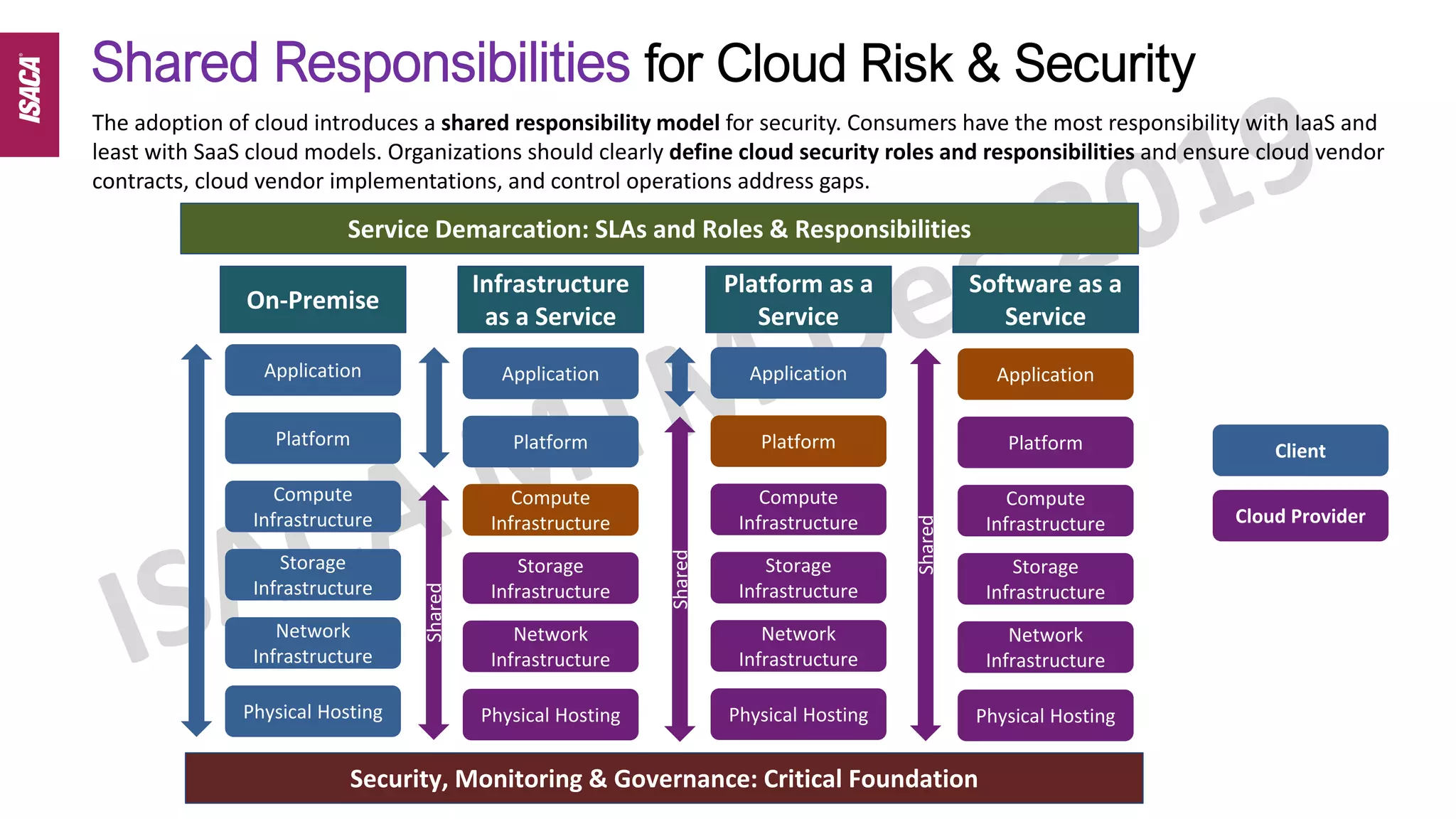
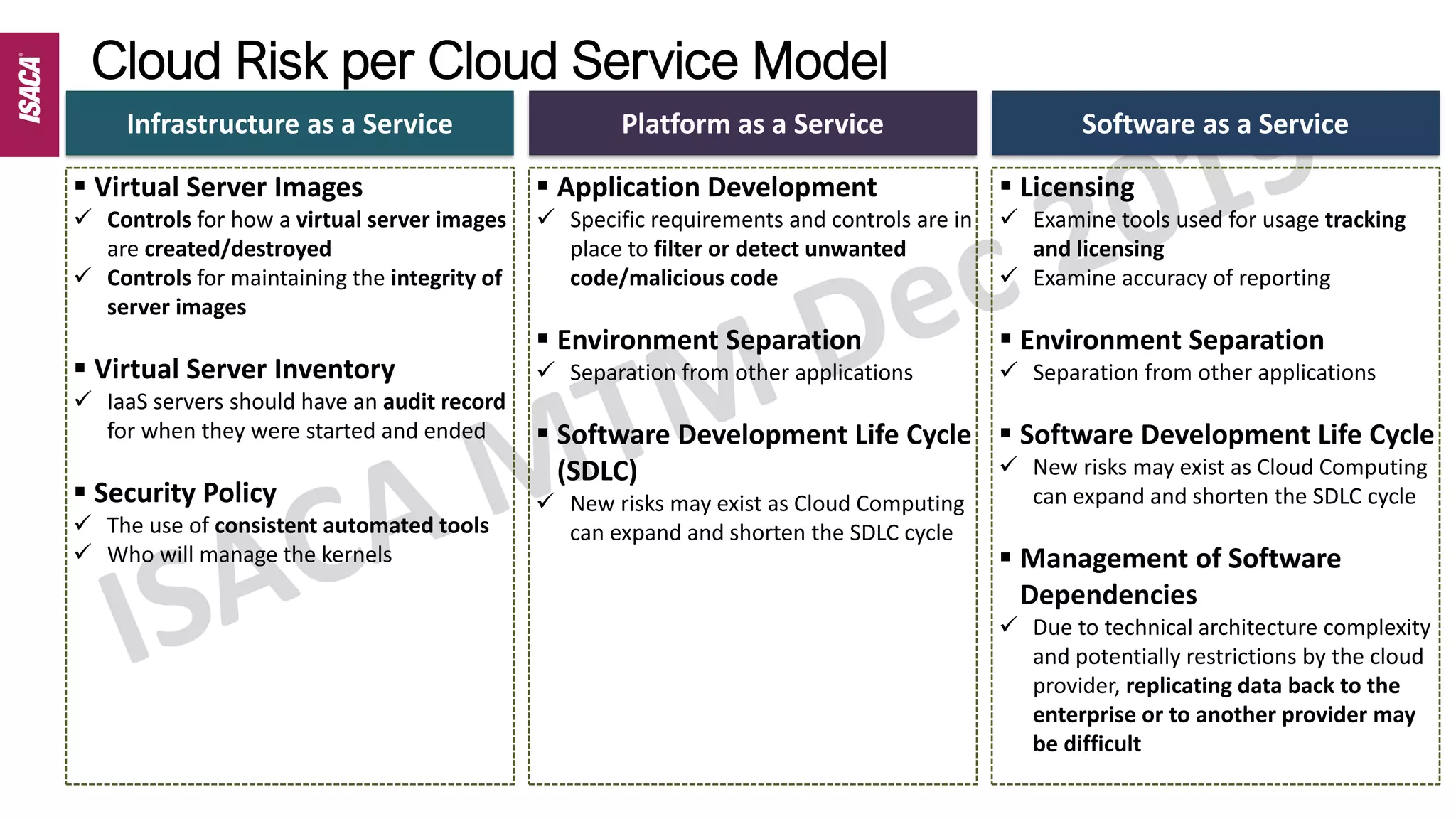
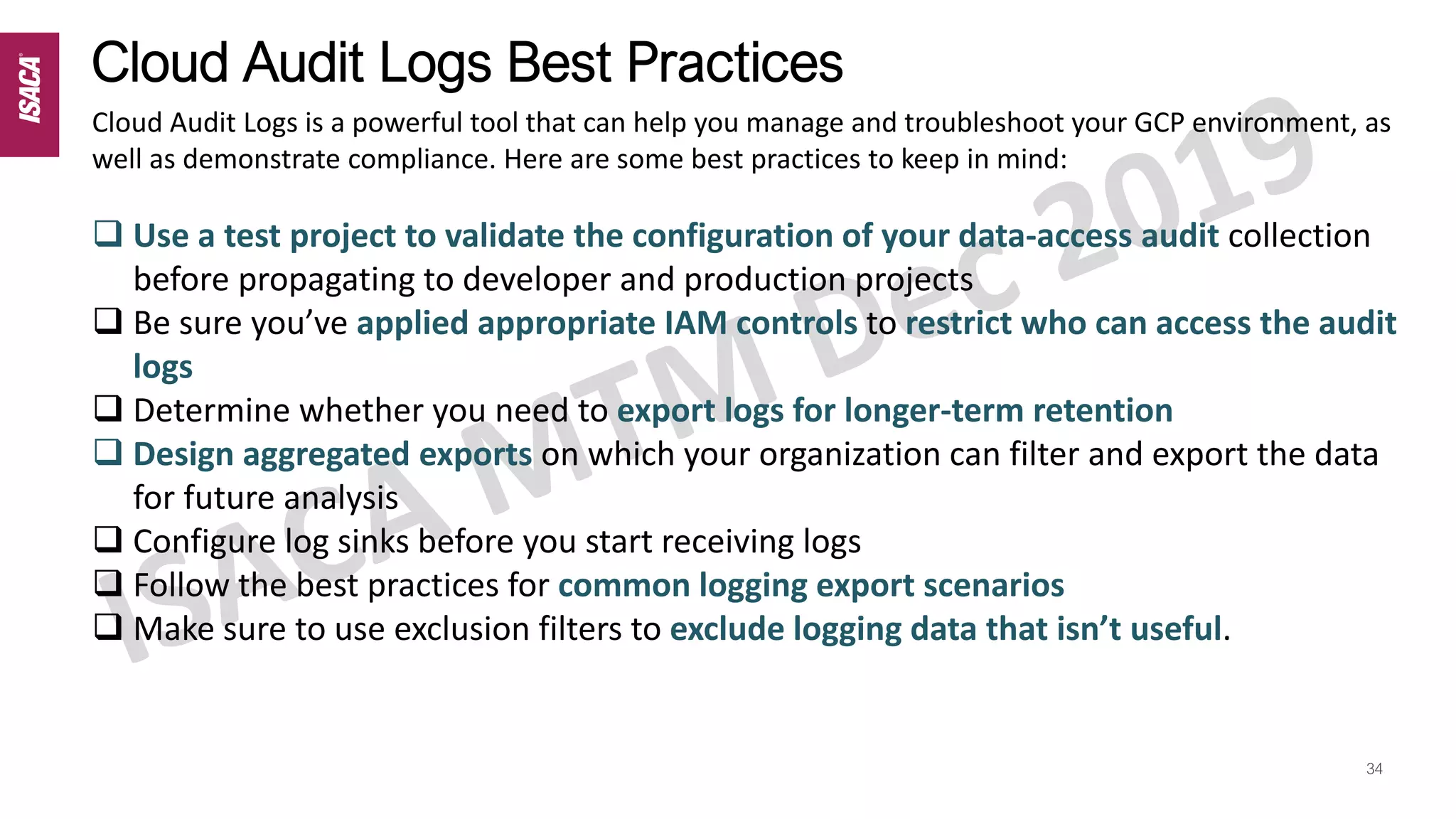
The document discusses cloud auditing by detailing risks, responsibilities, and essential characteristics of various cloud service models (IaaS, PaaS, SaaS). It emphasizes the importance of understanding shared responsibilities in cloud security, governance, and the necessity for auditors to grasp different audit methodologies depending on the service model used. Additionally, it highlights critical areas of focus and relevant standards for cloud security auditing.