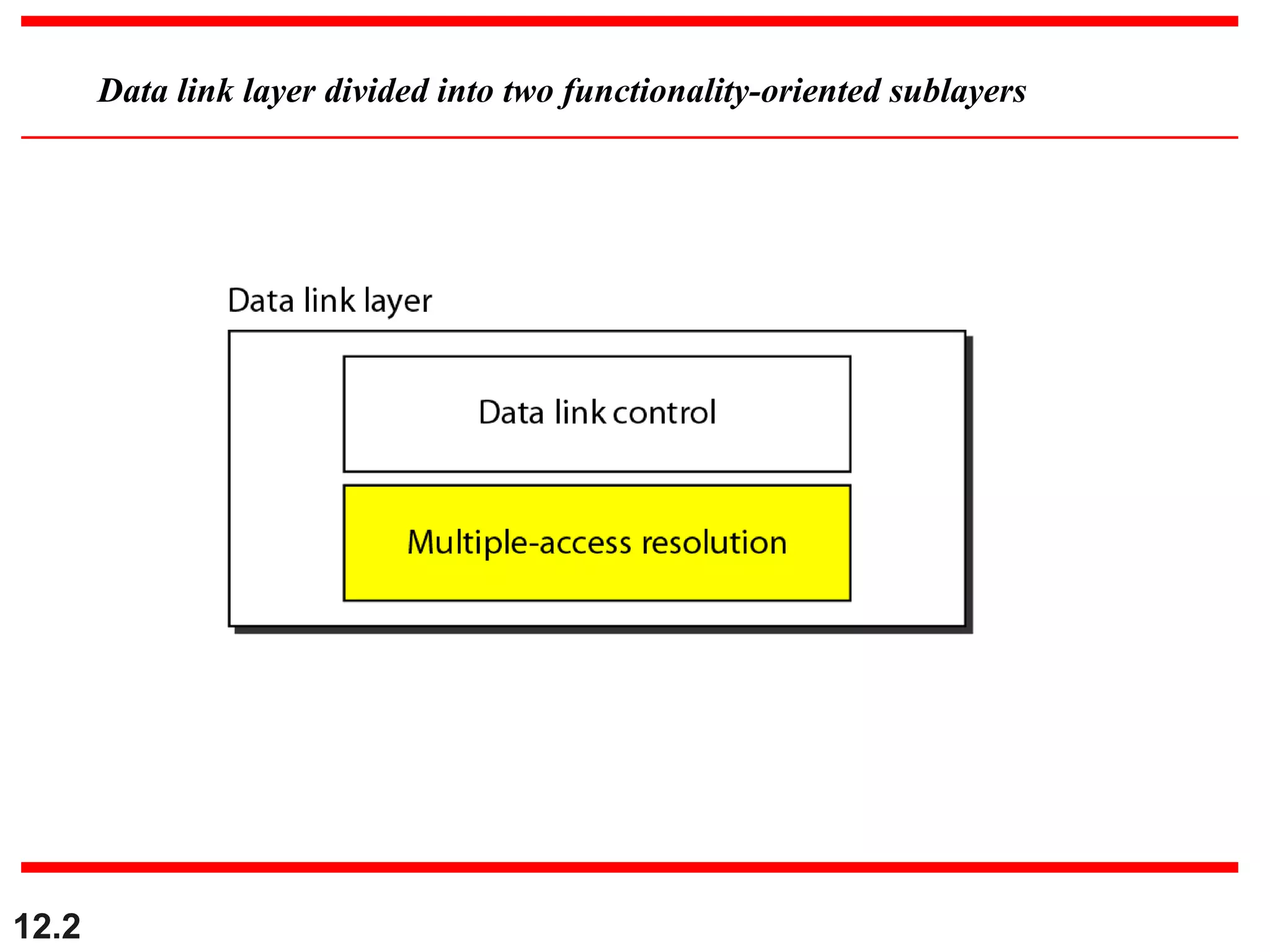
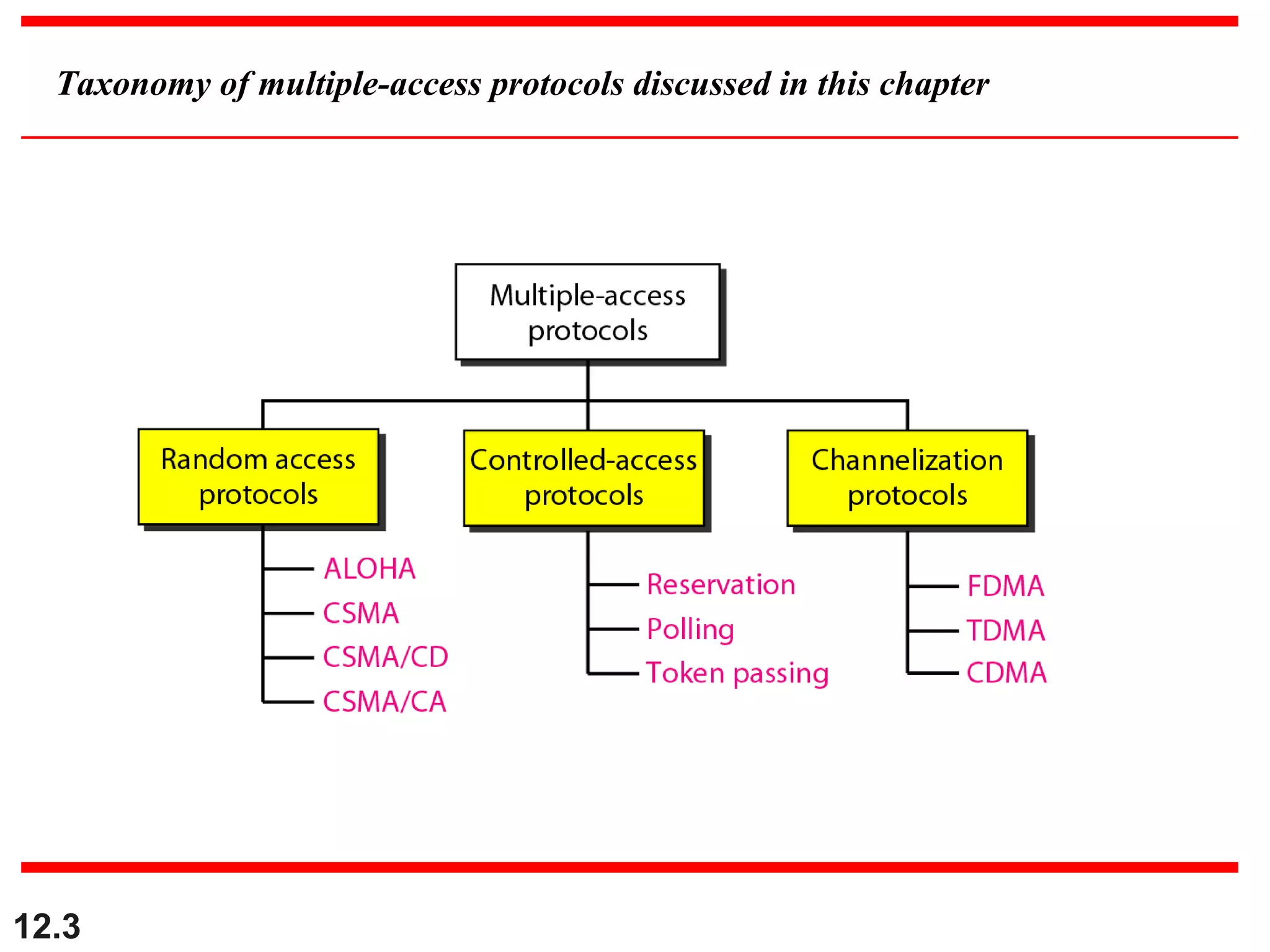
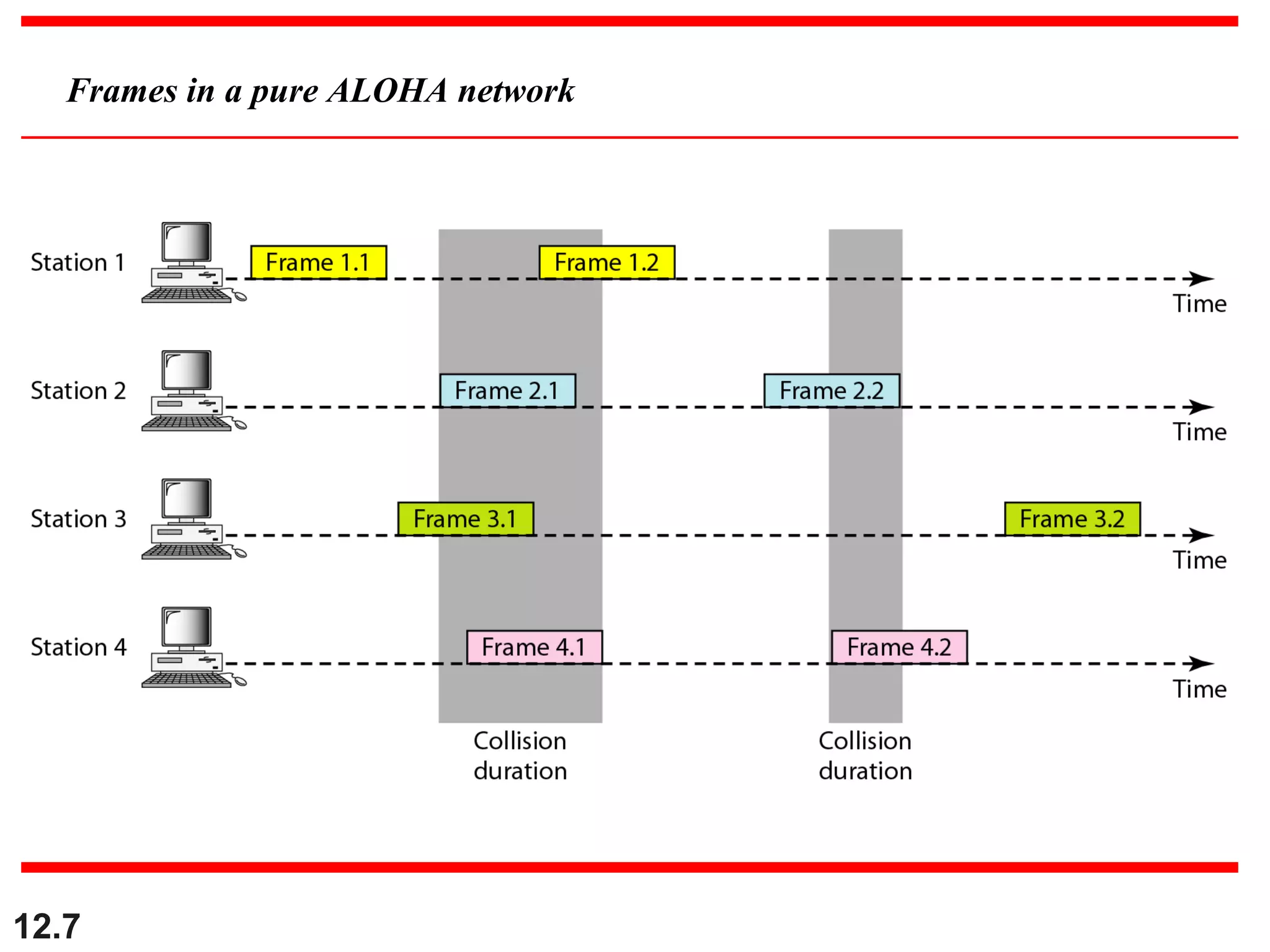
