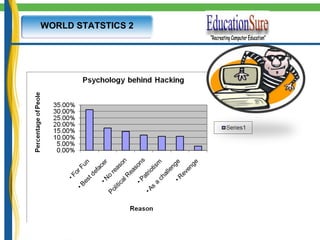
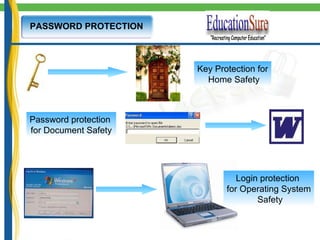
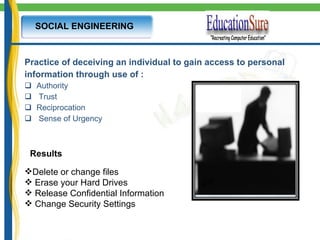
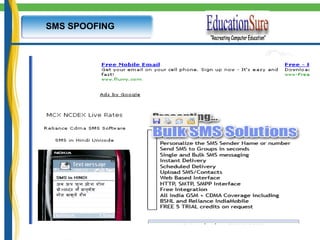
This document provides an introduction to IT security and ethical hacking. It discusses common online threats like theft of passwords and malware attacks. It emphasizes the need for security to protect valuable information. It also discusses social engineering, keyloggers, trojans, and phishing as common cybercrimes. Worldwide hacking incidents and statistics on cyber crimes are presented. Methods for password protection and dealing with security threats are outlined.




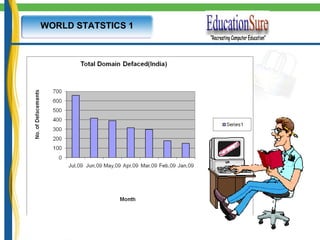











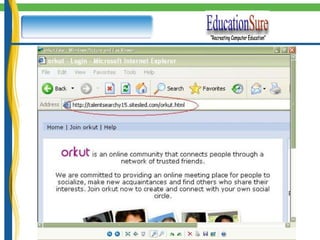


![NEW AGE CYBER CRIME How secure are India's call centres? Is information security becoming a casualty in India's booming call centres as they drive down costs to keep themselves competitive for foreign clients? [BBC NEWS NETWORK ] http://news.bbc.co.uk/1/hi/world/south_asia/4619859.stm](https://image.slidesharecdn.com/itsecurityethicalhacking-100715141139-phpapp02/85/It-security-_ethical_hacking-31-320.jpg)

![SPREADING TROJAN, VIRUS & WORMS Sends spoofed E-mail: [email_address] Computer A Receives E-mail from: [email_address] Computer B Computer B opens the attachment thinking it’s a security patch software Trojan Spyware Virus Worms Computer Crashed](https://image.slidesharecdn.com/itsecurityethicalhacking-100715141139-phpapp02/85/It-security-_ethical_hacking-34-320.jpg)