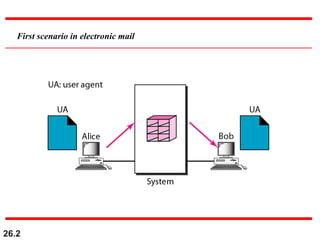
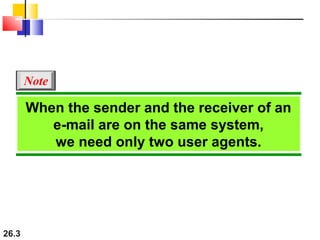
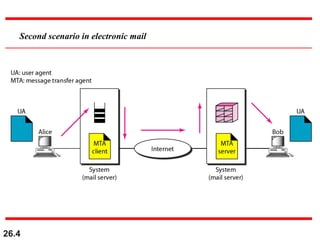
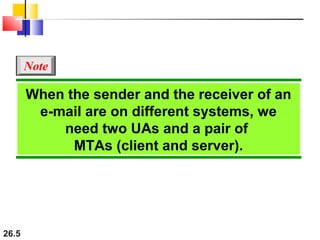
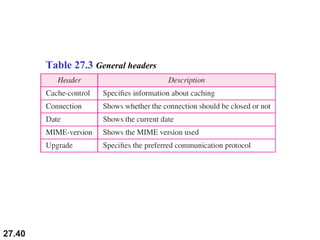
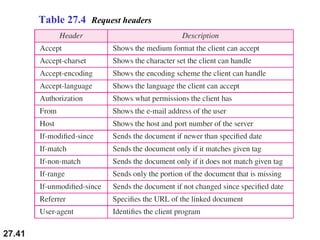
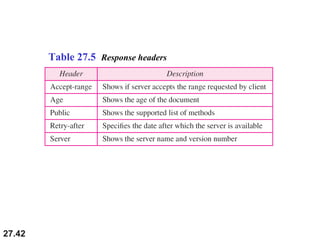
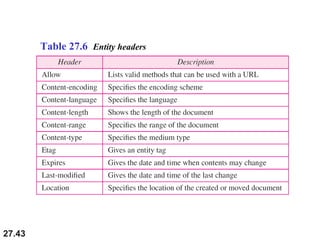
Here are explanations of the requested concepts:
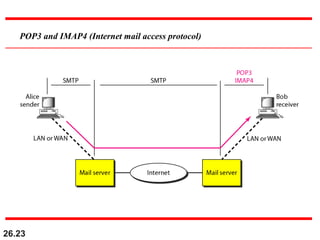
1. SMTP (Simple Mail Transfer Protocol):
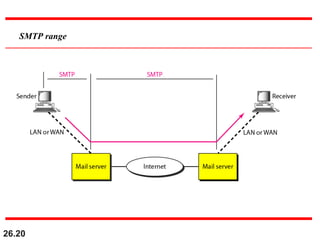
- Used for sending and receiving email messages between servers
- Works on TCP port 25
- Client (email sender) connects to SMTP server and sends the email
- SMTP server then handles delivering the email to recipient's SMTP server
2. POP (Post Office Protocol):
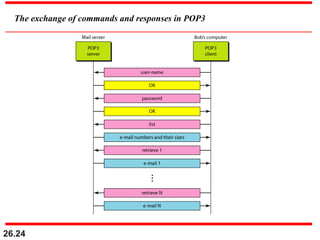
- Used for retrieving email from a remote server to a local machine
- Works on TCP port 110 (POP3)
- User must first authenticate with their username and password
- POP downloads all emails from the server to the local machine
- Emails are then deleted from the server by default
3. IMAP (Internet Message Access Protocol):