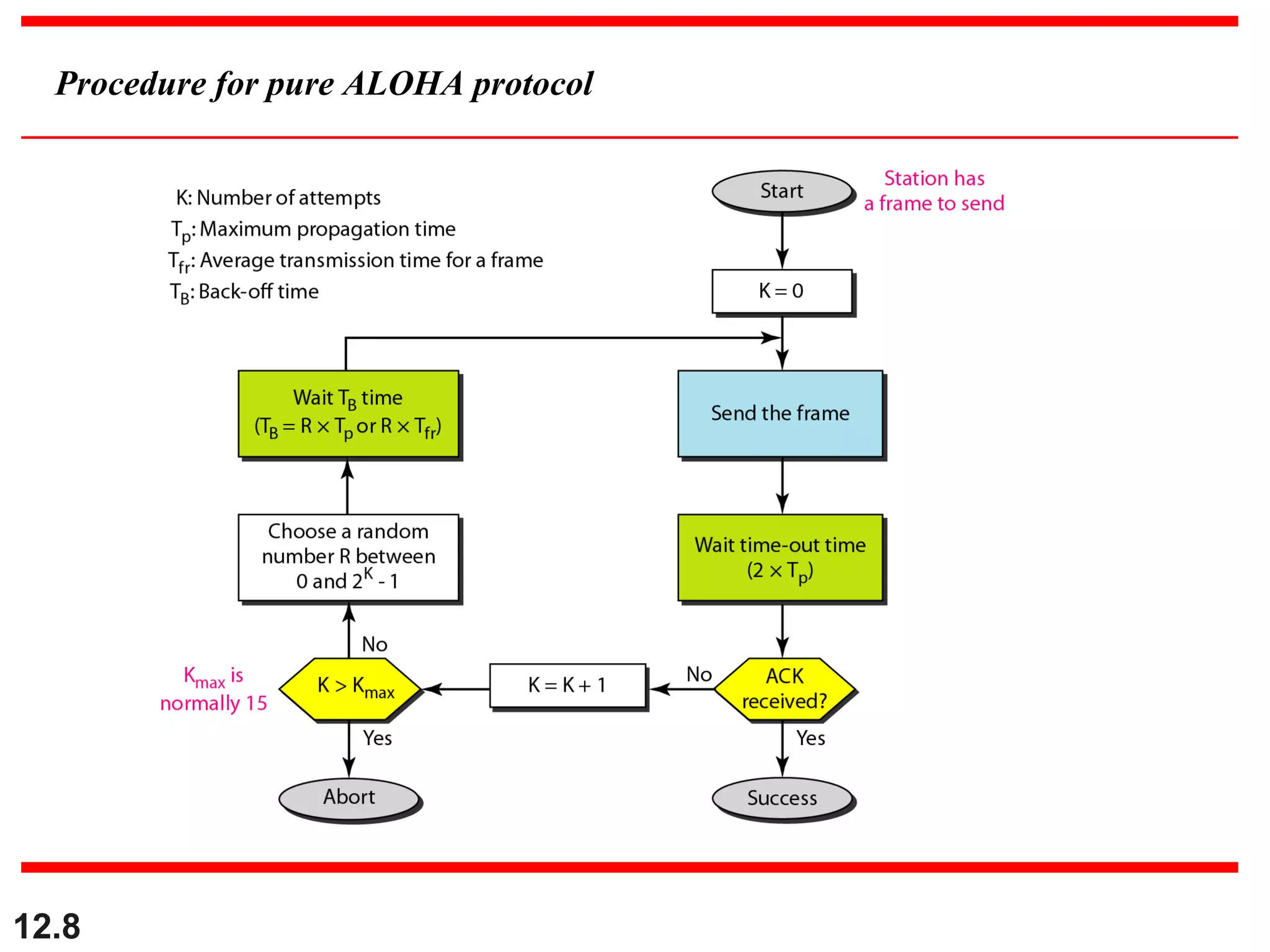
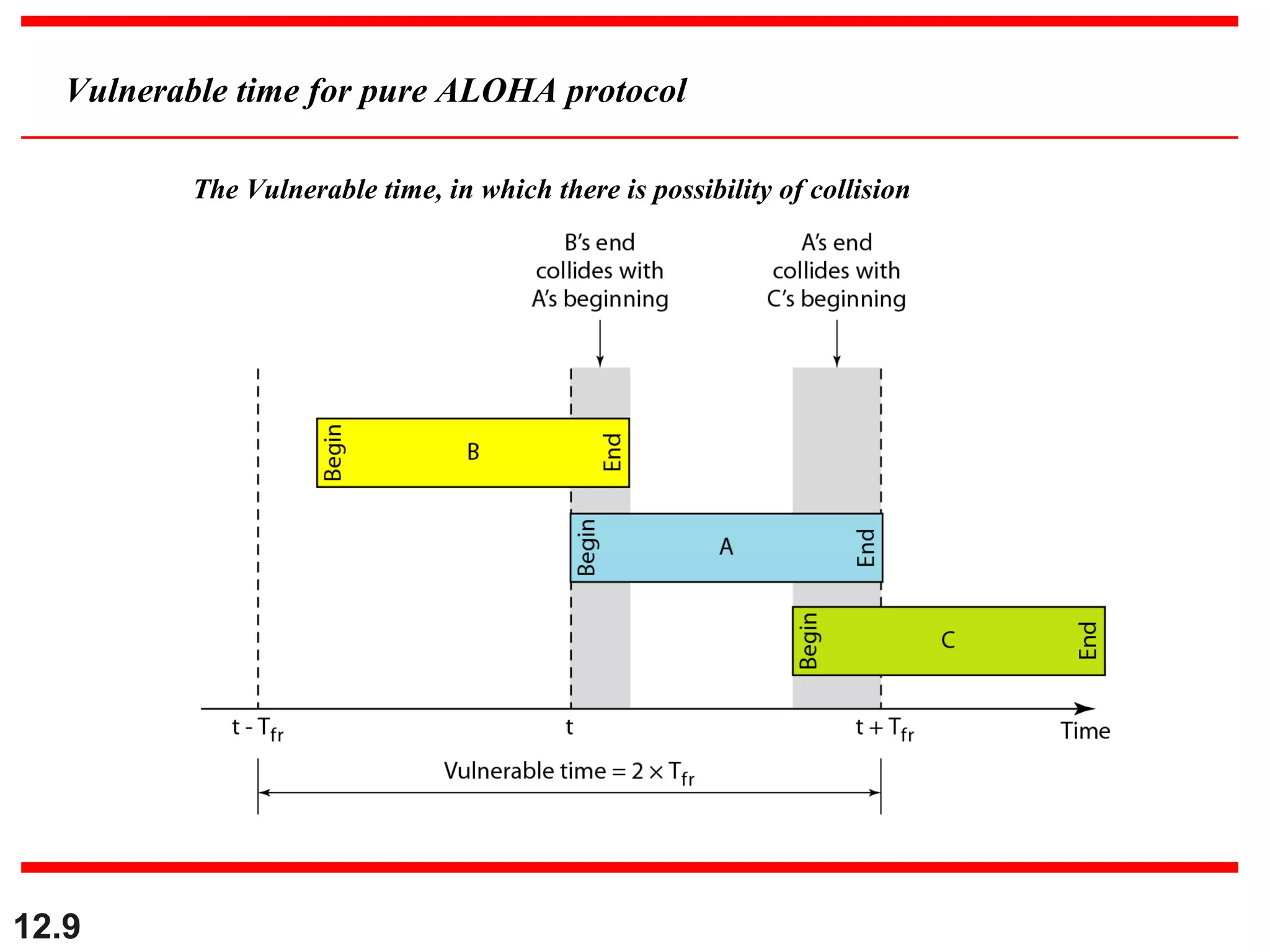
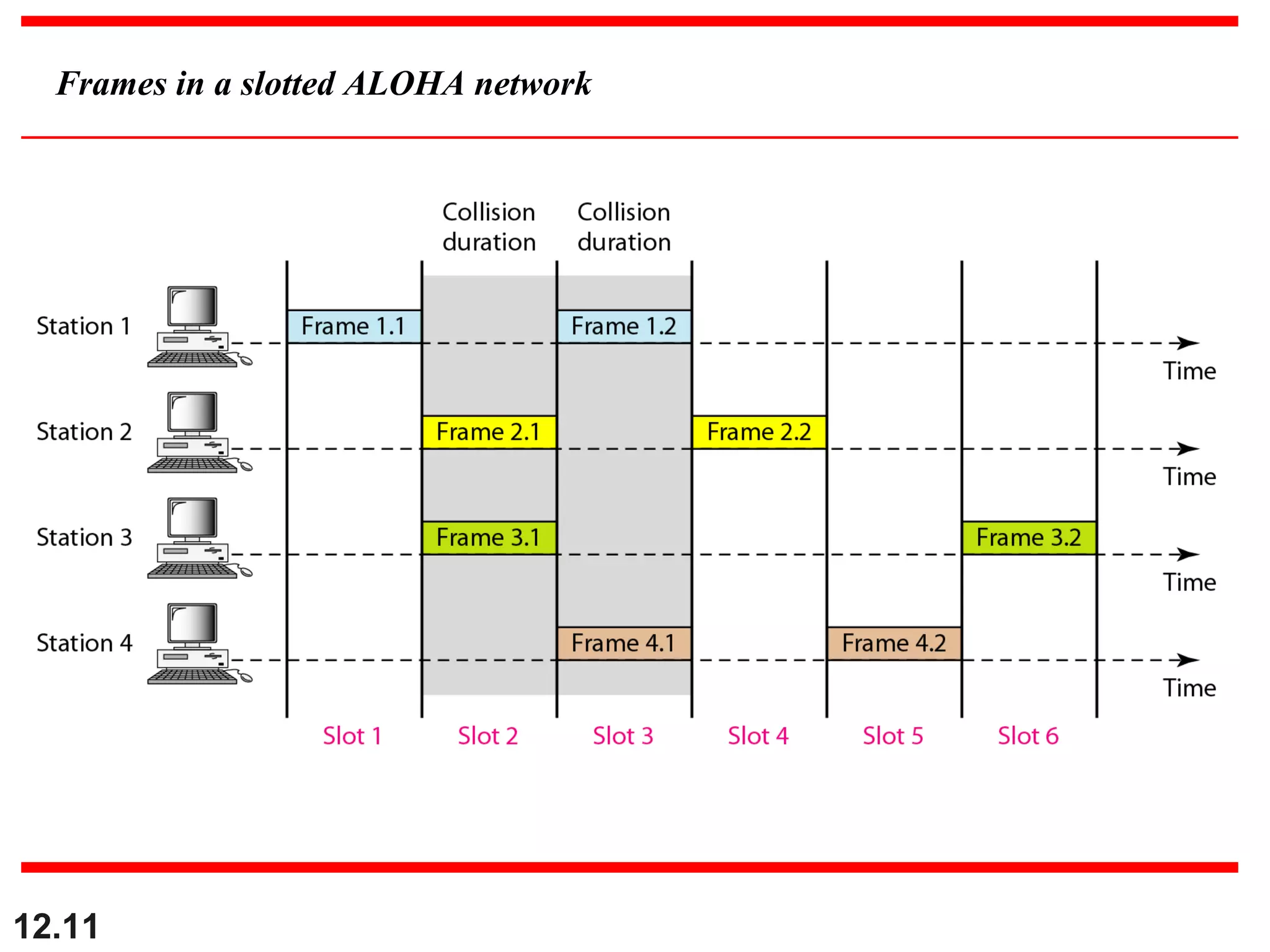
