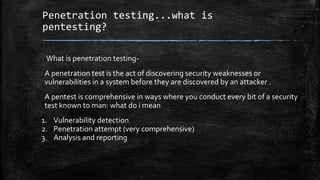
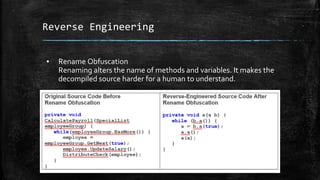
This document discusses the importance of mobile application security and penetration testing. It describes penetration testing as discovering vulnerabilities before attackers through vulnerability detection, comprehensive penetration attempts, and analysis/reporting. The document outlines static and dynamic analysis methods used for Android application security assessments. These include code review, function hooking, runtime debugging, and analyzing data at rest and in transit. It promotes understanding how applications work through reverse engineering, decompilation, and deobfuscation. The methodology uses tools like MARA, MobSF, Xposed, Frida, and BurpSuite.