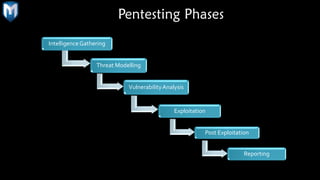
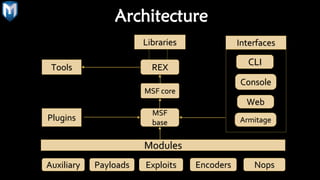
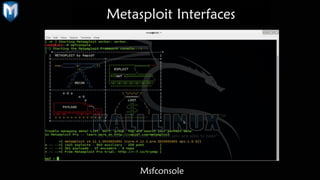
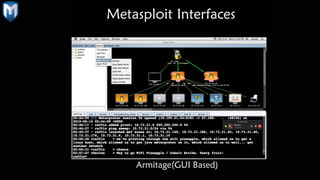
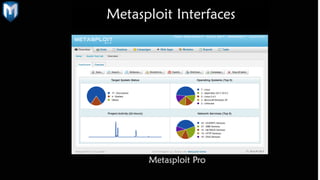
The document provides a comprehensive overview of penetration testing, focusing on the Metasploit framework as a key tool for identifying security vulnerabilities. It covers the phases of penetration testing, the advantages and disadvantages of using Metasploit, and its historical development along with future prospects. Companies invest heavily in security measures, and penetration testing is highlighted as an essential strategy to protect against potential security breaches.