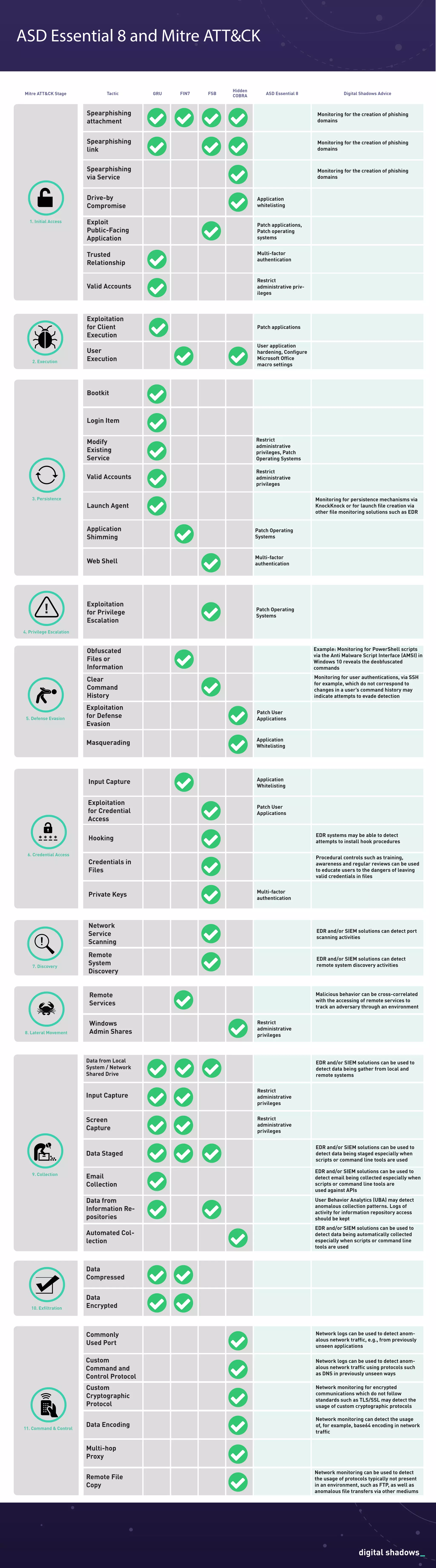
The document outlines various tactics and techniques involved in cyber threats, categorized using the MITRE ATT&CK framework. It emphasizes methods of initial access, credential access, privilege escalation, and data exfiltration, along with preventive measures such as application whitelisting, multi-factor authentication, and user training. Additionally, it highlights the importance of monitoring tools like EDR and SIEM in detecting threats and malicious behavior within systems.