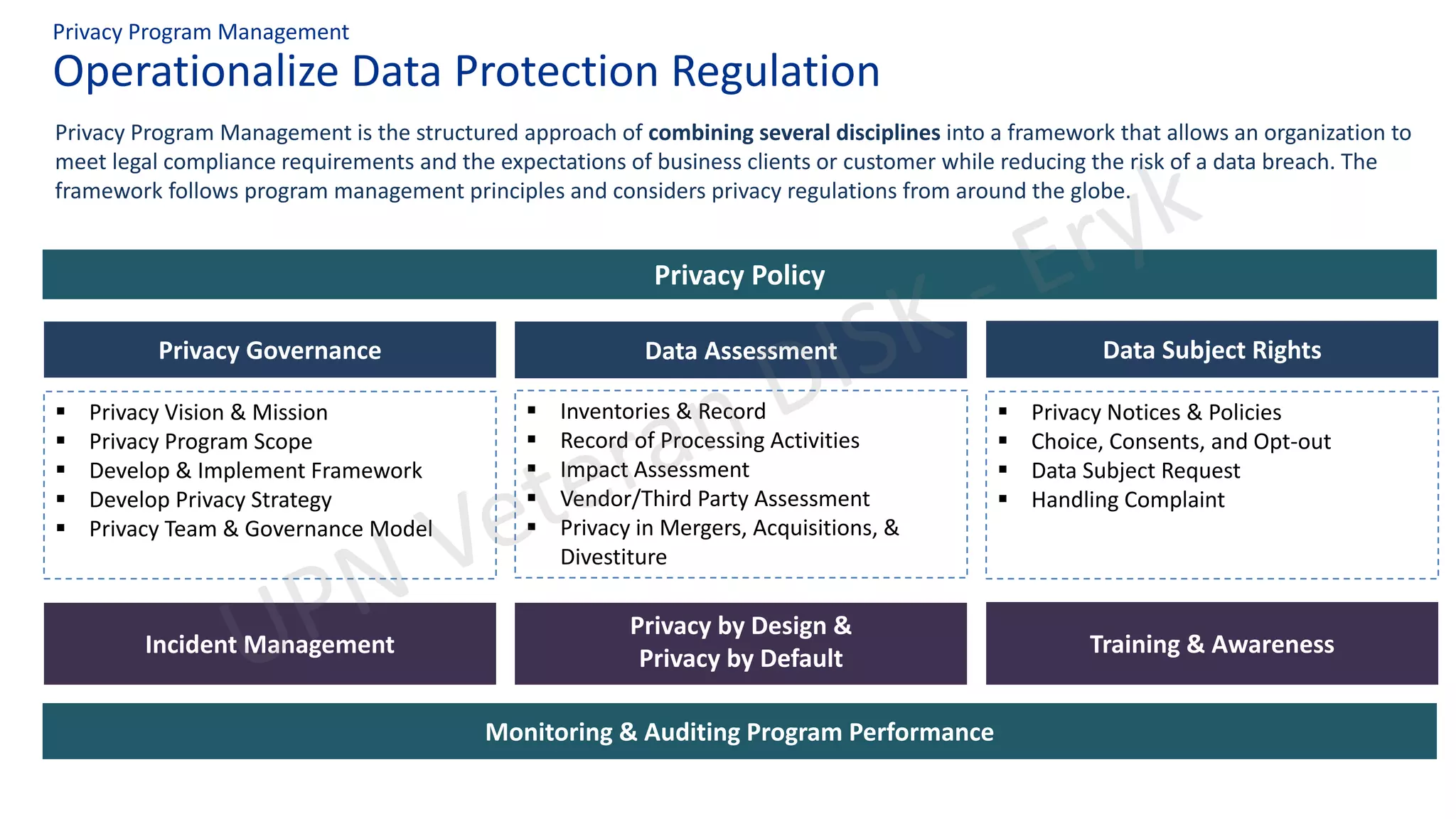
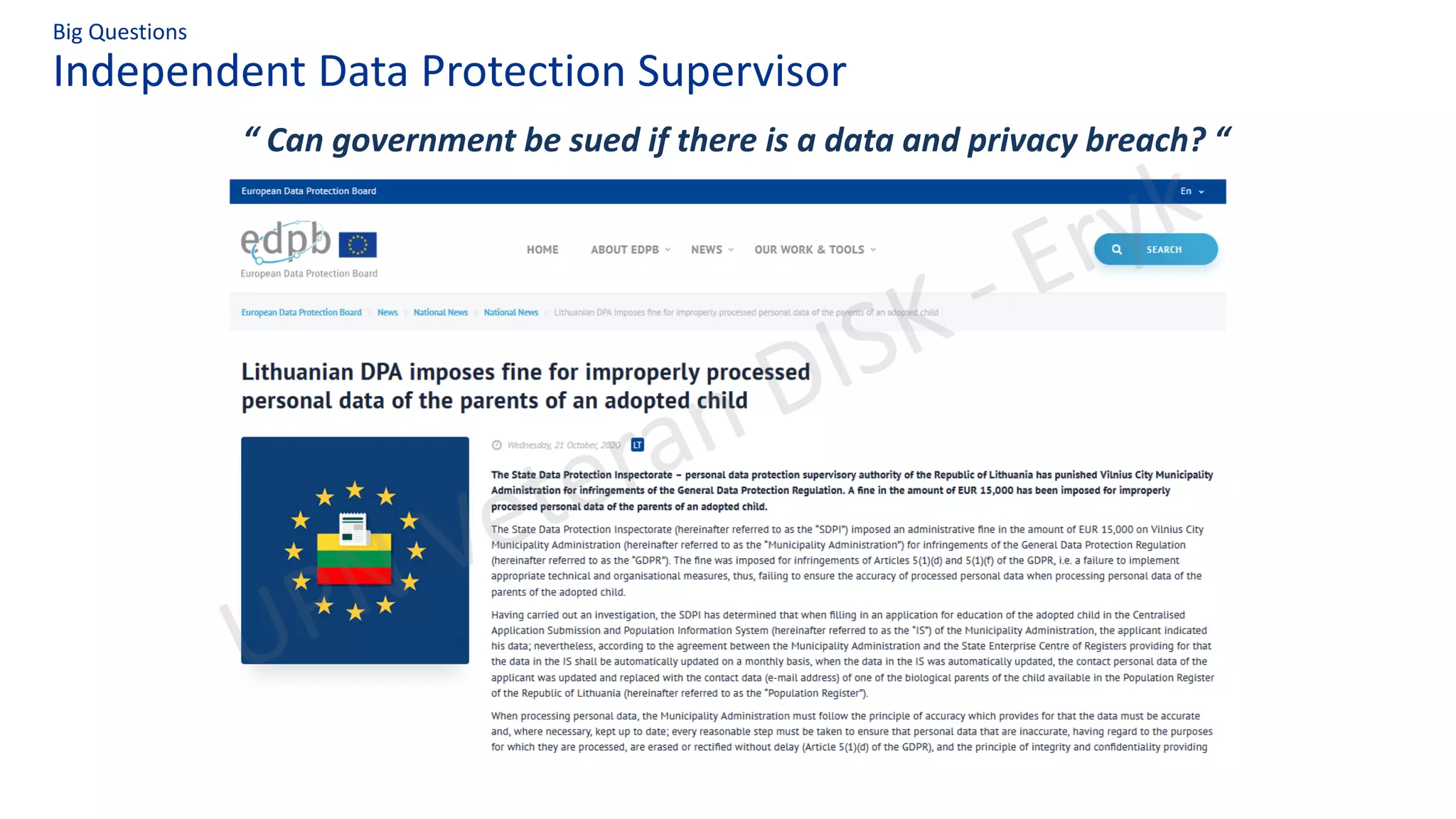
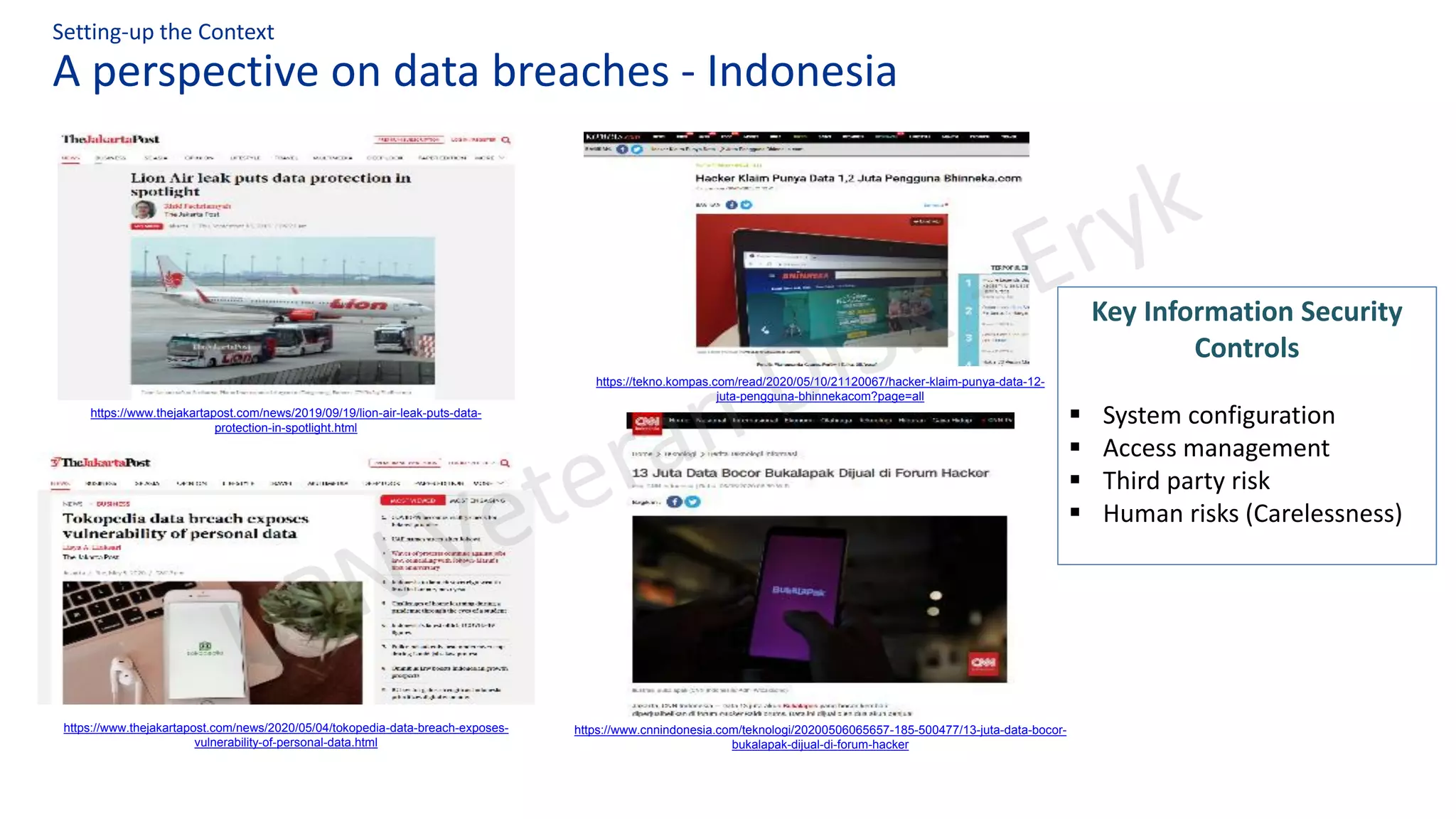
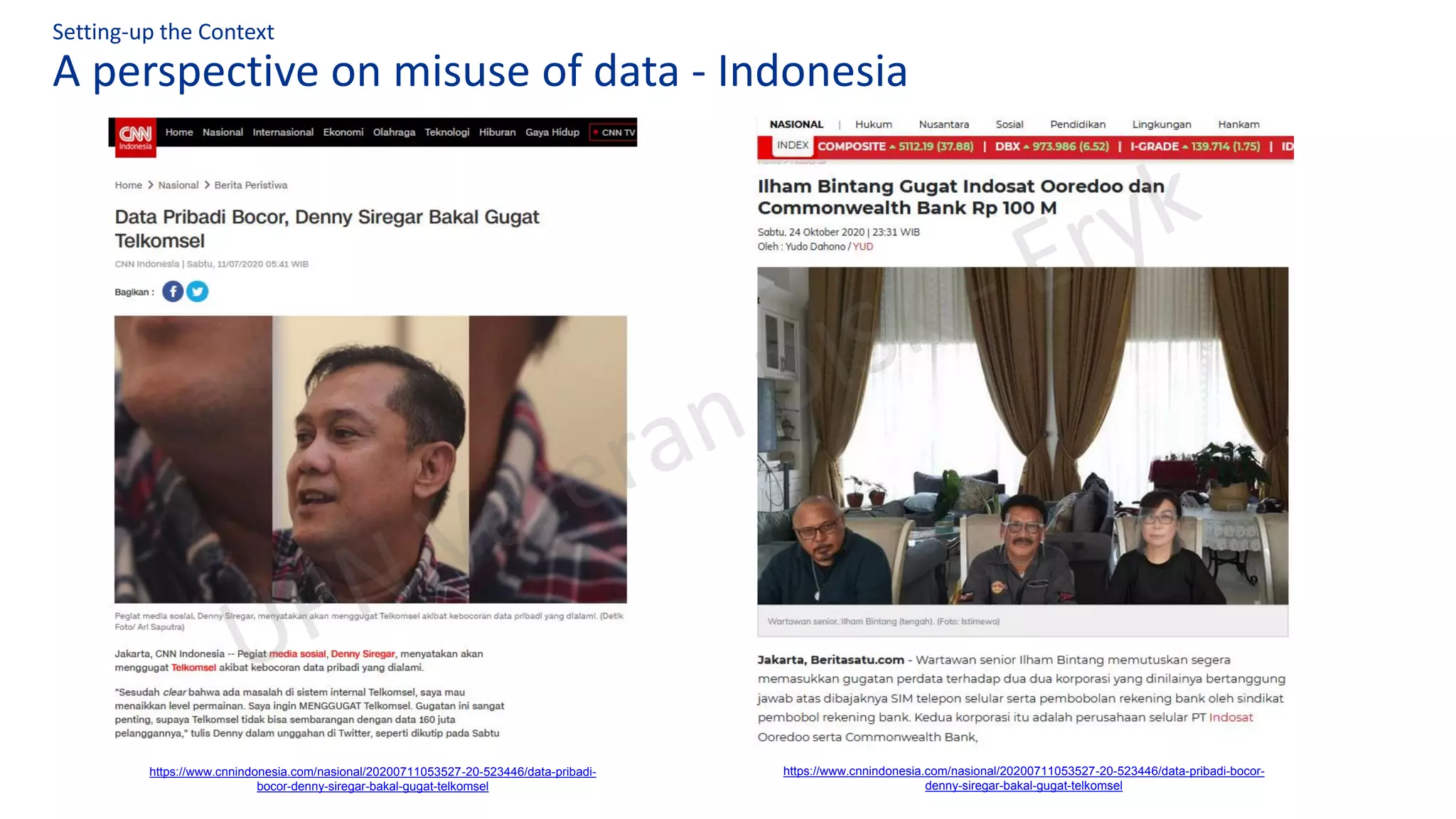
This document summarizes key aspects of Indonesia's draft Personal Data Protection Bill, including definitions of data controllers, processors, and protection officers. It outlines their obligations around data collection, security, breach reporting and subject rights. Common GDPR non-compliance issues are also discussed. The document emphasizes operationalizing privacy programs through frameworks addressing areas like policies, assessments, training and incident response. It raises questions around independent oversight and government accountability for data breaches.


