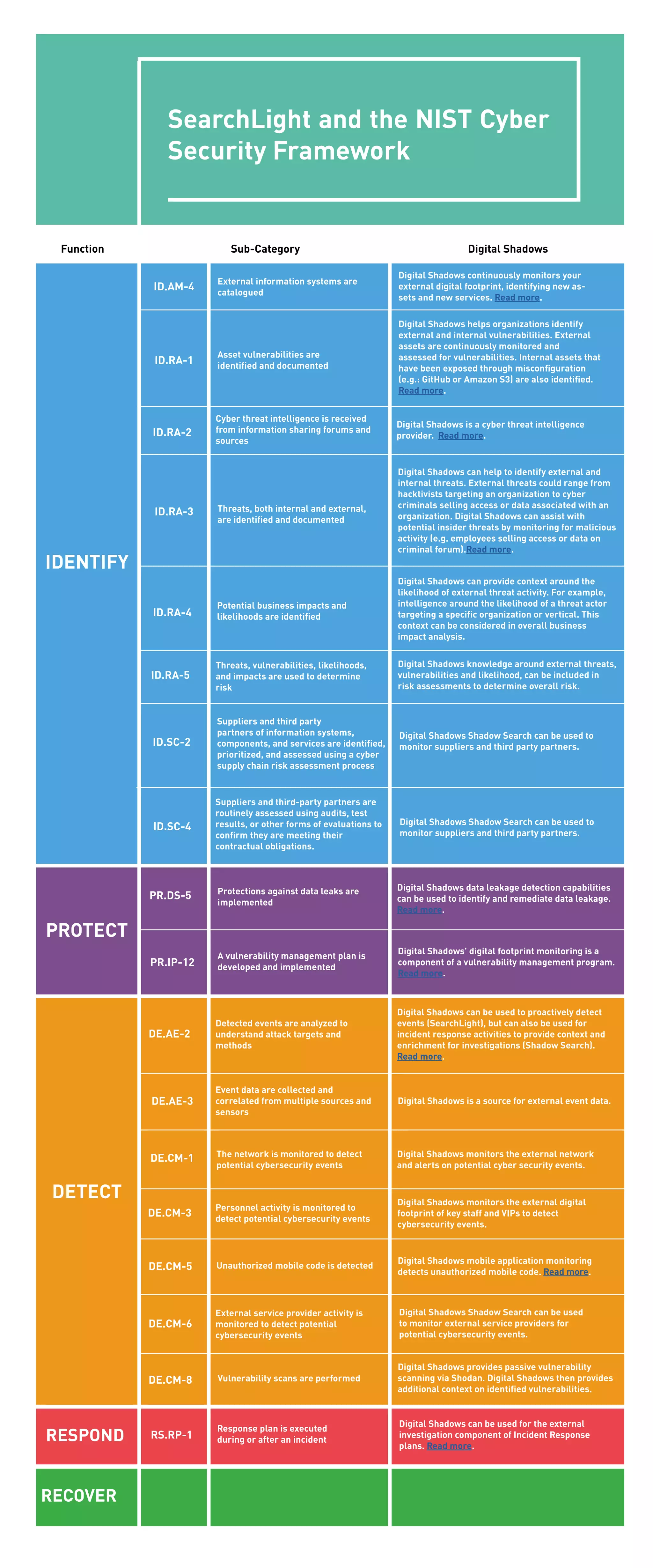
The document outlines the role of Digital Shadows in enhancing cybersecurity through continuous monitoring of external and internal vulnerabilities, detecting potential threats and events, and aiding risk assessments. It emphasizes the importance of collaboration with suppliers and third-party partners while leveraging cyber threat intelligence to mitigate risks. Digital Shadows offers various tools for proactive detection, monitoring, and incident response to safeguard organizations against cyber threats.