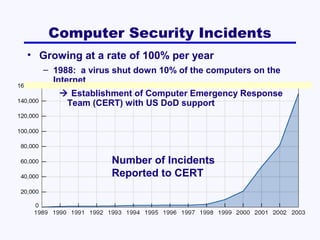
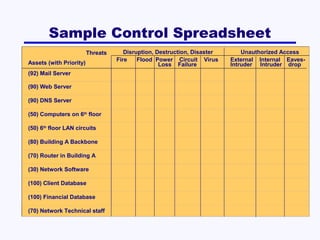
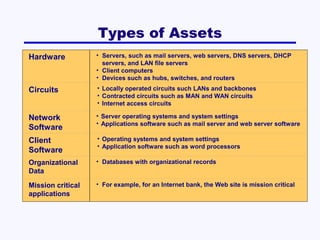
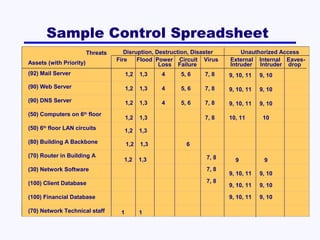
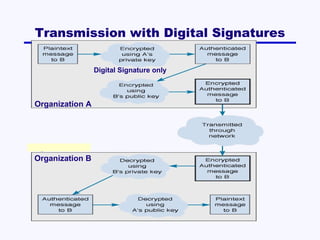
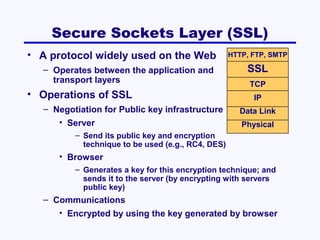
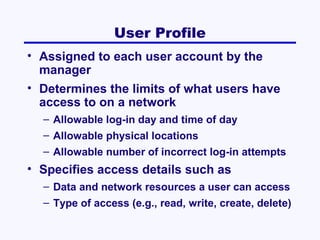
This document discusses network security. It covers risk assessment, controlling unauthorized access through prevention, detection and correction methods, and best practice recommendations. The key threats are disruption, destruction, unauthorized access and financial losses. Controls include firewalls, intrusion detection, access controls, encryption, and disaster recovery plans. The goals of security are confidentiality, integrity and availability of data and systems.