![Common Mistakes in Data Privacy – GDPR Enforcement [SAMPLE]
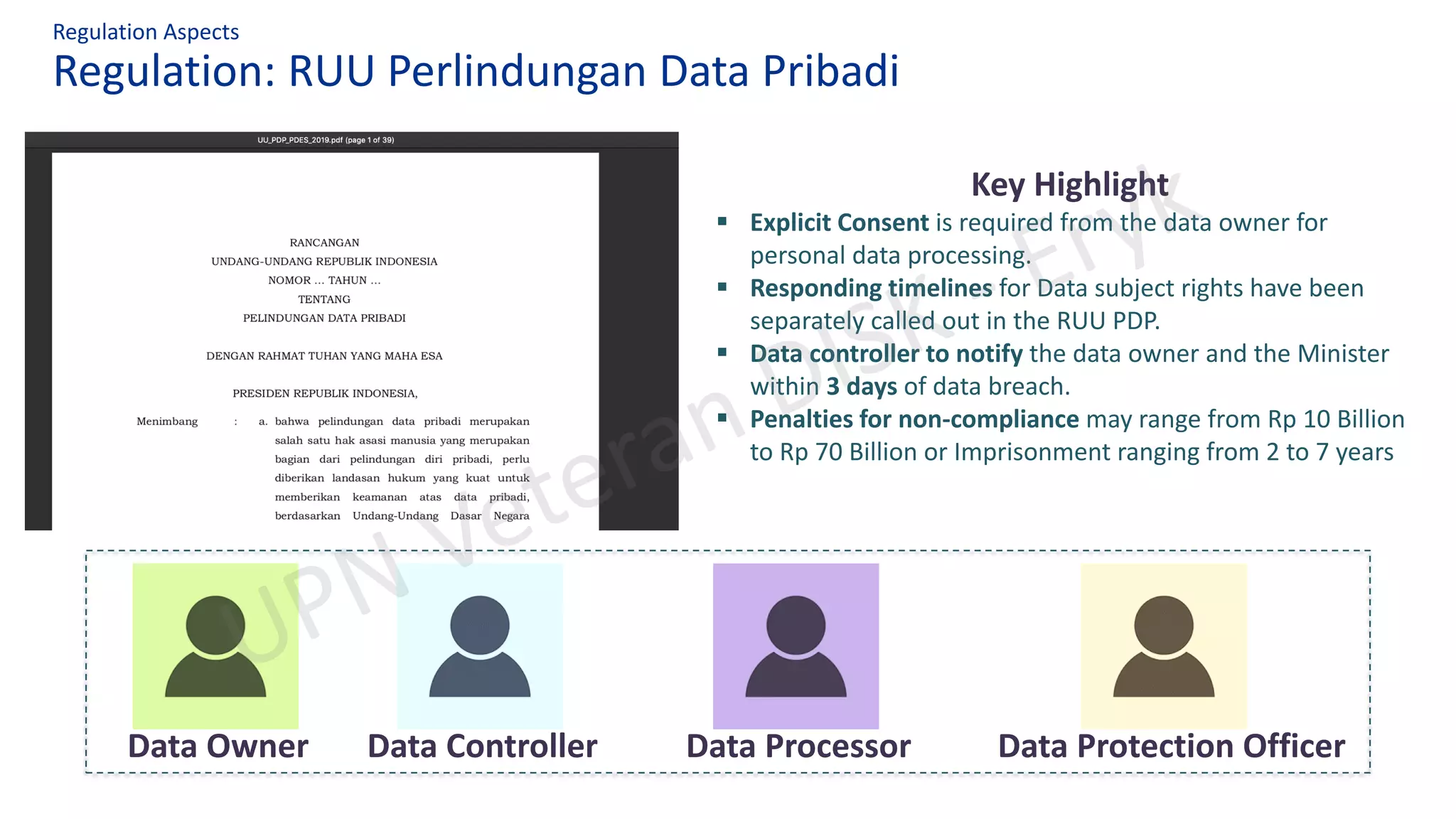
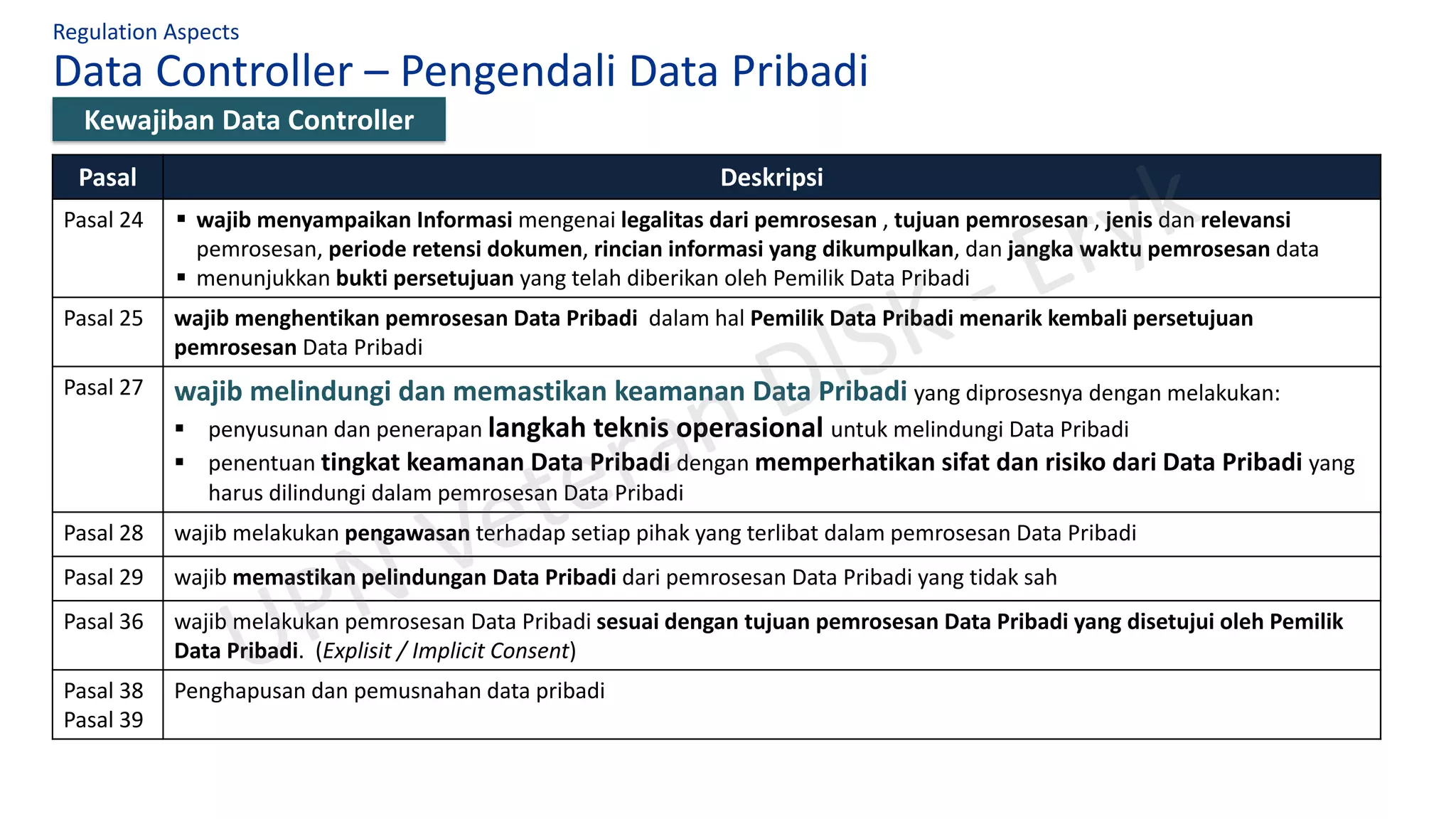
Regulation Aspects
https://www.enforcementtracker.com/
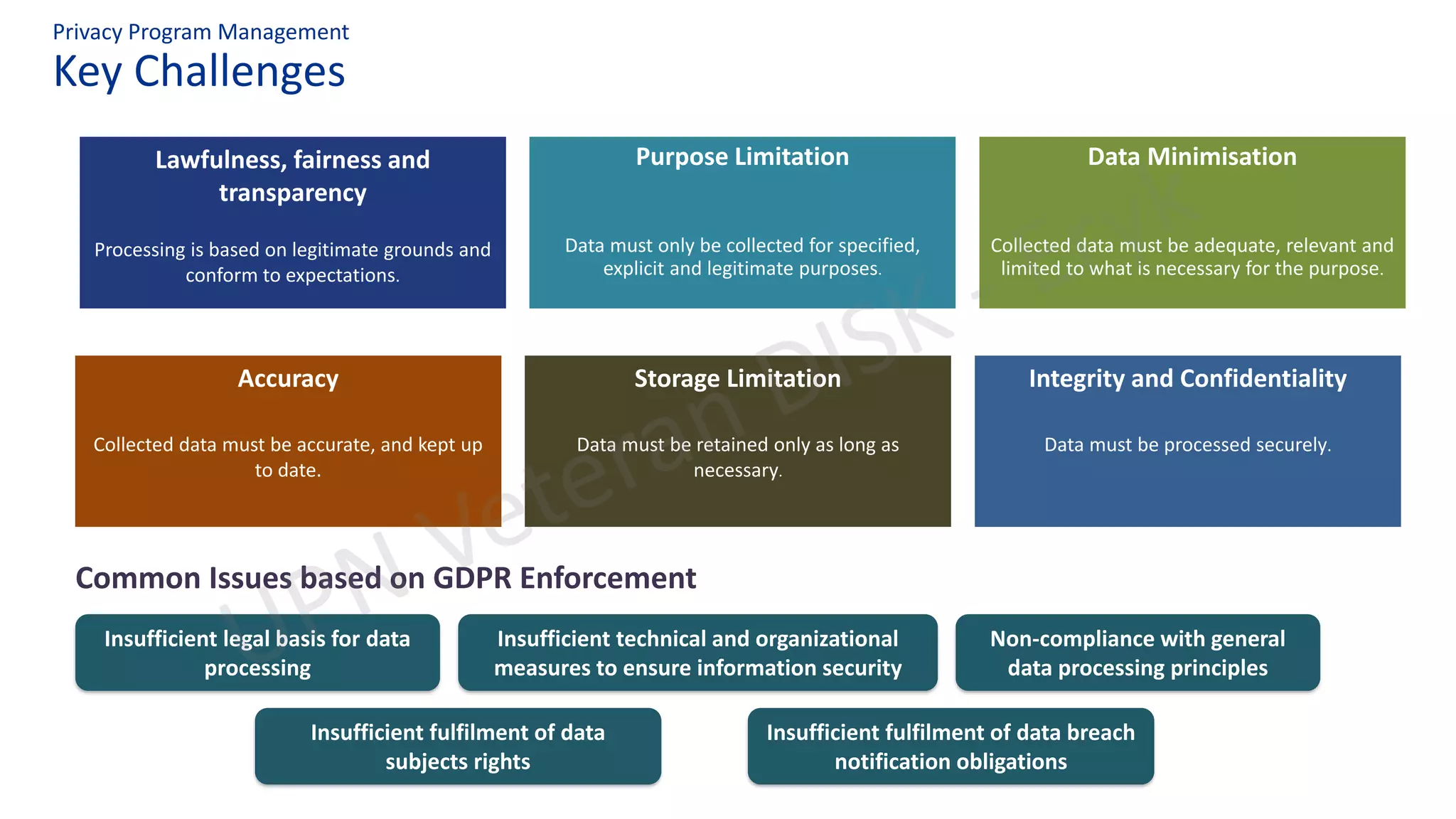
Common Issues
▪ Insufficient legal basis for data
processing
▪ Insufficient technical and organizational
measures to ensure information
security
▪ Non-compliance with general data
processing principles
▪ Insufficient fulfilment of data subjects
rights
▪ Insufficient fulfilment of information
obligations
▪ Insufficient fulfilment of data breach
notification obligations
▪ Insufficient cooperation with supervisory
authority](https://image.slidesharecdn.com/upnveterandisk-ruupdpurgencypublic-201031150318/75/Urgensi-RUU-Perlindungan-Data-Pribadi-10-2048.jpg)