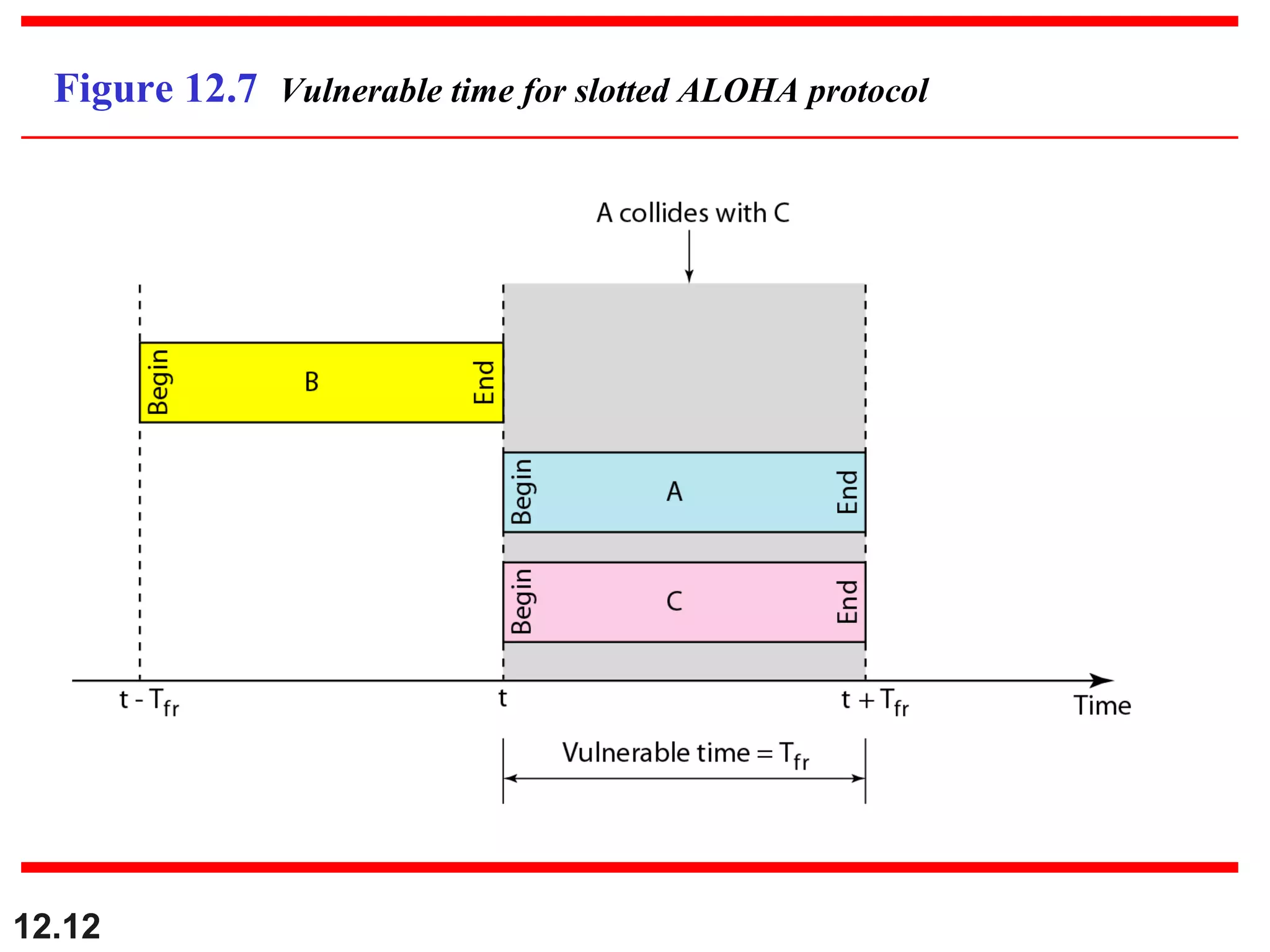
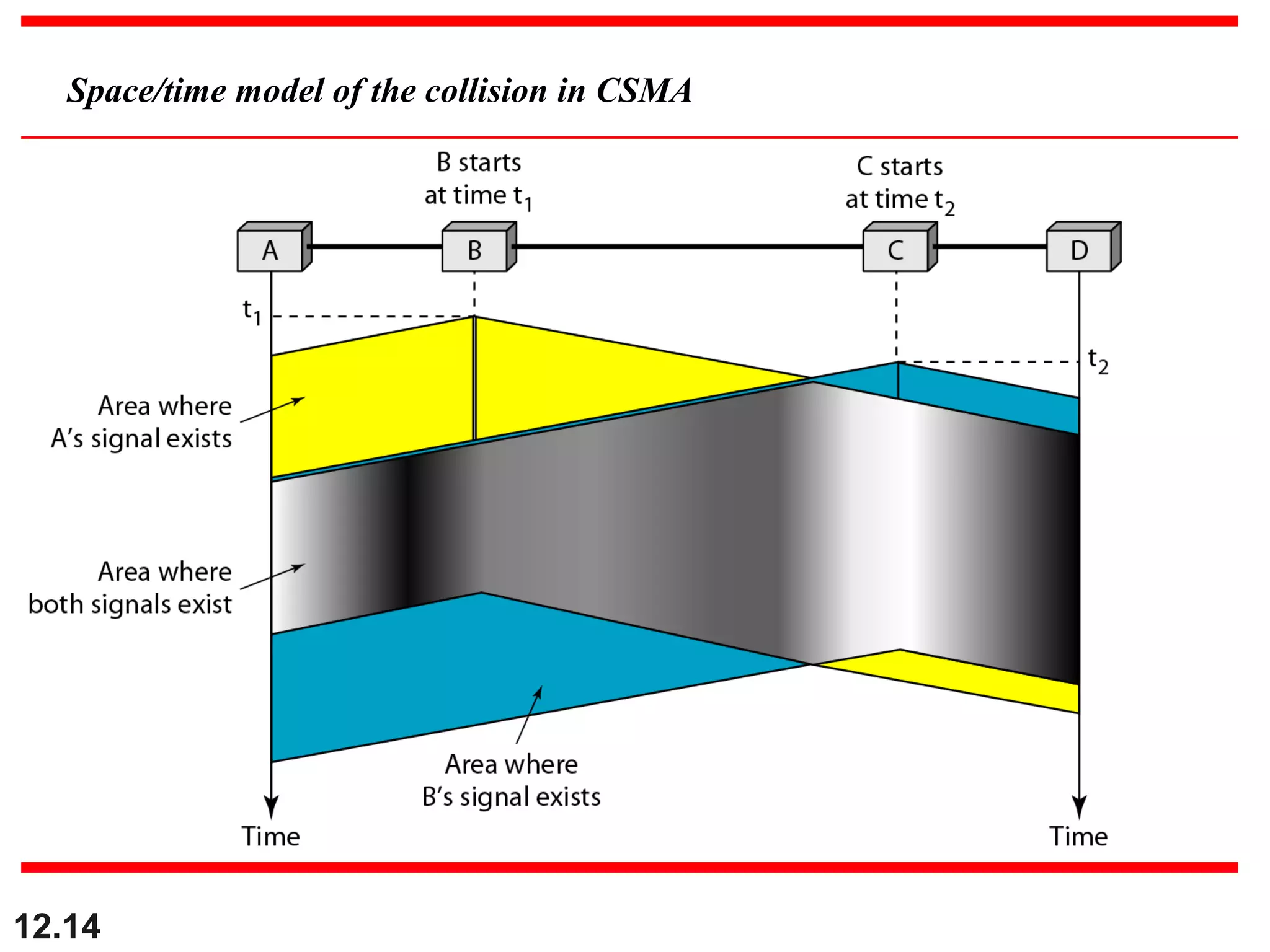
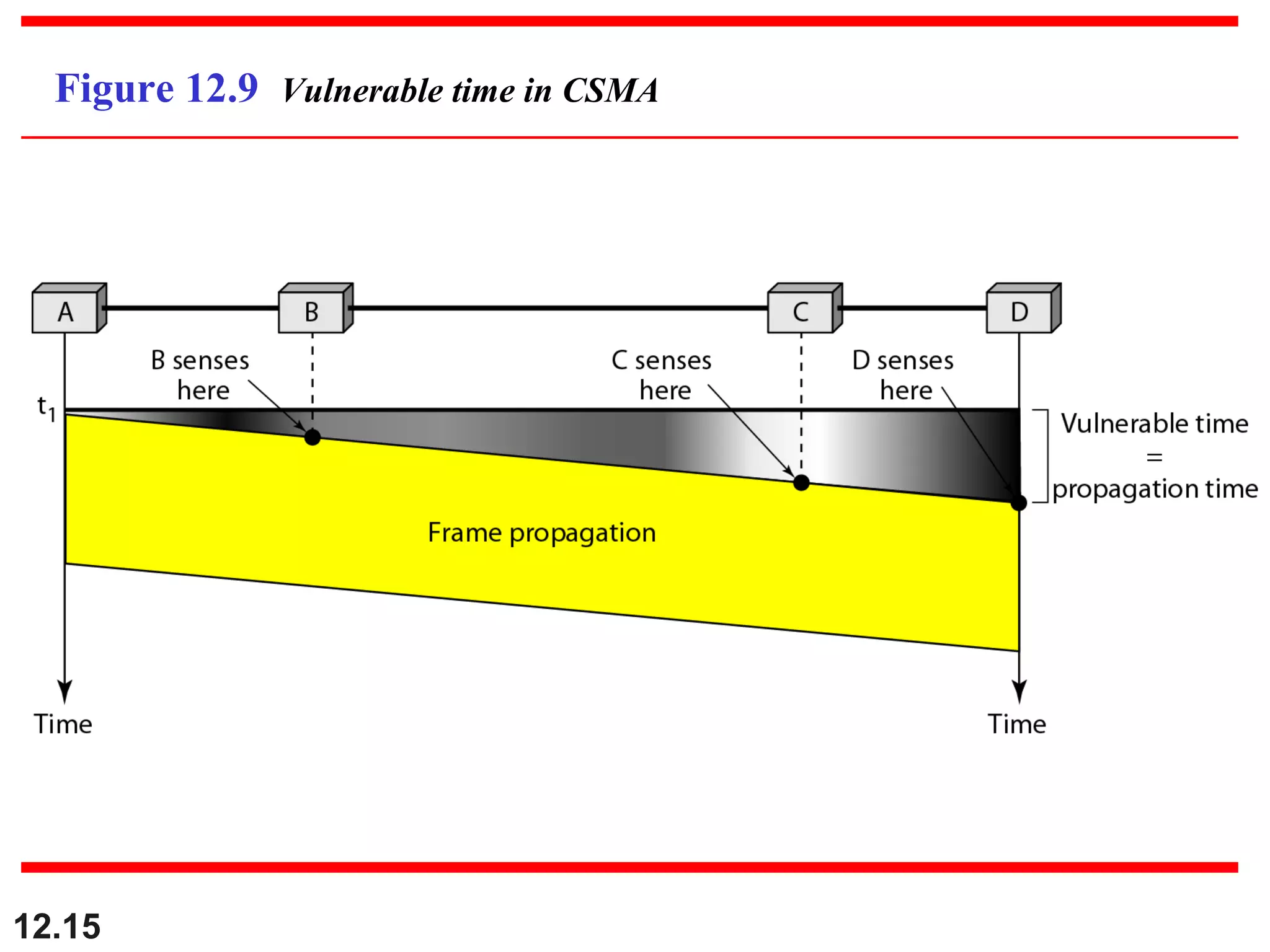
