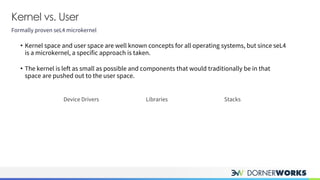
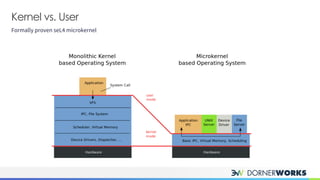
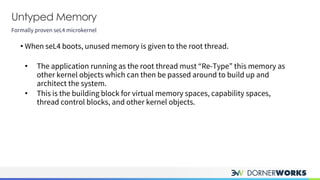
The document introduces the sel4 microkernel, emphasizing its formally proven security properties of integrity and confidentiality, making it suitable for high-security applications. It outlines the advantages of using sel4 on verified hardware and its open-source nature, which eliminates licensing costs. Additionally, the document discusses key design elements such as capabilities for resource access control and inter-process communication mechanisms, presenting sel4 as an effective solution for trustworthy systems.