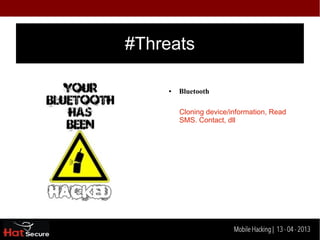
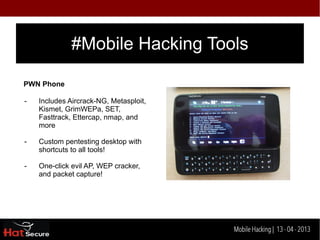
The document discusses mobile hacking and identification techniques for encrypted data. It covers mobile technology threats like Bluetooth, WiFi, cracked apps, and data storage. It then describes mobile hacking tools like PWN PAD, PWN Phone, and Linux chroot that can be used for wireless attacks, networking, and Android hacking. The conclusion recommends using firewalls, antivirus software, keeping apps up to date, avoiding cracked apps, and using security locks to help defend against these mobile threats.