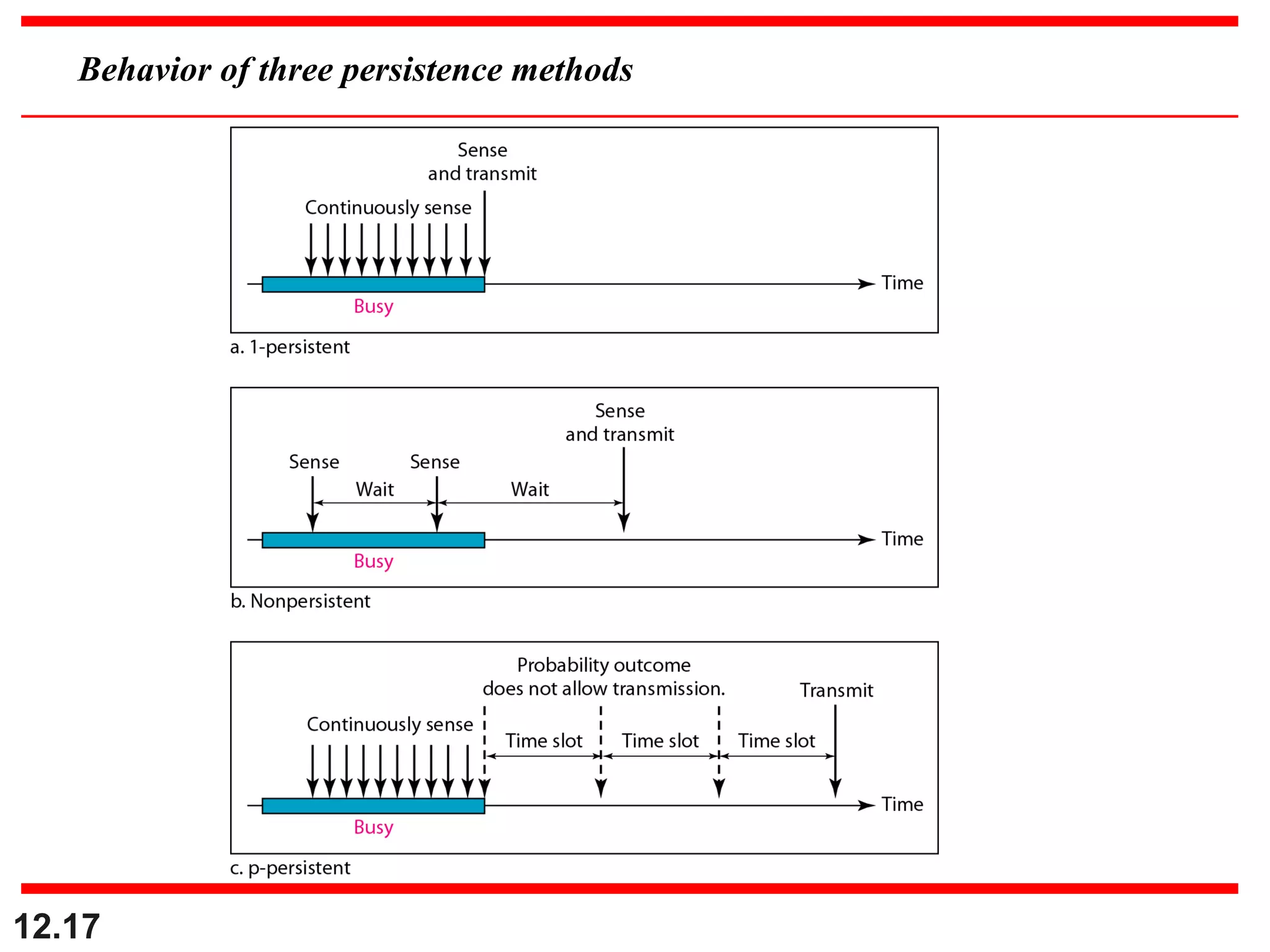
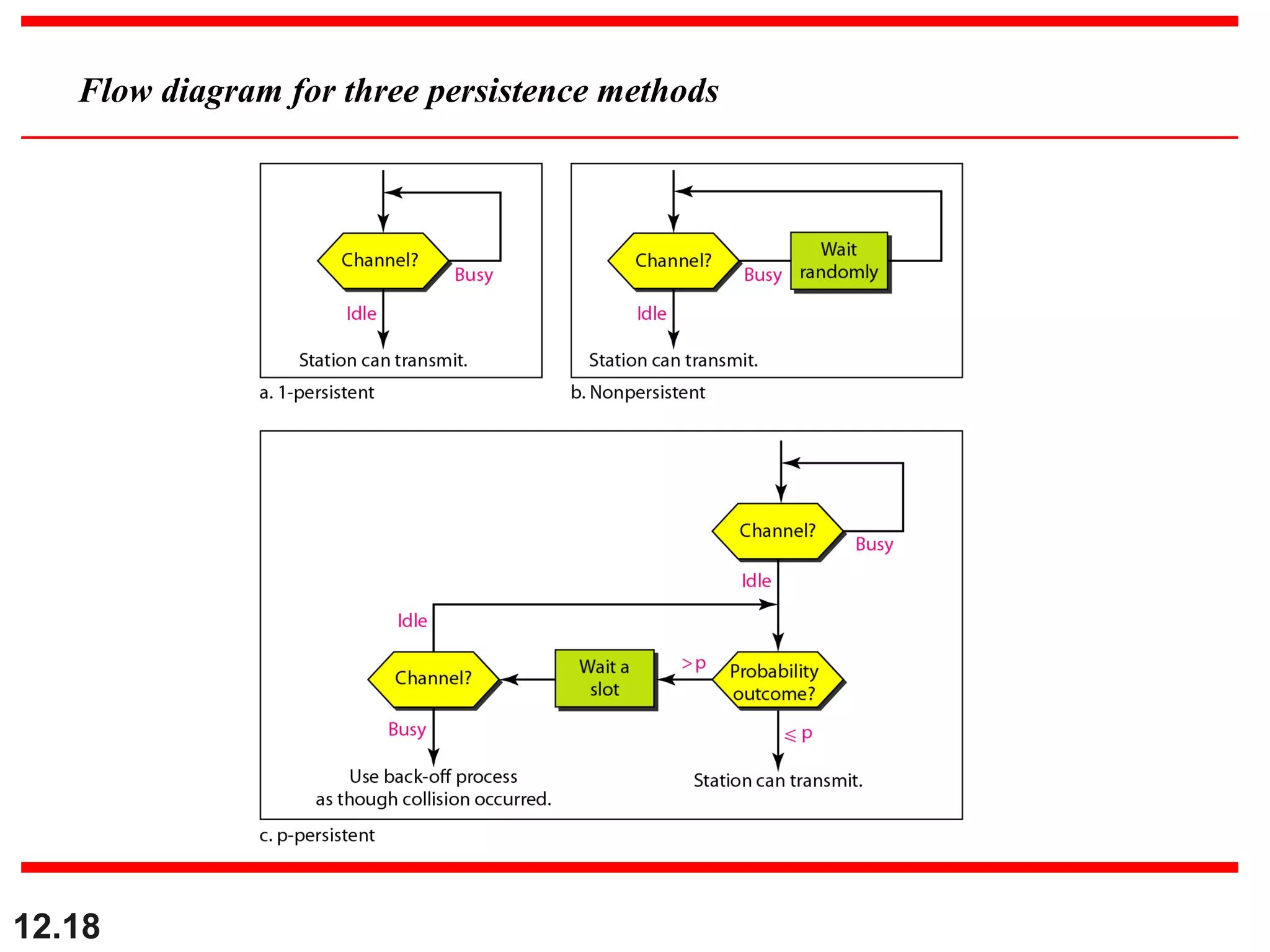
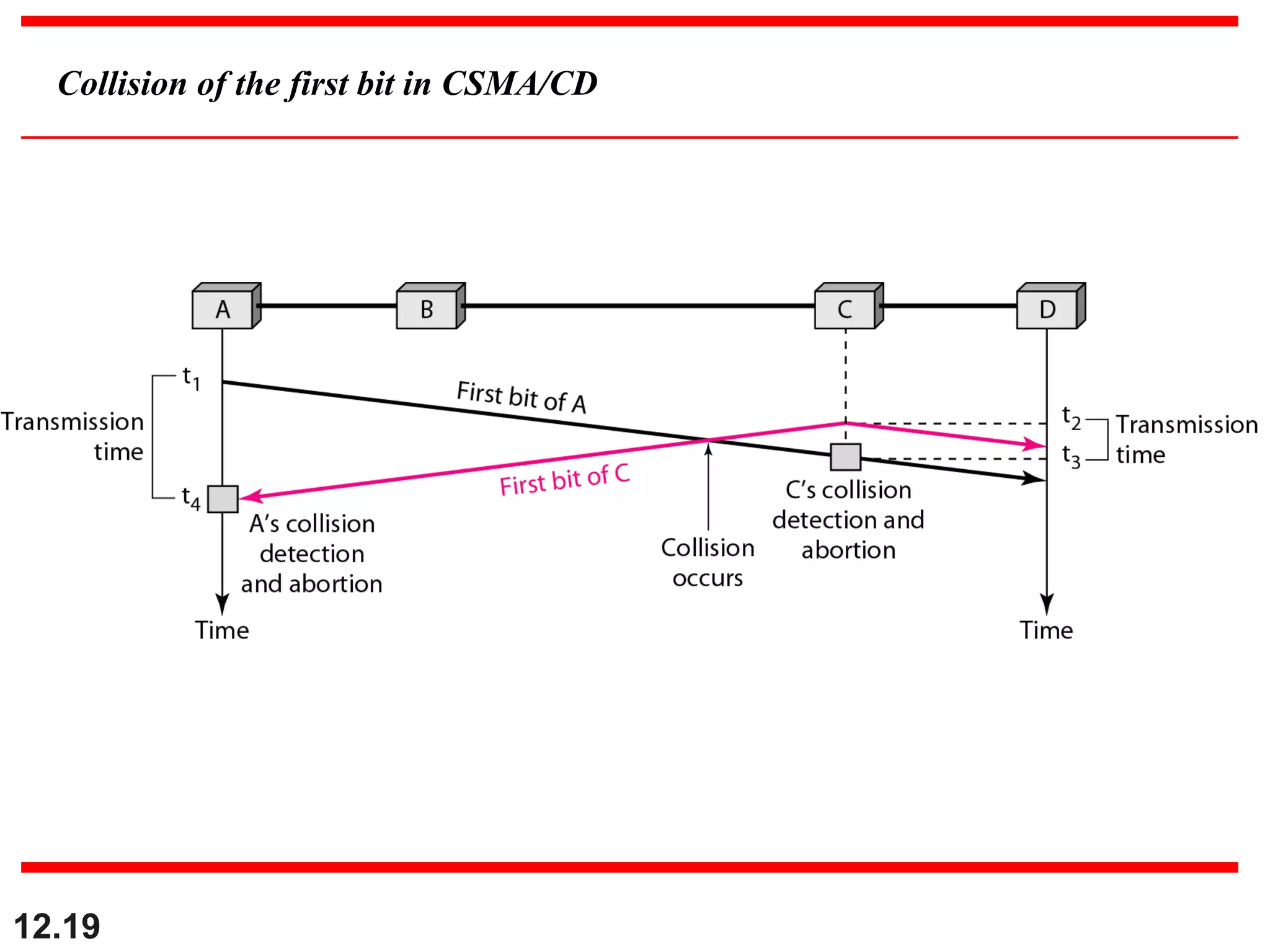
