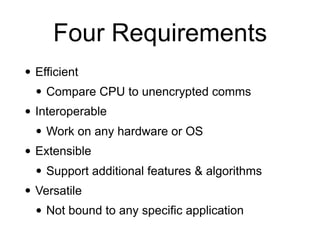
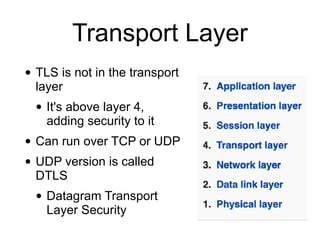
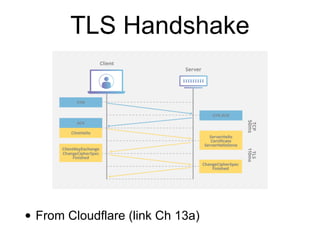
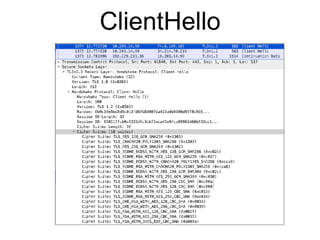
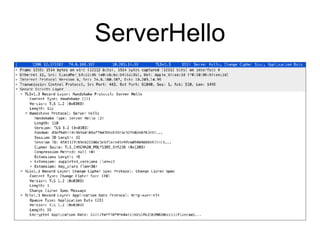
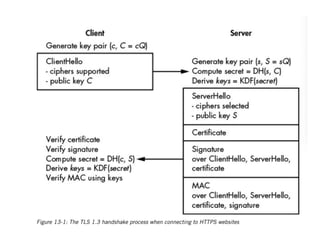
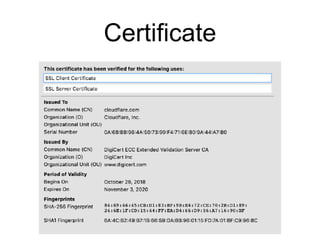
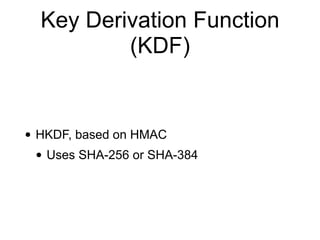
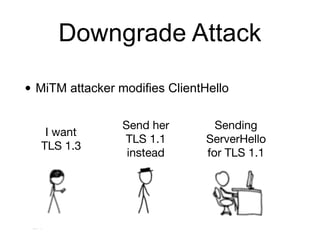
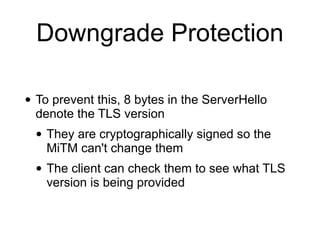
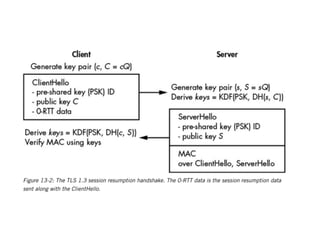
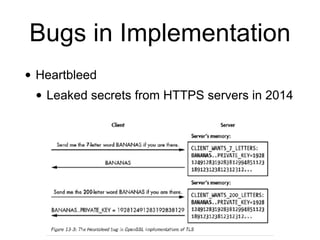
The document discusses the Transport Layer Security (TLS) protocol, its evolution from SSL, and significant improvements in TLS 1.3 over previous versions, particularly in terms of security and efficiency. It highlights features such as the removal of weak algorithms, introduction of authenticated ciphers, and enhancements like downgrade protection and session resumption. Additionally, the document addresses vulnerabilities and attacks associated with TLS, emphasizing the importance of secure communications across various applications.