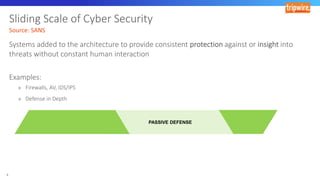
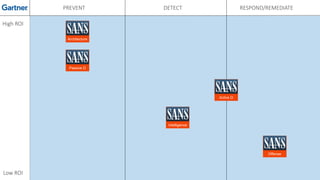
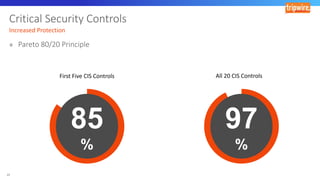
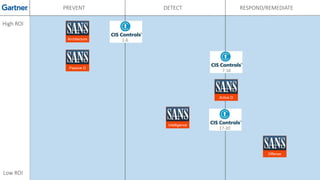
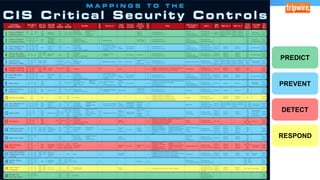
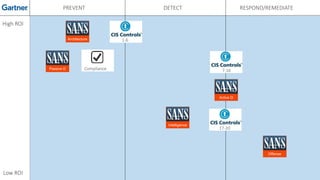
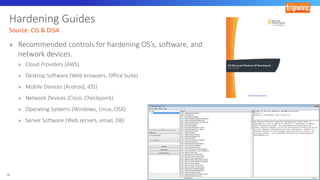
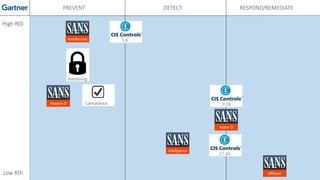
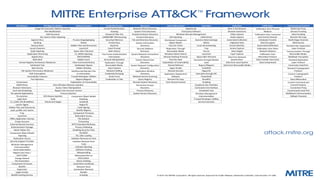
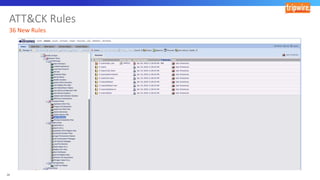
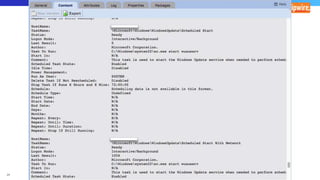
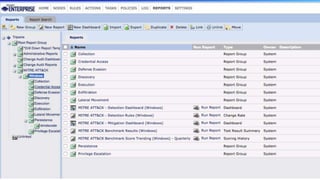
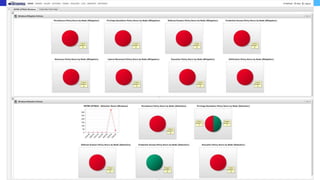
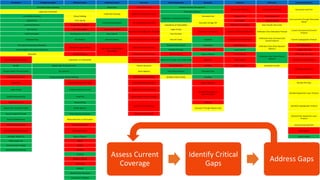
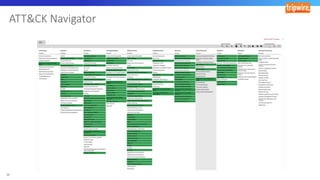
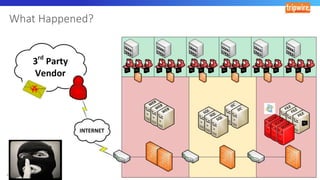
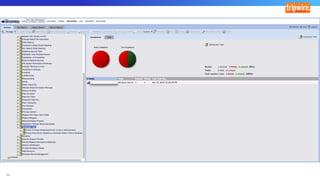
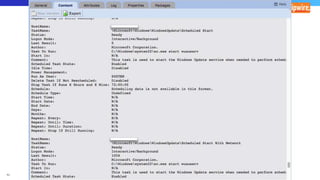
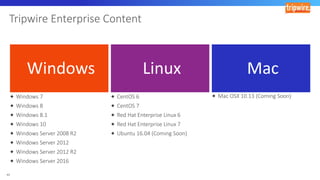
The document discusses various techniques and tactics associated with the MITRE ATT&CK framework, focusing on offensive and defensive strategies for cybersecurity. It highlights methods of credential access, execution, exfiltration, and persistence, along with defense evasion techniques and system discovery tactics employed by attackers. Additionally, it suggests assessing current security measures and addressing coverage gaps by utilizing resources related to critical security controls.