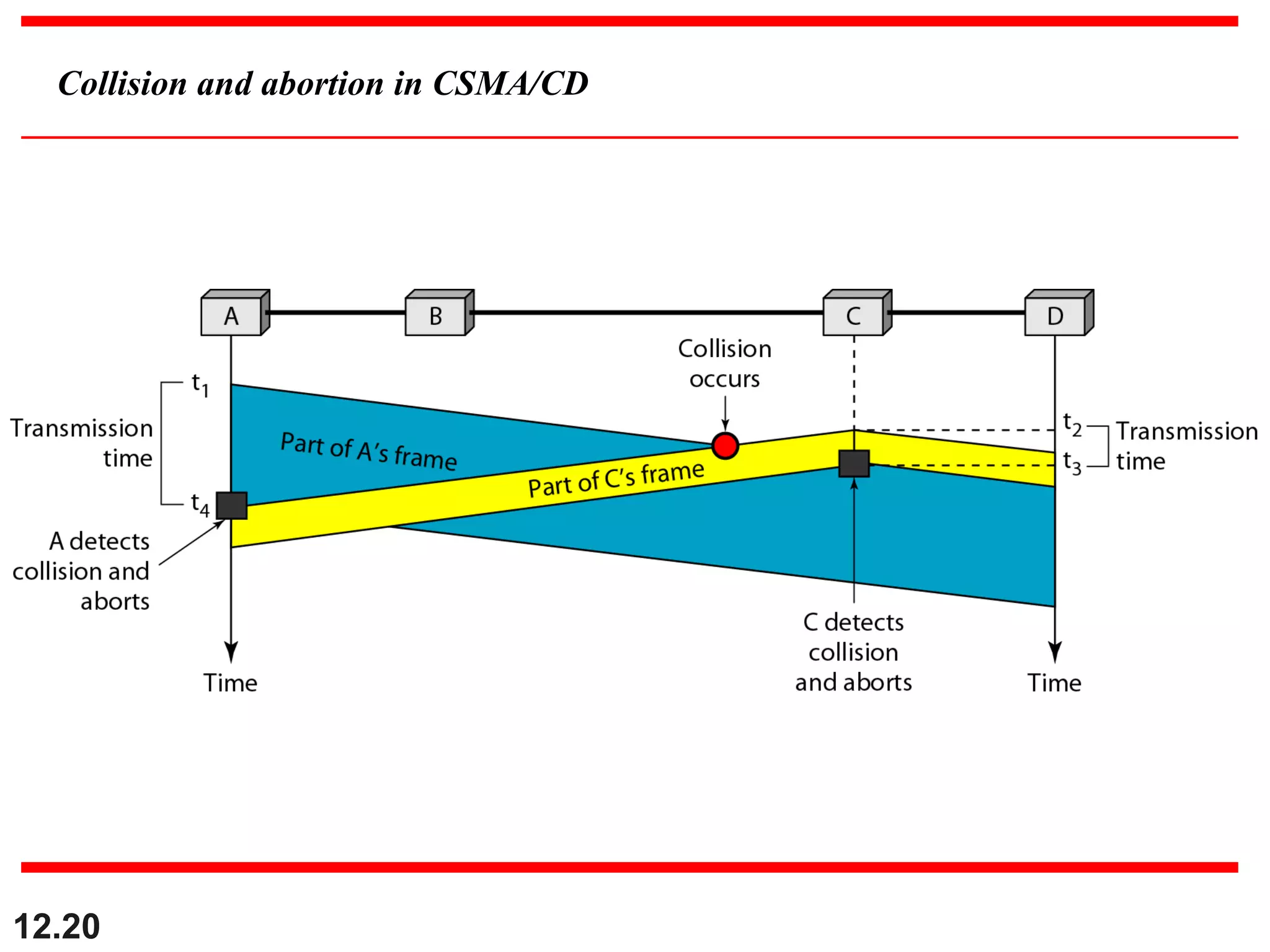
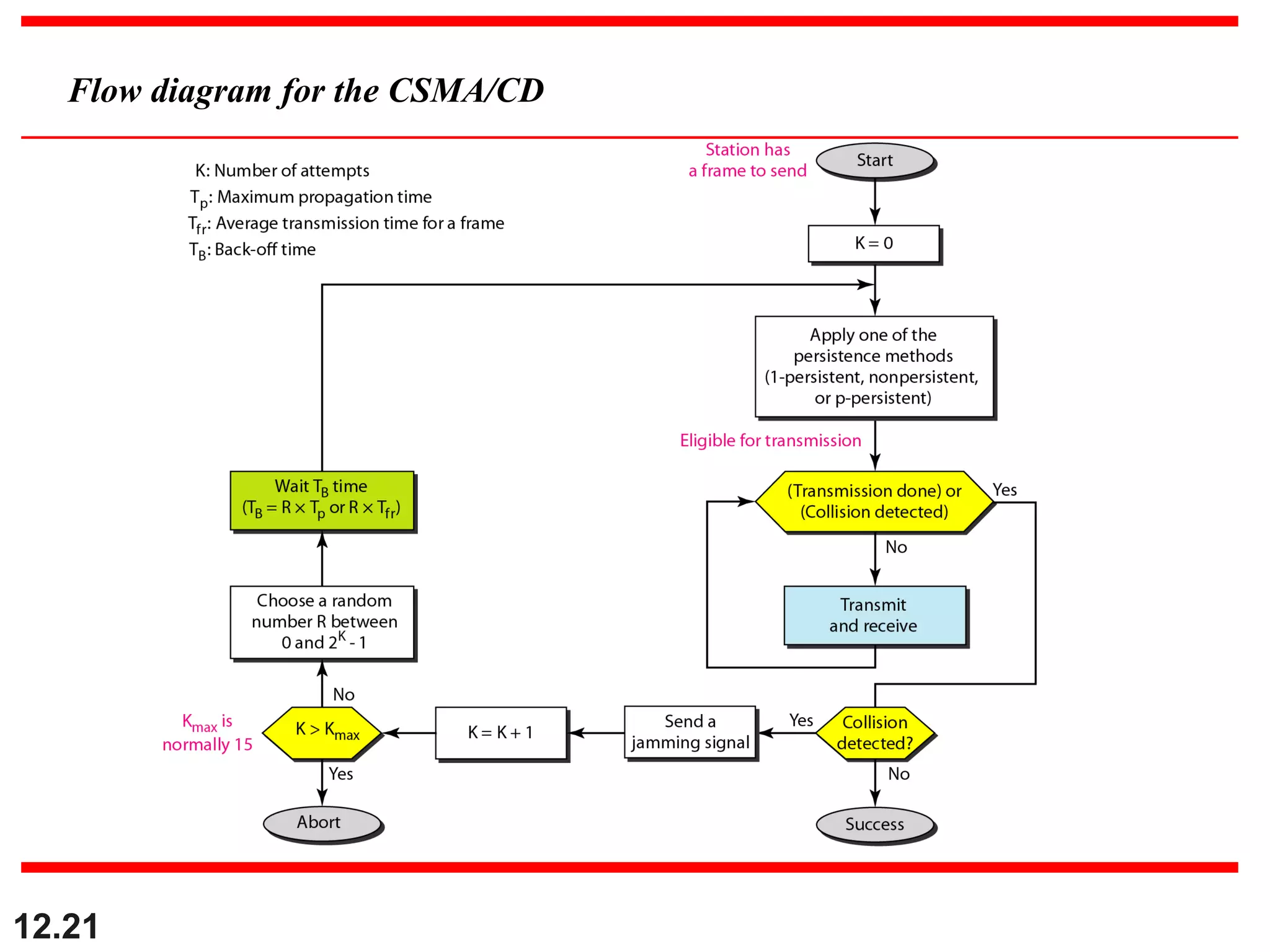
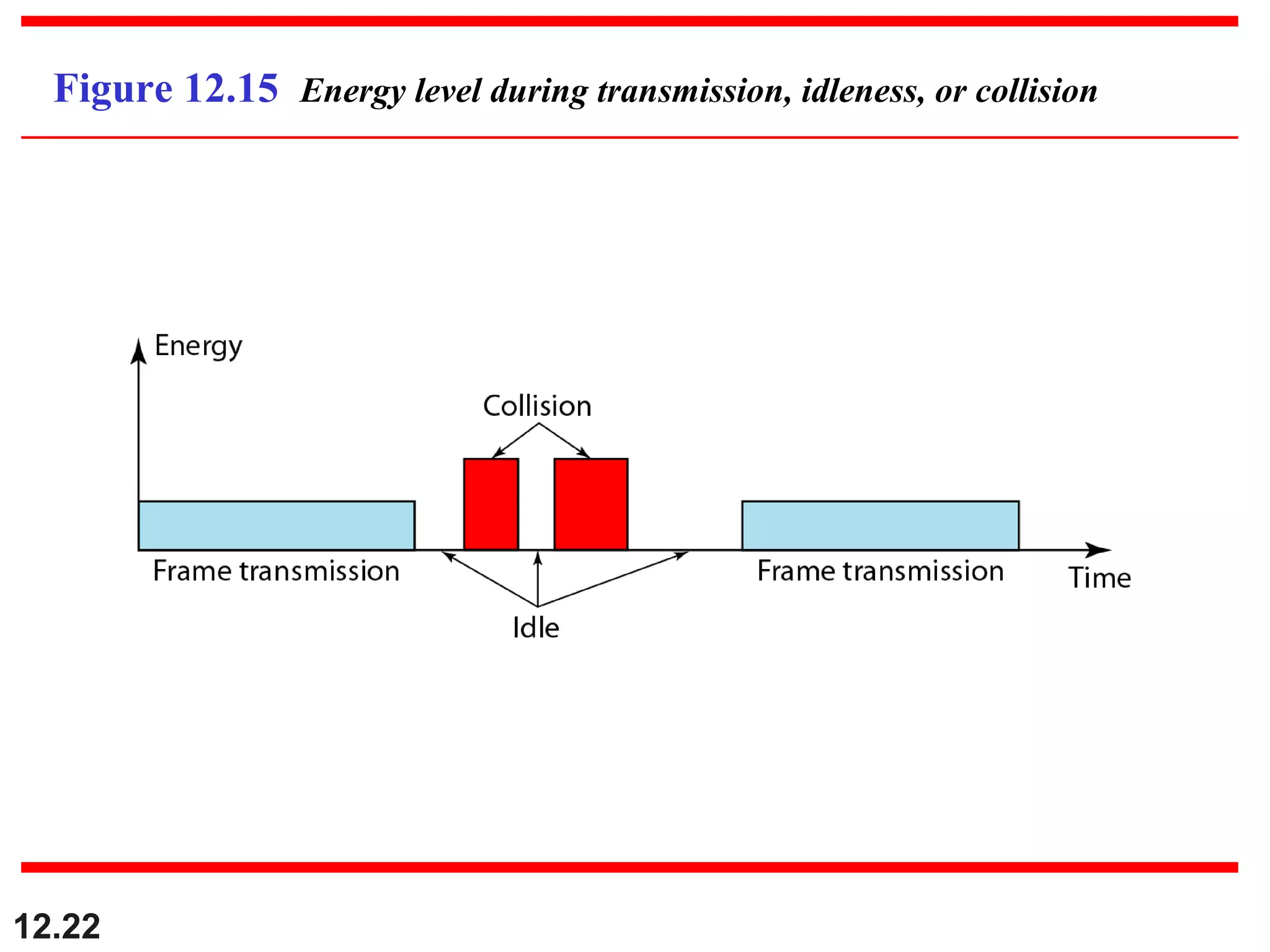
