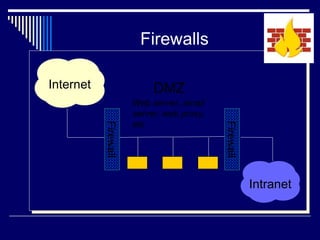
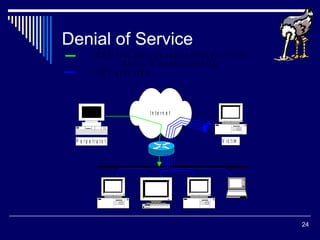
Internet security involves protecting systems and data from unauthorized access. Common security threats include hacking, viruses, phishing, and denial of service attacks. It is important for users to implement security measures like firewalls and keep software updated to prevent intrusions and thefts of personal information.