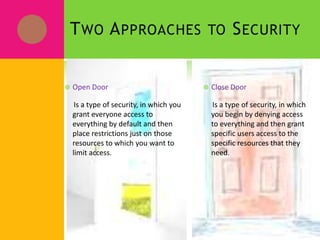
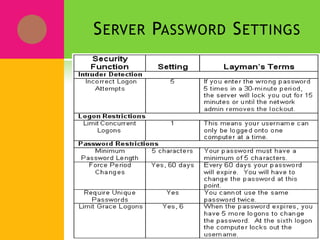
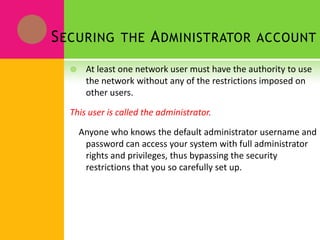
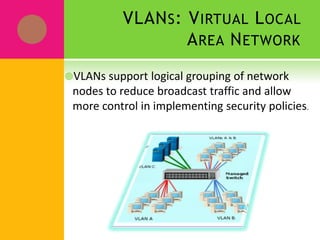
Network security involves protecting network assets and operations from threats like viruses, Trojan horses, and data interception. Key network security tools include antivirus software, firewalls, intrusion detection systems, VPNs, encryption, and identity services. There are two approaches to security - an open door approach that grants access by default and a close door approach that denies access by default. VLANs (Virtual Local Area Networks) logically group network nodes to reduce broadcast traffic and allow more granular security policies between groups.