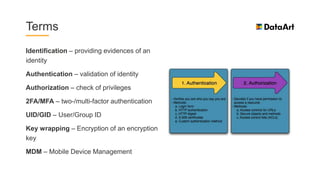
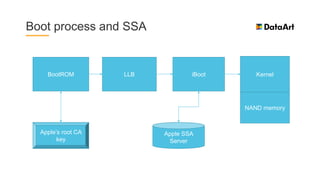
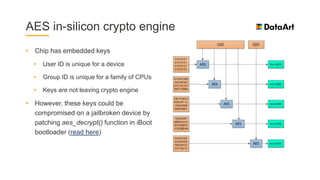
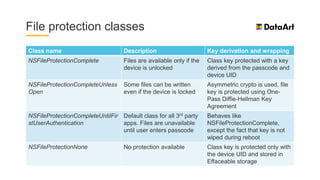
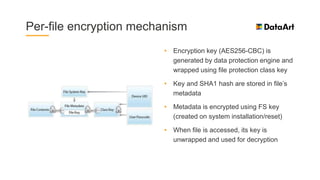
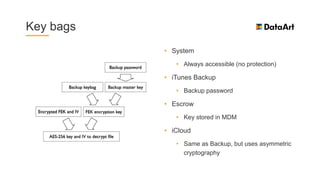
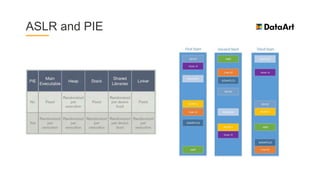
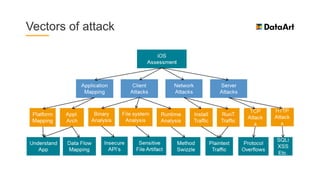
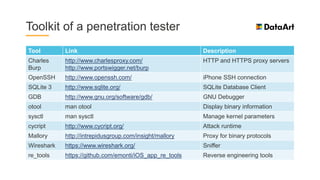
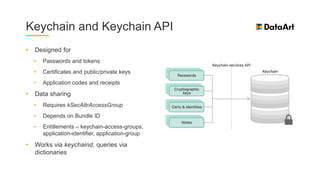
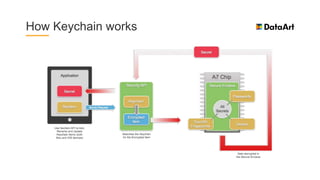
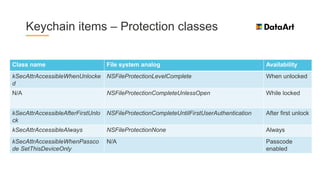
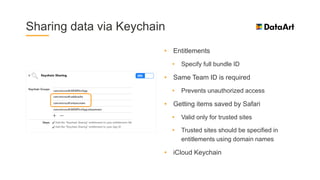
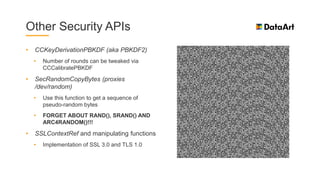
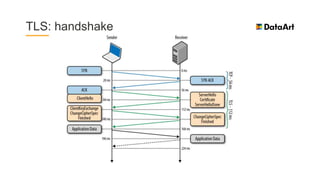
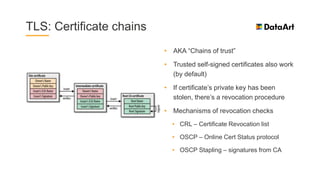
The document is a comprehensive overview of mobile security, specifically focusing on iOS development, covering topics such as security APIs, encryption methods, and the security architecture of iOS applications. It discusses principles of secure coding, best practices for managing user data, and mechanisms to protect against various types of attacks. Additionally, it provides insights into tools and recipes for enhancing iOS security during application development.