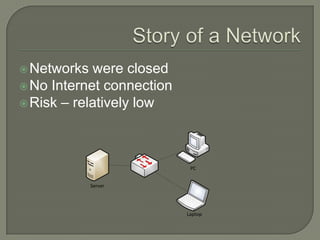
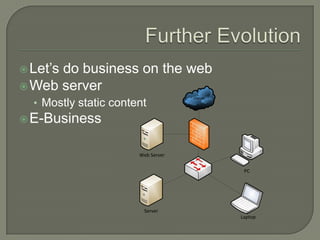
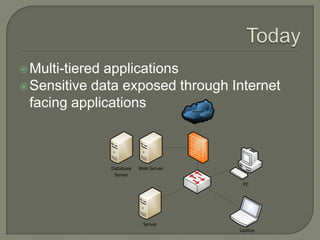
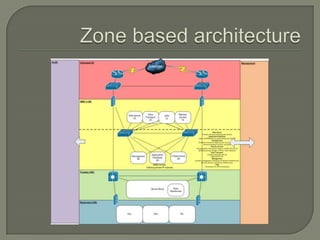
This document discusses the need for adopting an industry standard network security architecture model to improve security without unnecessary complexity. It outlines the evolution of typical network architectures from closed to increasingly open and exposed. This has introduced new threats that cannot be addressed by isolated security solutions alone. The document advocates aligning security controls according to well-defined architectural principles and business needs, and properly managing the integrated system as a whole.