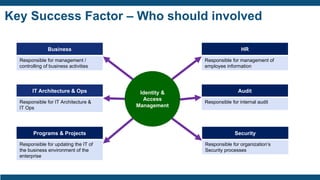
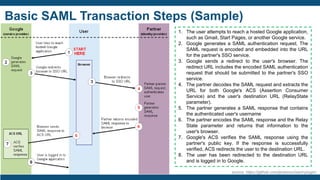
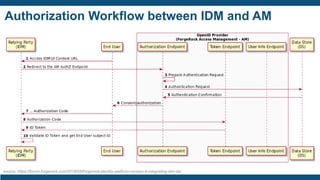
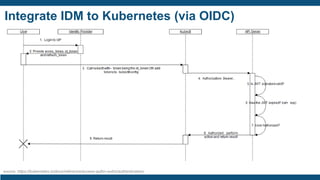
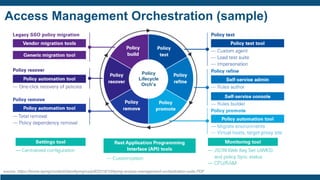
The document discusses identity and access management (IAM) for securing the DevOps lifecycle. It covers key aspects of IAM including:
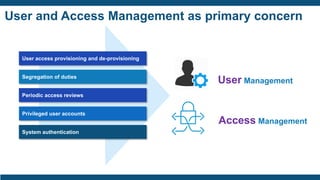
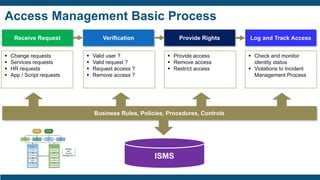
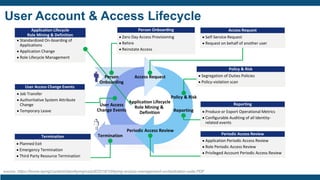
- User access provisioning and de-provisioning, periodic access reviews, privileged user accounts, and segregation of duties being primary concerns.
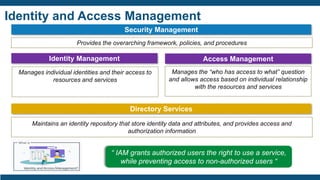
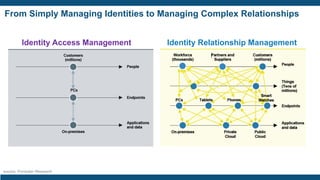
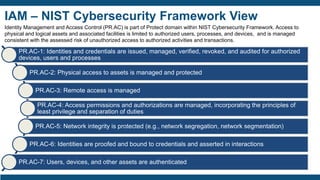
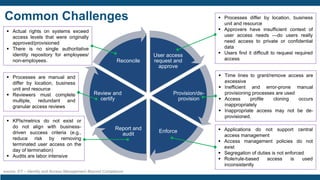
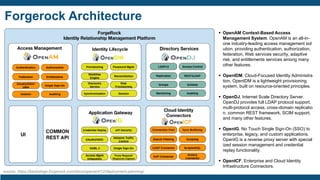
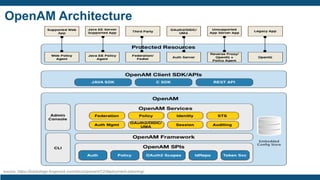
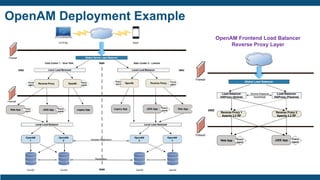
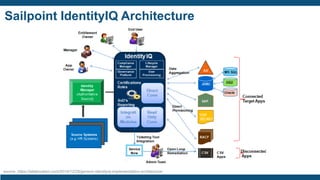
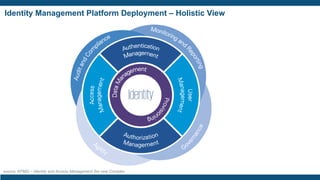
- The importance of IAM foundations like identity management, access management, directory services, and managing complex identity relationships rather than just identities.
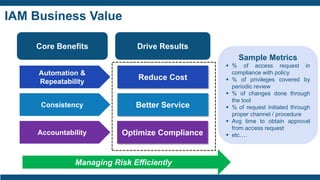
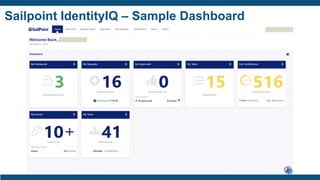
- Business values of IAM like automation, consistency, accountability, reduced costs, better service, and optimized compliance.
- Drivers for IAM investments like security, compliance with regulations, and improving productivity.
