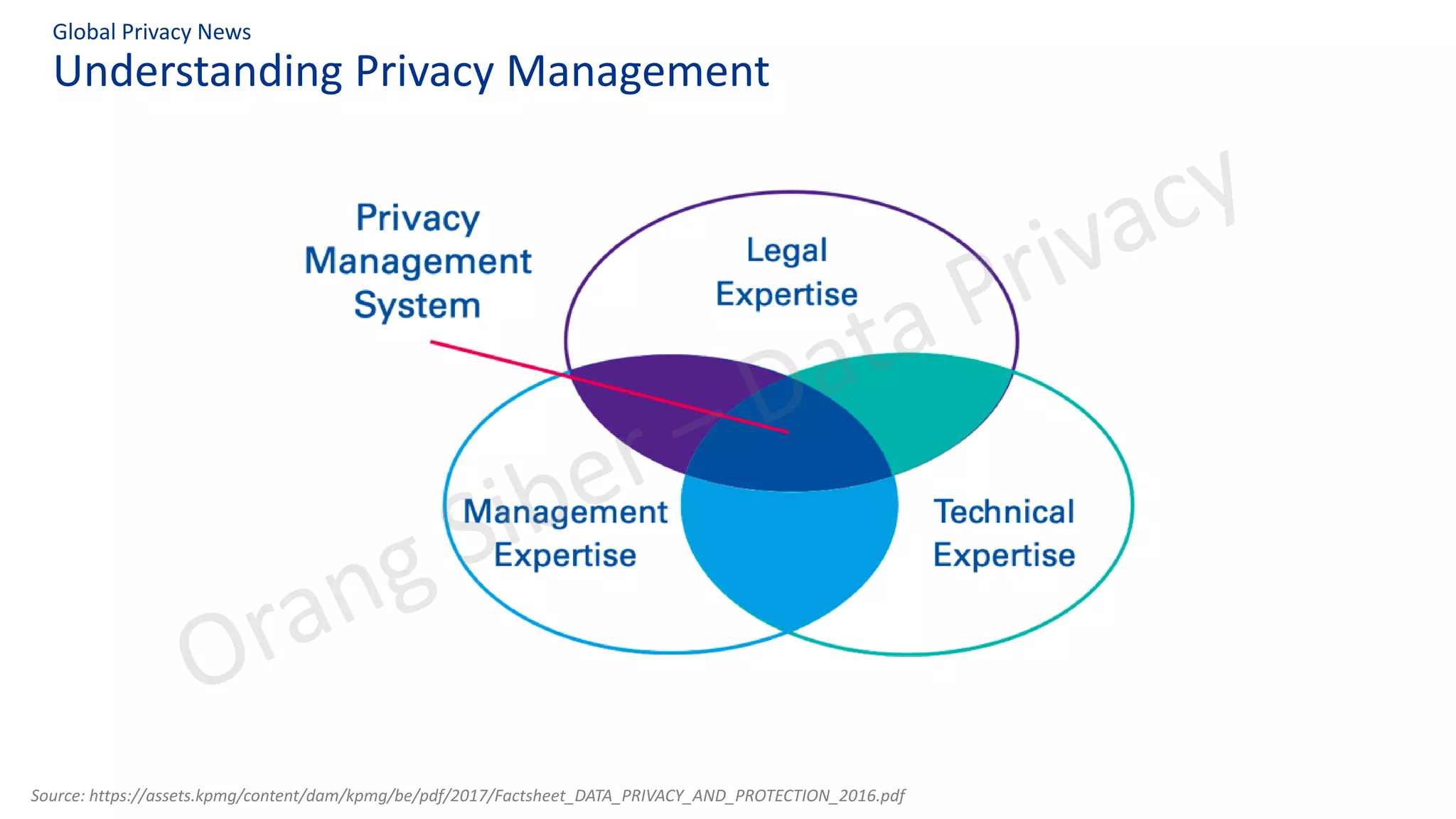
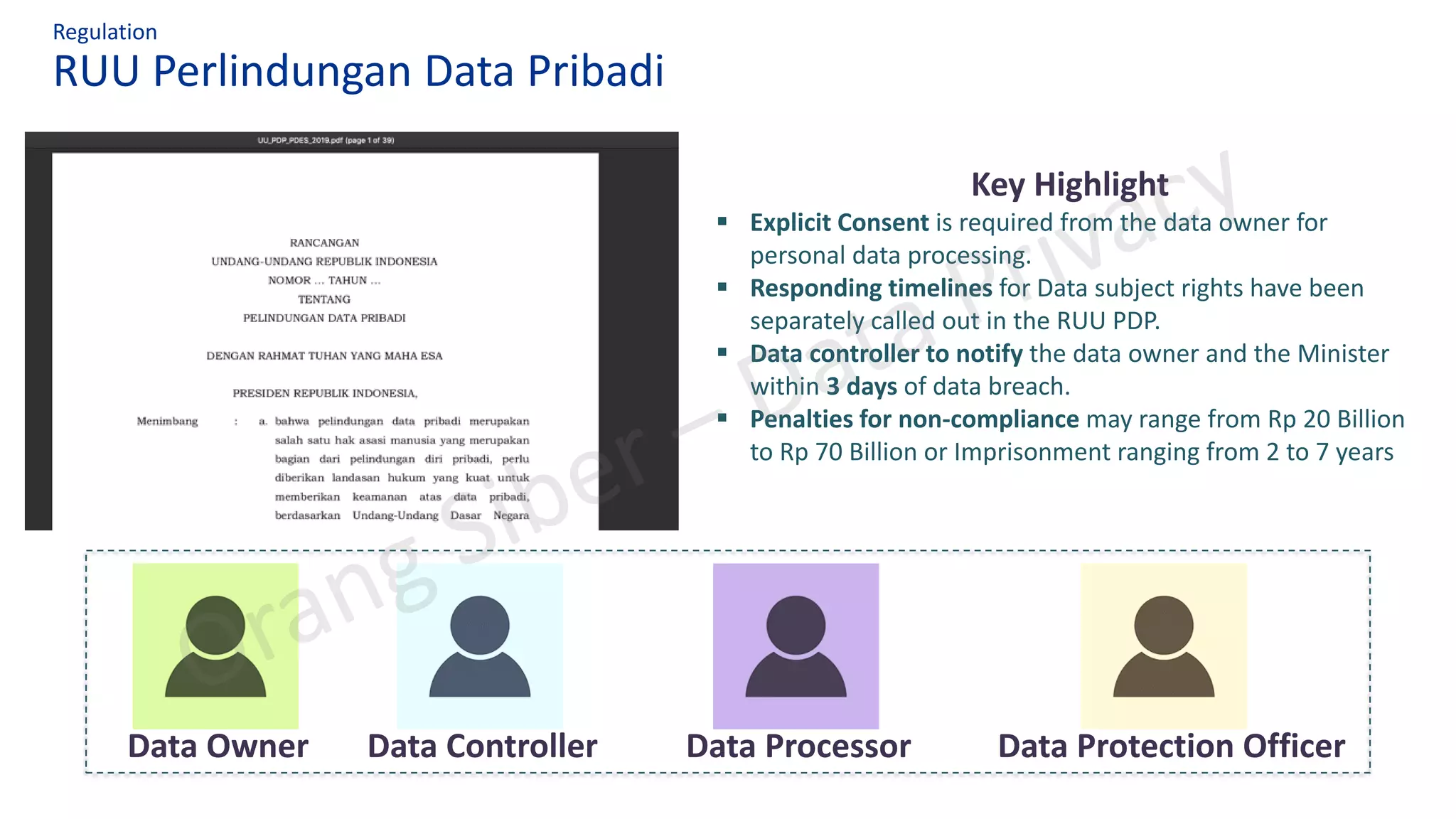
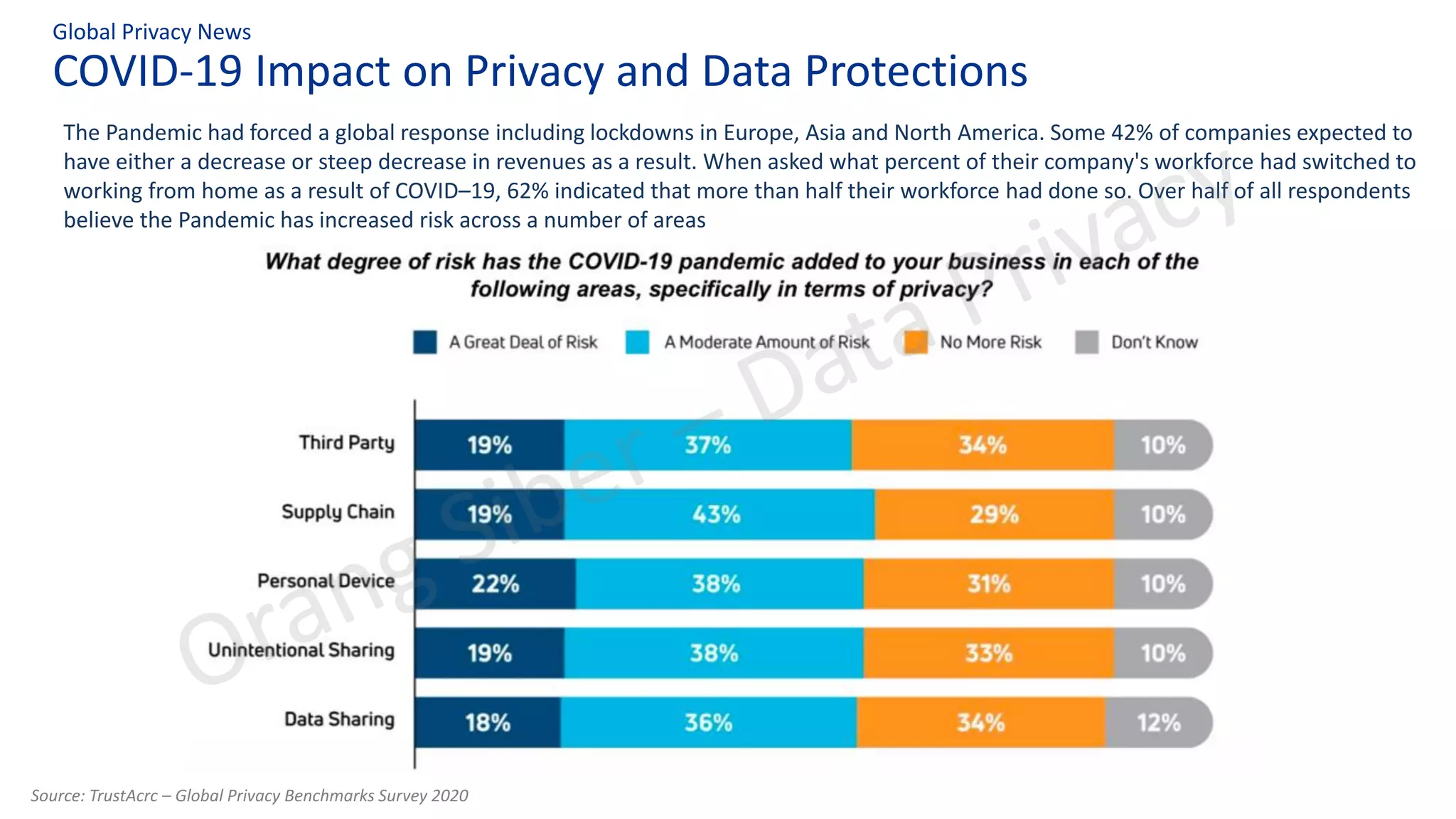
