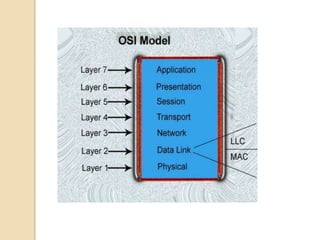
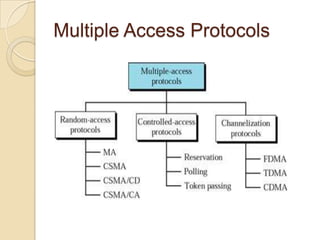
The document summarizes key aspects of the MAC (Media Access Control) layer. It discusses how the MAC layer provides MAC addressing using unique identifiers for each device and provides multiple access to allow multiple devices to share the same communication channel. It describes different multiple access protocols like random access, CSMA, polling, and channelization methods including FDMA, TDMA, and CDMA that control how devices access and share the channel.