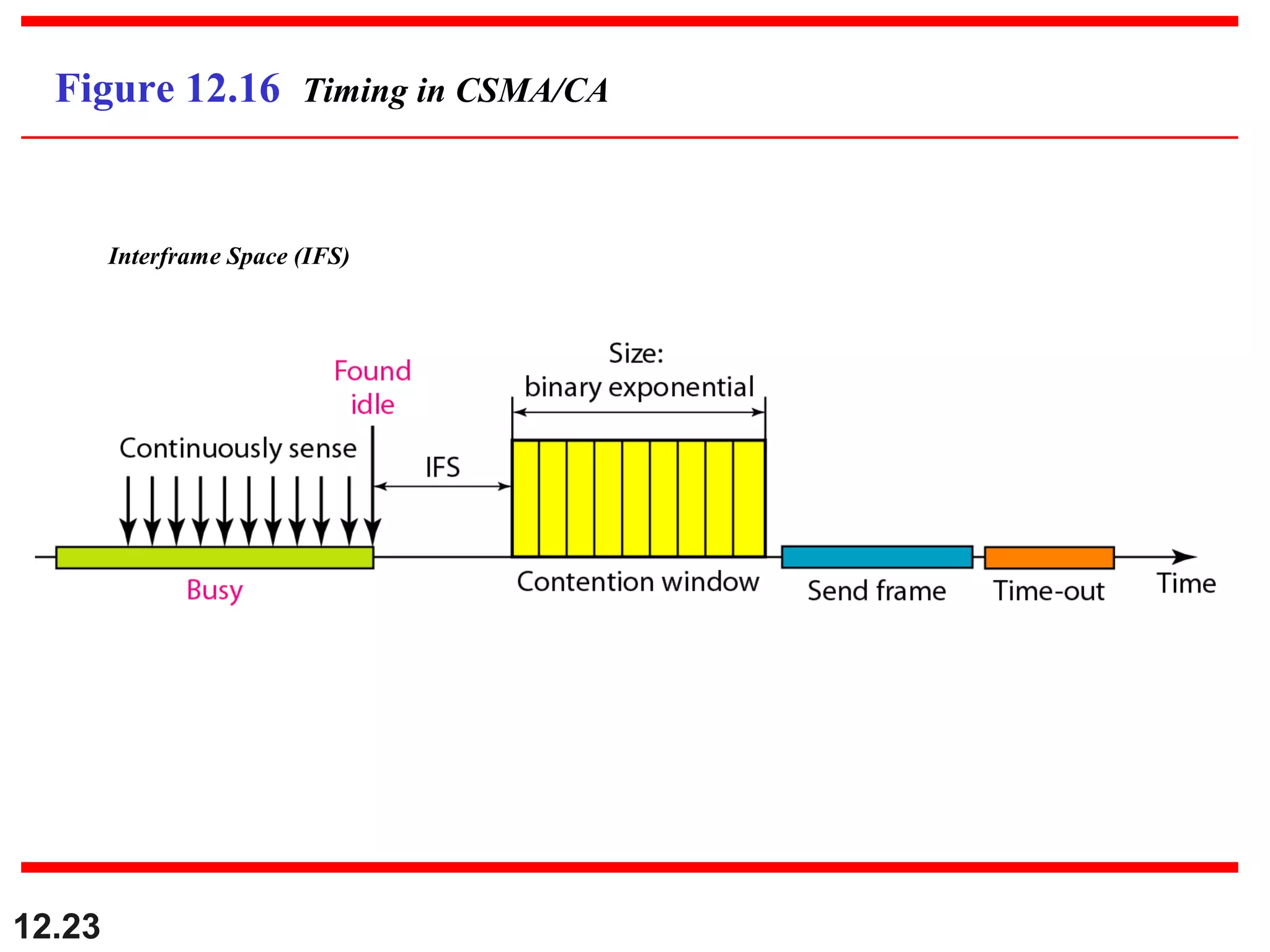
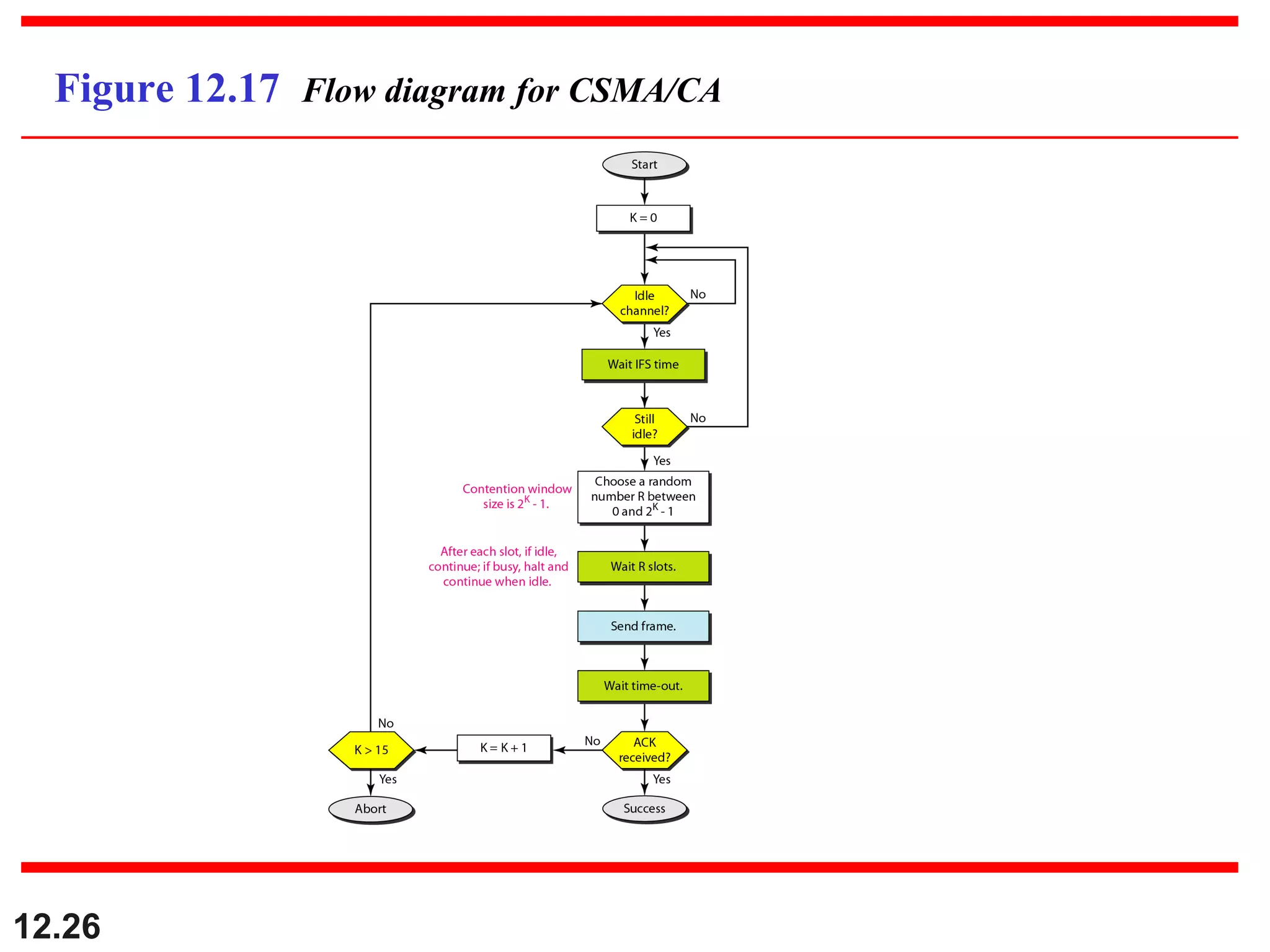
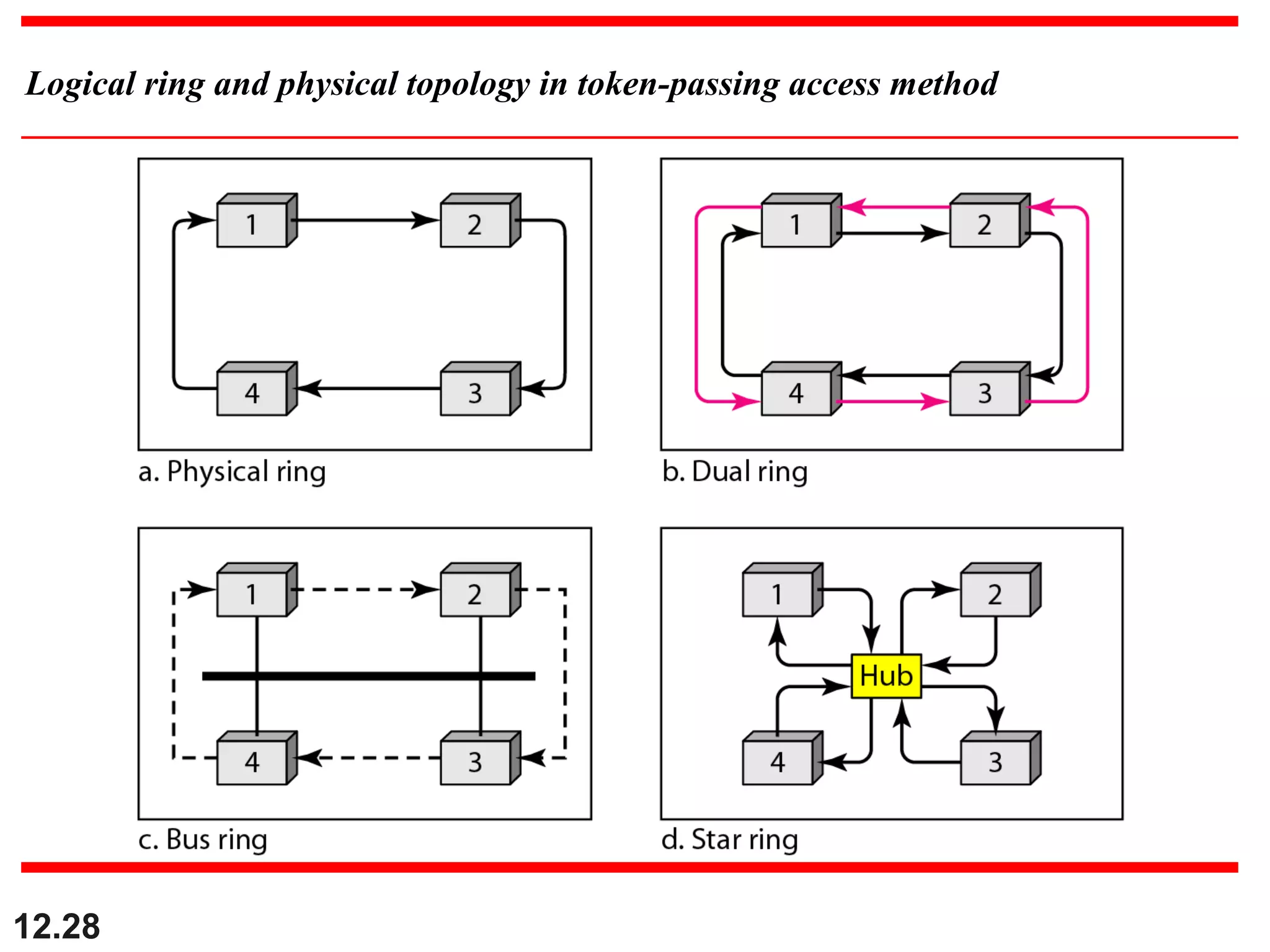
The document discusses random access protocols for wireless networks including pure ALOHA and slotted ALOHA, describing how frames are transmitted and the vulnerable time periods that can cause collisions. It also covers carrier sense multiple access (CSMA)