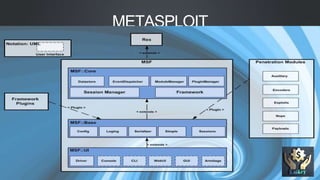
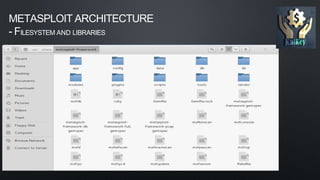
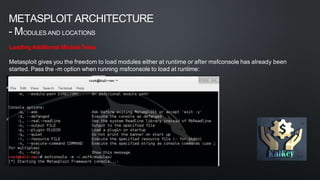
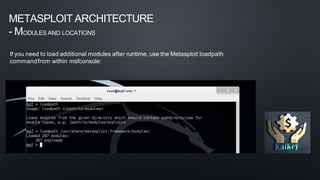
The document discusses Metasploit, an open-source penetration testing framework. It has the world's largest database of exploits and is used to develop and execute exploit code against remote targets. The document then describes Metasploit's architecture, including its filesystem structure with modules, libraries, and locations for exploits, payloads, and encoders. It also discusses Metasploit's object model and how modules are implemented as Ruby classes.