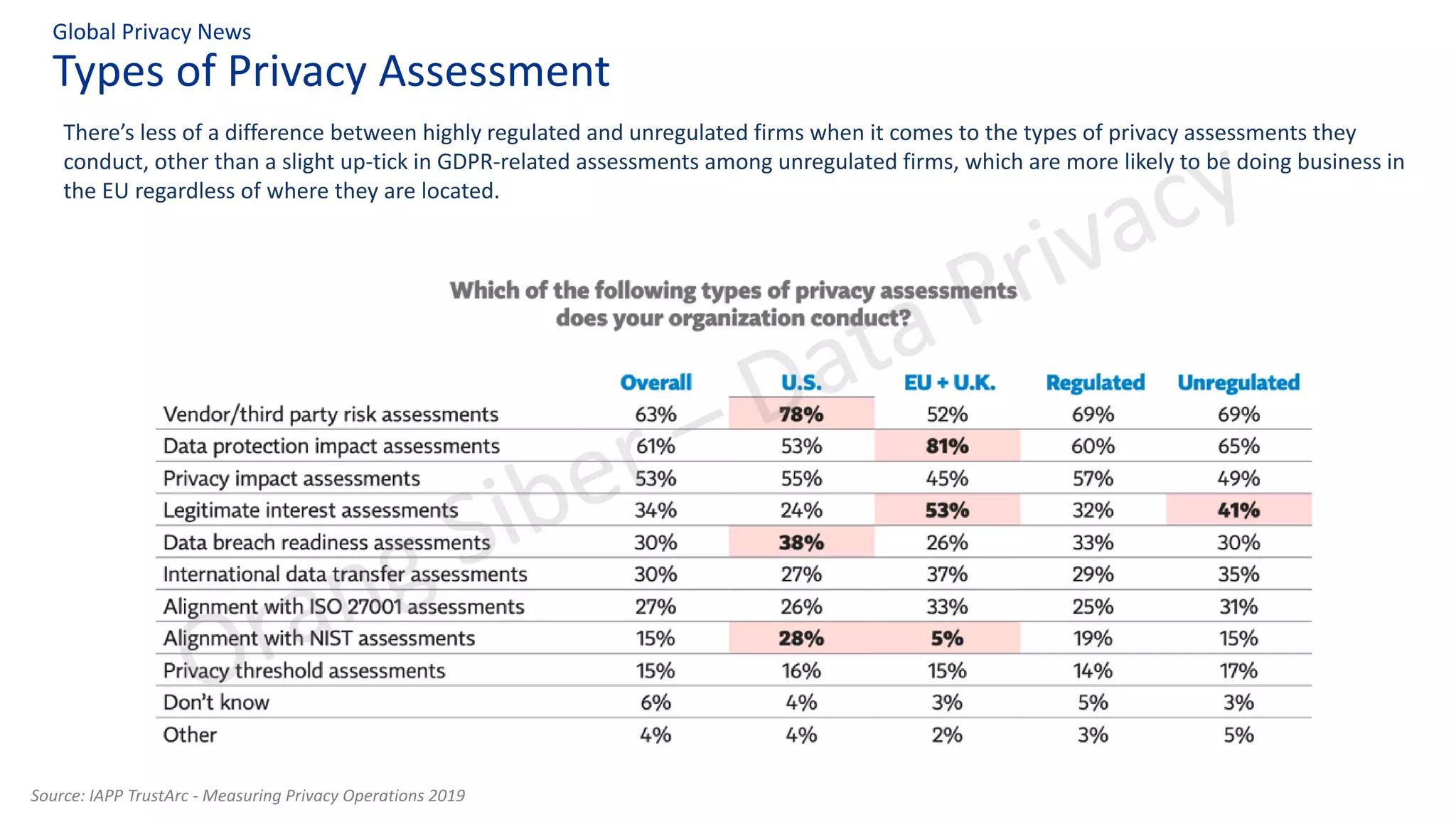
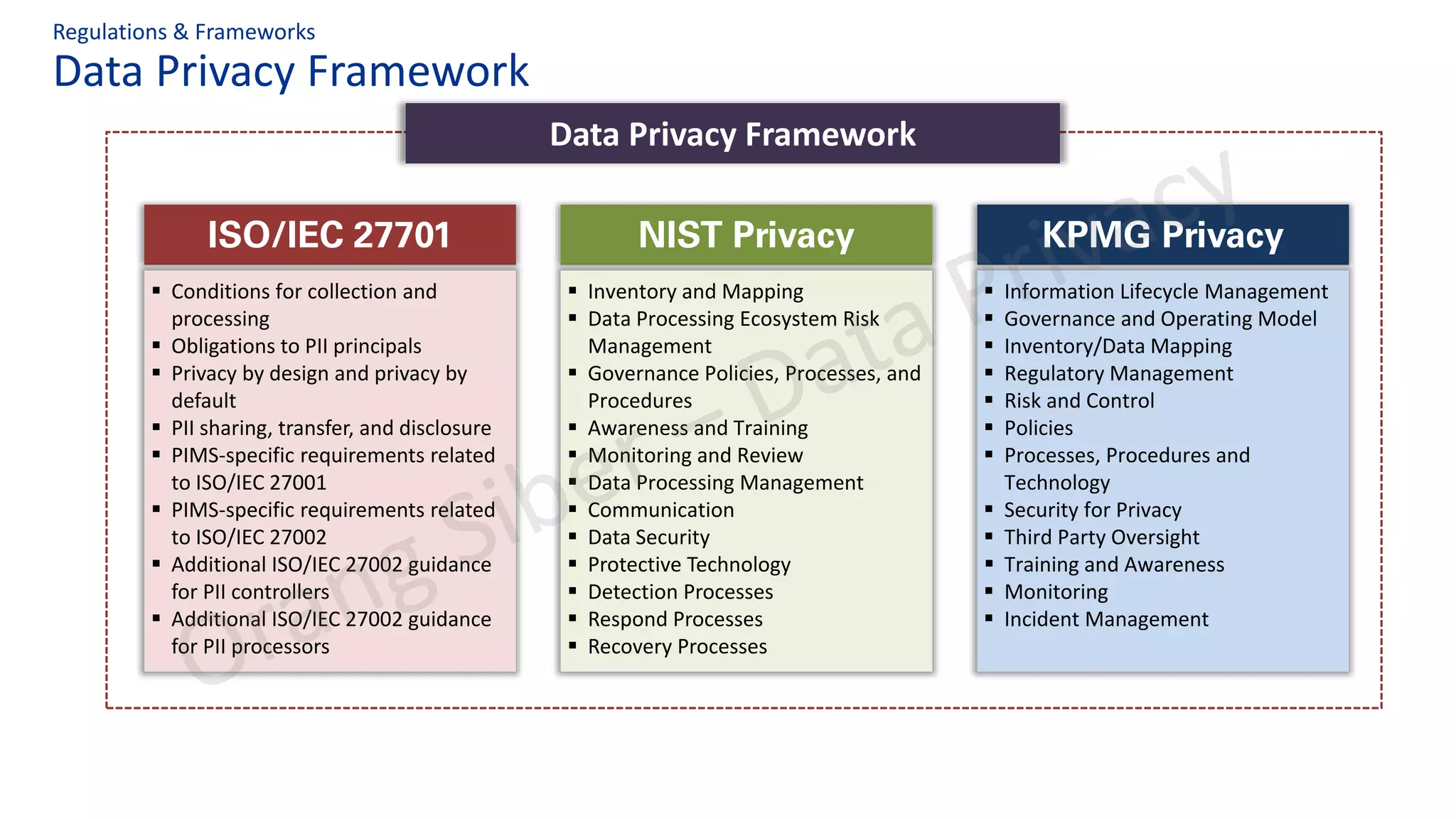