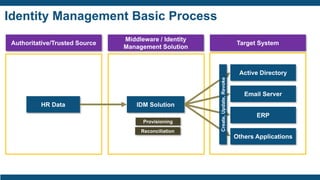
- The IAM lifecycle including identity management, access management, provisioning,





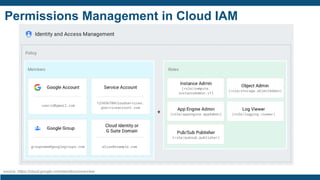

![Case Study – Identity Management Platform Deployment
Insurance Company
Challenge
Approach
Deliverable
— Leading global insurance company, had a number of outstanding audit points arising from the lack of visibility into “who has
access to what”. The client, in order to address these audit points, embarked on an Identity and Access Management programme in XXXX
that saw the replacement of their existing legacy automated provisioning tool with a strategic Identity Management platform. This project involved the
management of 5000 users and covered the on-boarding of 35 business critical applications.
— [Consultant] was selected to help the client deploy the strategic Identity Management platform.
— [Consultant] followed an access governance led approach to the deployment i.e; authoritative source data was reconciled prior to applications
being on-boarded. Entitlement review was conducted across all on-boarded applications.
— Once periodic entitlement reviews were instituted as a BAU process, the platform was further enhanced to support access requests and Joiner,
Movers and Leavers policies.
— Business and IT roles were on-boarded to conduct role based certifications for specific applications.
— [Consultant] helped with the remediation of orphan and dormant accounts, including the establishment of unique identifiers for every identity
record.
— The project was successfully transitioned to deployment support after the deployment of core functionality.
— [Consultant] put together a multi location support team to help the client consolidate the functionality built and to support the continued roll-out of the
platform across their application estate.
— Delivery of a comprehensive strategic user access programme that is supported by all divisions within the organization and satisfies
the regulator.
— A clear vision of the target state and practical implementation phases for sustained growth.
— A multi location support team to help consolidate the functionality built and to support the continued roll-out of the platform across application estate.](https://image.slidesharecdn.com/identityaccessmanagementforsecuringdevopserykshare-191114154949/85/Identity-Access-Management-for-Securing-DevOps-35-320.jpg)
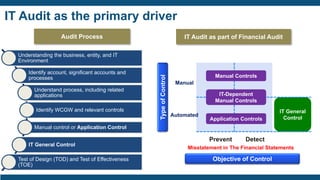
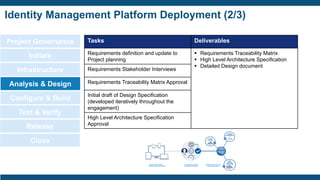
![Identity Management Platform Deployment (1/3)
Project Governance
Initiate
Infrastructure
Analysis & Design
Configure & Build
Test & Verify
Release
Close
Tasks Deliverables
Baseline [Tools] install in
development environment
▪ Infrastructure Validation Host Instance
Diagrams
▪ Baseline [Tools] Installation in
Development Environment
▪ [Tools] environment ready for Test and
Verification
Source repository configured with a
Standard Build Environment and tools.
Environment connection details captured
and documented.
Developer and system accounts created
Development, UAT, and Production
environments in place](https://image.slidesharecdn.com/identityaccessmanagementforsecuringdevopserykshare-191114154949/85/Identity-Access-Management-for-Securing-DevOps-37-320.jpg)
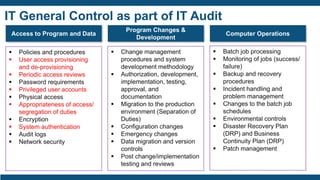
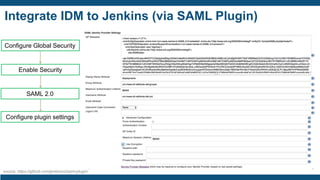
![Identity Management Platform Deployment (3/3)
Project Governance
Initiate
Infrastructure
Analysis & Design
Configure & Build
Test & Verify
Release
Close
Tasks Deliverables
Iterative updates to Design Specification ▪ Identity cubes built and populated
▪ Models and policies defined in [Tools]
▪ Workflows implemented
▪ Simple Branded Pages
▪ Build Guide Established
▪ All configurations complete
Data loading
Load authoritative source
Load account and entitlement data
Correlate accounts to identities
Review orphans
Workflow definition
Policy modeling
Create Build Guide (UAT)
Configuration of access certifications
Development of rule libraries
General configuration of reporting, and dashboard
Pass-Through Authentication / SSO Configuration
Simple Branding
Preparation of UAT-ready system](https://image.slidesharecdn.com/identityaccessmanagementforsecuringdevopserykshare-191114154949/85/Identity-Access-Management-for-Securing-DevOps-39-320.jpg)