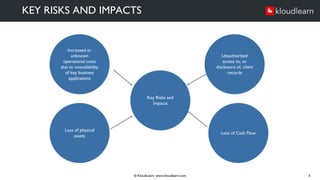
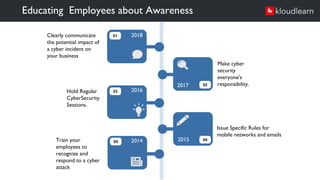
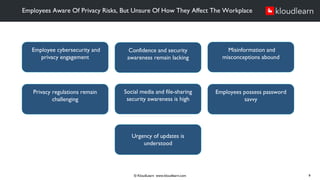
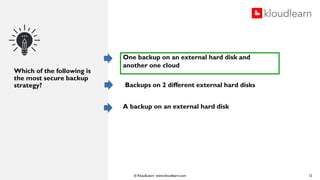
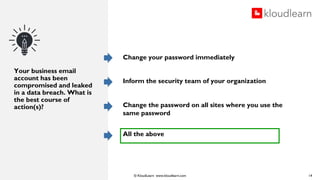
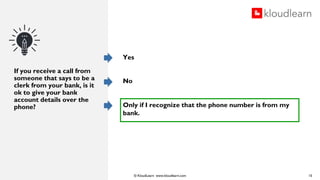
The document details an online course aimed at improving employee awareness of cyber security, emphasizing the need for training and clear corporate security policies. It highlights the current understanding and gaps in knowledge among employees, along with the importance of updated directives and effective communication of security practices. Key recommendations include regular training sessions, clear do's and don'ts, and fostering a culture of security responsibility within the organization.