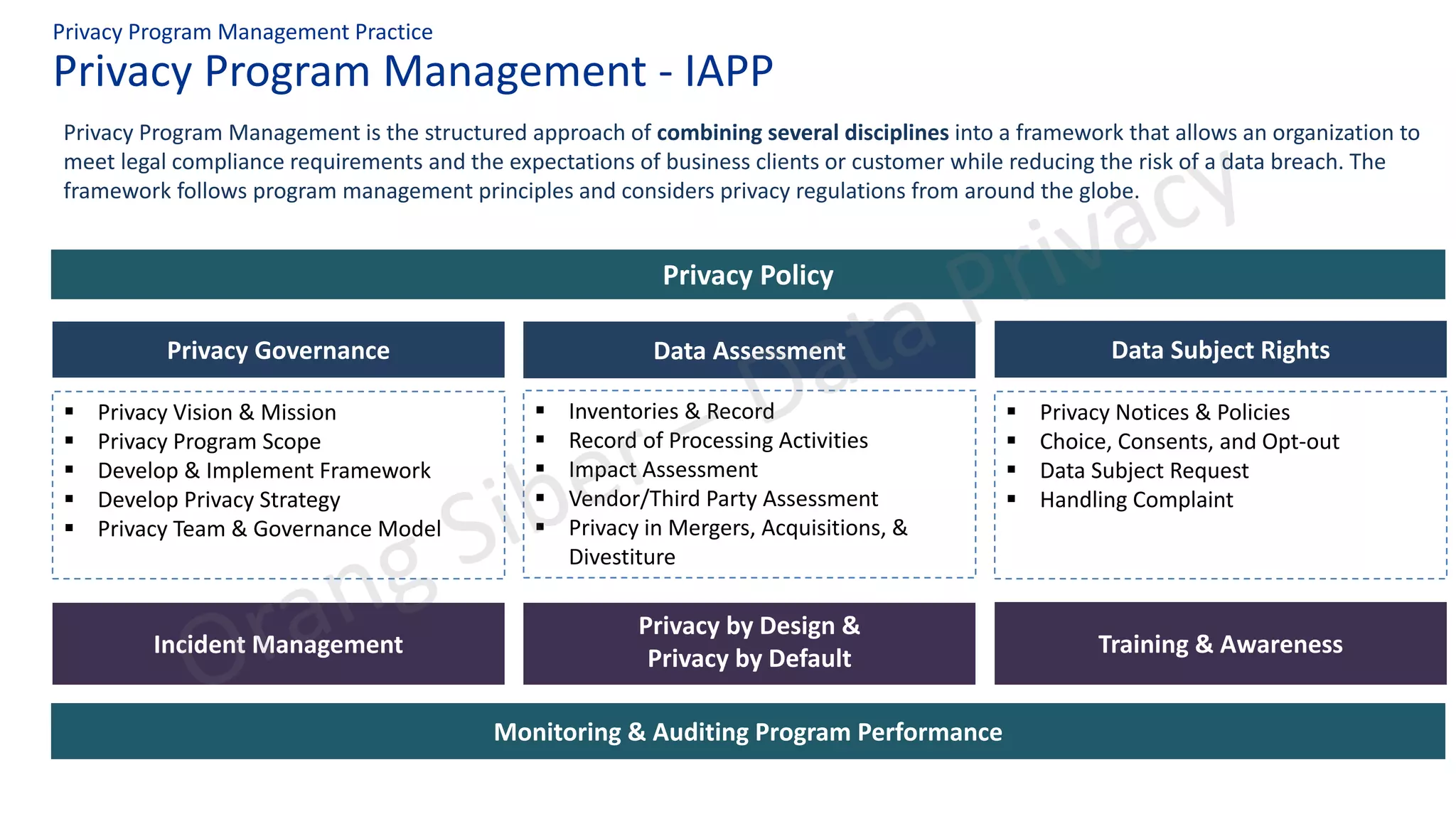
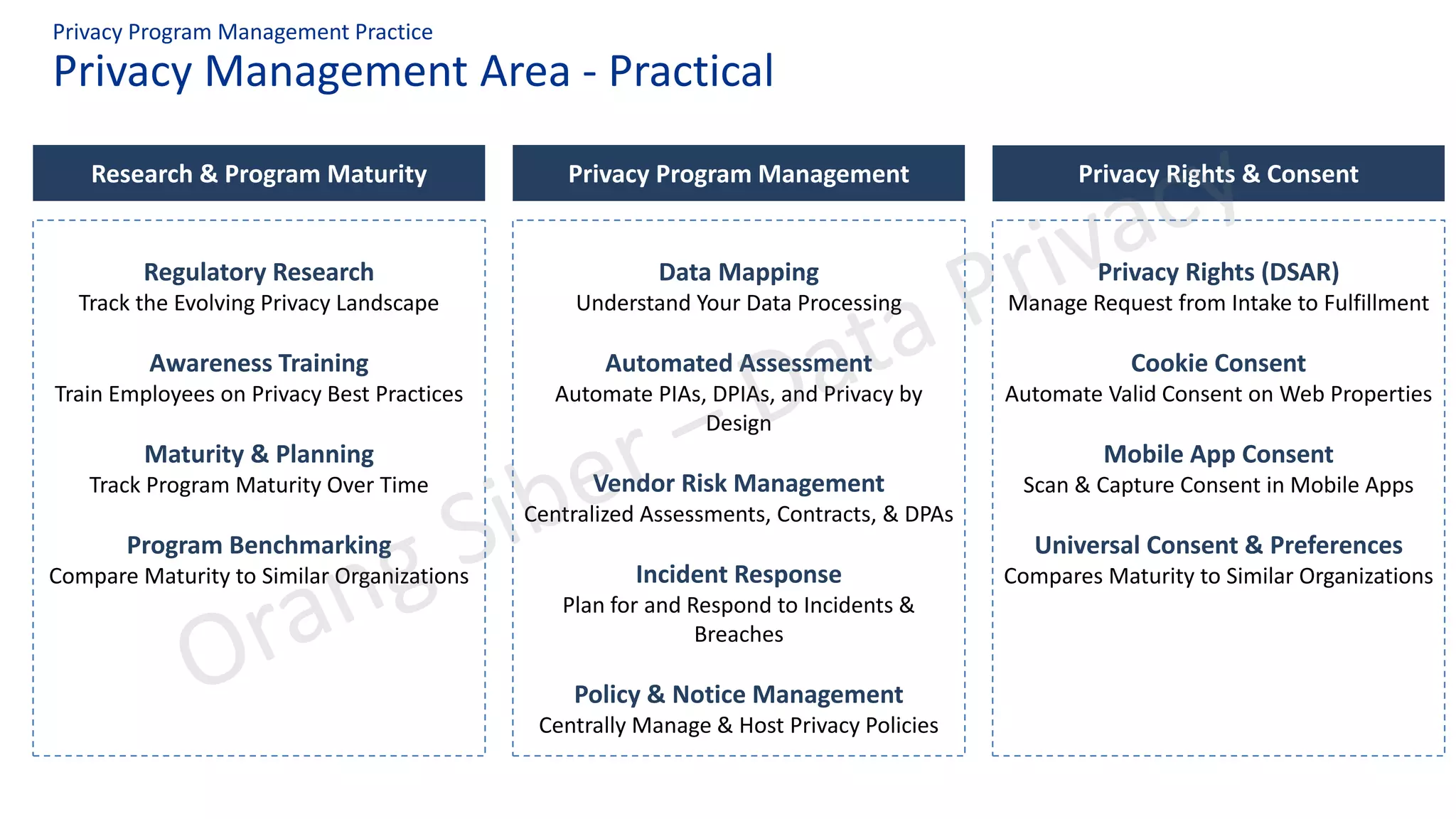
The document discusses best practices in data privacy program management, highlighting key regulatory requirements such as the necessity of explicit consent for personal data processing and penalties for non-compliance. It explores the impact of COVID-19 on privacy and data protection, noting increased risks and shifts to remote work. Additionally, it outlines a structured approach to privacy management, incorporating frameworks to ensure legal compliance and reduce data breach risks.