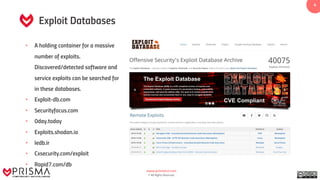
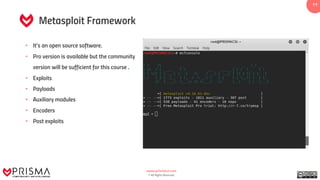
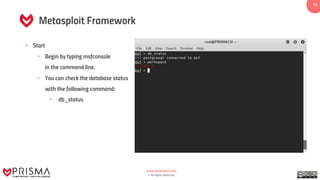
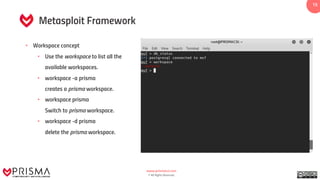
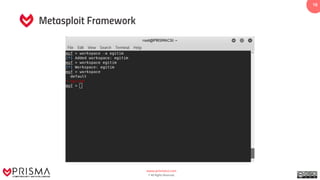
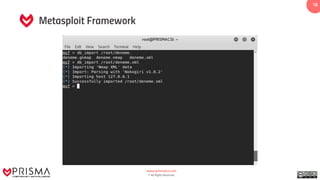
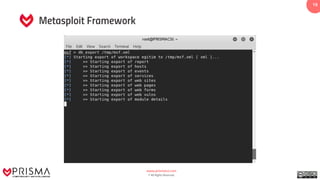
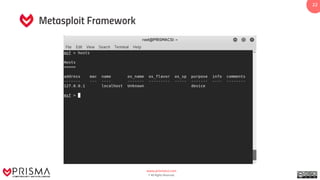
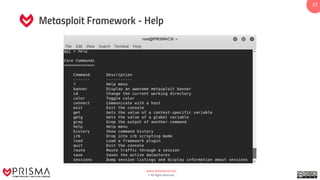
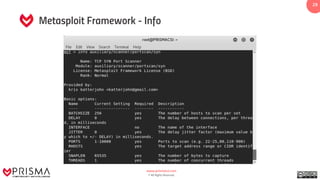
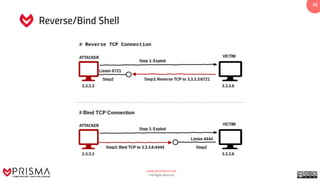
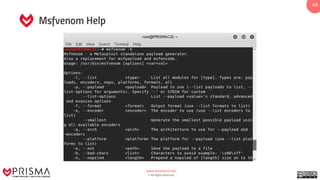
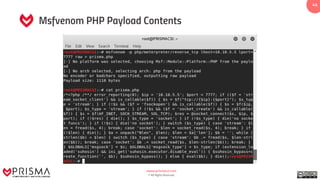
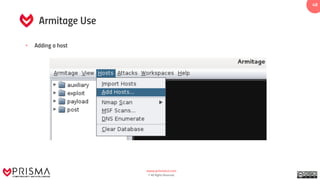
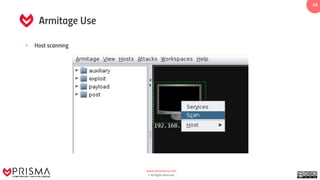
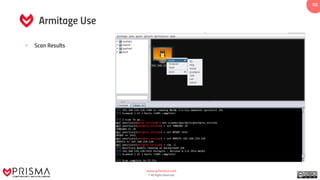
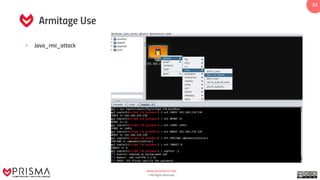
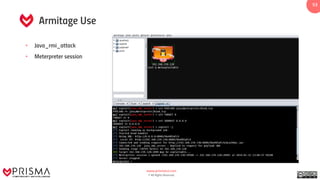
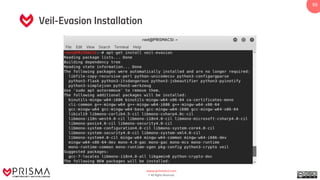
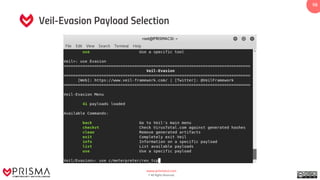
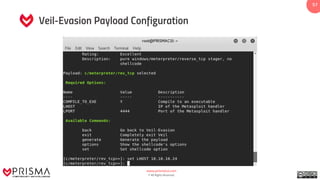
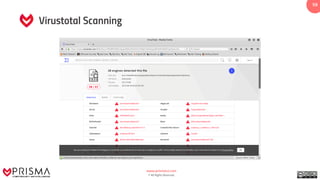
The document provides a comprehensive overview of exploitation techniques in cybersecurity, including types of exploits, exploit databases, and the usage of tools like the Metasploit framework. It covers various concepts such as payloads, exploit editing, and antivirus evasion strategies, while offering practical demonstrations for training purposes. Key features and commands related to Metasploit are detailed, aimed at equipping users with the knowledge to perform ethical hacking.