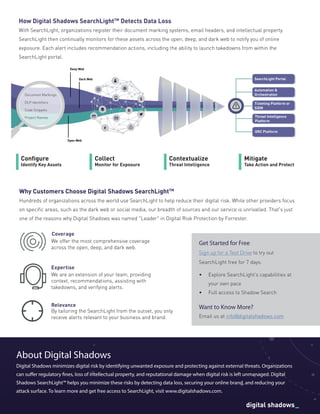
Digital Shadows provides a data loss detection service called SearchLight that identifies when sensitive company information has been exposed online. SearchLight monitors the open, deep and dark web to detect exposed employee credentials, confidential documents, intellectual property and customer data. It then notifies customers and provides recommendations to mitigate risks. SearchLight is an effective solution because it offers comprehensive coverage across different parts of the web and helps customers take action to remove exposed data.