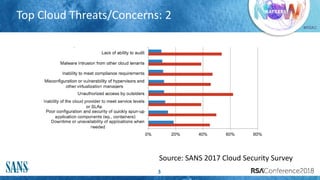
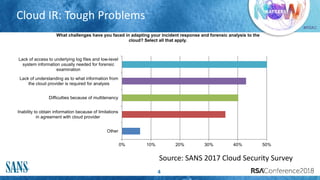
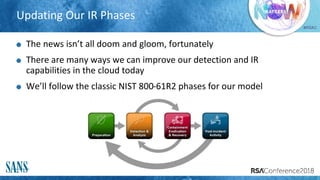
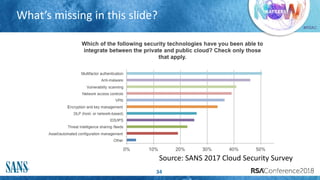
The document discusses challenges and strategies for incident response (IR) in cloud environments, highlighting issues like lack of visibility and event data. It outlines the importance of gathering information from cloud service providers and implementing effective detection and analysis methods. Additionally, it offers guidelines for forensic investigation and emphasizes the need for automation in future IR processes.