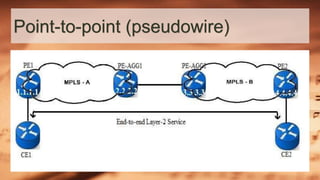
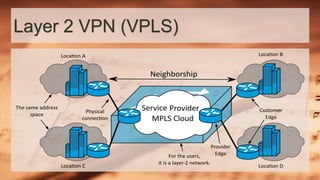
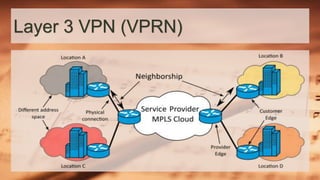
This document discusses MPLS VPN and its three main types: point-to-point VPNs using pseudowires to encapsulate traffic between two sites; layer 2 VPNs called VPLS that provide switched VLAN services across sites; and layer 3 VPNs known as VPRN that utilize VRF tables to segment routing for each customer using BGP. It describes how MPLS VPN works using CE, PE, and P routers to forward labeled packets through the provider network and pop the label at the destination PE to deliver the packet. Finally, it provides additional resources for learning more about MPLS VPN technologies.